Item-Level Targeting Controls
For
each target item or group of items that you create, the result will be
a returned value of true or false. If you choose to include multiple
targeting items in one decision, you must use the logical operators,
AND or OR, to combine the items so that a final decision can be made
from the target item suite. All of the items will be considered with
the logical operators that you configure. The final result of all items
and logical operations together will be a single true or false.
To change whether an item uses an AND or an OR, follow these steps from within the Targeting Editor:
1. | Select the item from the list of selected items.
|
2. | Right-click the item, and then click Item Options.
|
3. | Click either AND or OR.
|
You
can also include or exclude the item decision that you have configured.
This is controlled by the IS or IS NOT configuration, which is per item
listed in the Targeting Editor. To configure this setting for an
existing item listed in the Targeting Editor, follow these steps:
1. | Select the item from the list of selected items.
|
2. | Right-click the item, and then click Item Options.
|
3. | Click either IS or IS NOT.
|
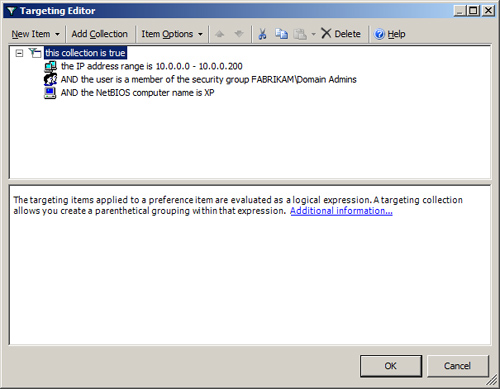
If
the list of targeting items that you need to use become too numerous
with too many logical operators, it is a best practice to use the
targeting collection item. This item allows you to create parenthetical
expressions. Like an algebra equation, the targeting collection allows
you to make decisions on items within the overall expression. Figure 21 illustrates a complex expression within the Targeting Editor.
3. Common Item-Level Targeting Scenarios
Item-level
targeting has been used in many scenarios to provide extra value to the
Group Policy Preferences settings, as well as for unique environments.
Common scenarios include the following.
Desktop vs. Laptop
There
may be times when you want to delineate your laptops from your
desktops. You may want to do this for many reasons, such as to
configure VPN connections for mobile users, configure printers
differently between the two types of computers, and many more
possibilities. You can accomplish this easily by using the Portable
Computer targeting item. If you were to create an environment variable
using the Environment Variable item, you could affix to each an easy
way of querying the computer type, which could be used by any of the
targeting items.
Computer Performance
Depending
on the setting that you are delivering or making on the target
computer, faster computers might need one setting level and slower
computers a different setting level. Another factor might be disk
space—some settings could be applied to only computers that meet
certain disk space criteria. By using the CPU Speed item and Disk Space
item, you can target each preference as required.
Operating System Targeting
With
the targeting item that allows for separation of all operating system
versions that support Group Policy Preferences, you can now use the
Operating System item to target any Group Policy Preferences setting to
the operating system that you want. This is especially useful for
settings and features that are valid only on certain operating systems.
Drive Mapping Security
Many
companies have financial or human resources applications that access
private data. The data is usually located on the network, but some
users have access to the drive mapping even though they do not have the
application installed. Instead of allowing all users in a department to
have a mapped drive to a private data share, you can use the File Match
item or the Registry Match item to narrow the scope of users who
receive the drive mapping to the private data. The File Match item and
the Registry Match item can target the installation files and registry
values to ensure that the application is installed.