By default, every user and computer in the
scope of management of a GPO will receive the settings contained in the
GPO. Before the availability of item-level targeting, there were a few
options available to alter this default application of GPO settings.
These options include:
All of these options for
altering the default processing and inheritance of GPO settings affect,
at a minimum, all of the settings in a GPO. This global control of the
settings within a GPO is hard to work with, hard to manage, and very
difficult to troubleshoot.
Group Policy
Preferences offers item-level targeting, which provides a highly
granular filtering capability that is nothing like the other options
that alter the default processing of GPO settings. Item-level targeting
provides many benefits over the other options, including:
Item-level targeting for each setting
Combining of Boolean item filters, to ensure that Group Policy Preferences settings target the correct user or computer
Over 25 targeting items to choose from
API-based foundation, which provides fast and efficient application of the Group Policy Preferences settings
Every
Group Policy Preferences setting can be configured with item-level
targeting. To configure the item-level targeting for a Group Policy
Preferences setting, you must access the Common tab for the setting by
following these steps:
1. | From the GPMC, edit a GPO that contains a Group Policy Preferences setting.
|
2. | Right-click any configured Group Policy Preferences setting, and then click Properties.
|
3. | In the Properties dialog box, select the Common tab.
|
4. | Select the Item-Level Targeting check box, and then click Targeting.
|
5. | The Targeting Editor appears, as shown in Figure 1.
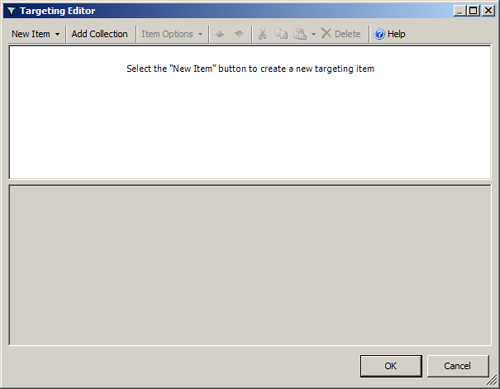
|
1. Item-Level Targeting Items
Every
Group Policy Preferences setting has the full range of item-level
targeting capabilities. Each item within the target provides the
ability to allow or deny the application of the associated setting to
the user or computer being controlled. The items within the Targeting
Editor can all be referenced by clicking the New Item menu, which
exposes the full list of items, as shown in Figure 2.
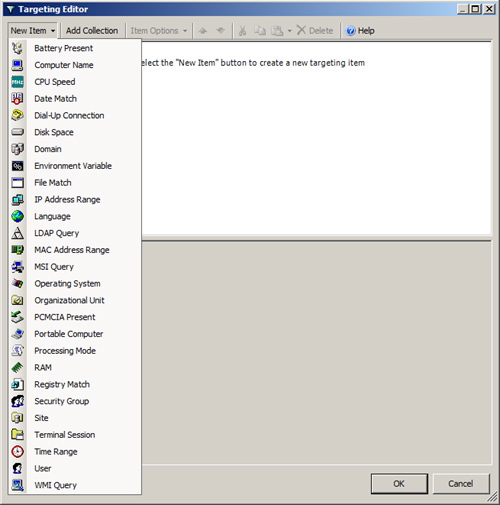
Battery Present
A
Battery Present targeting item allows a preference item to be applied
to computers or users only if one or more batteries are present in the
processing computer.
Note
If
an uninterruptible power supply (UPS) is connected to the processing
computer, a Battery Present targeting item may detect the UPS and
identify it as a battery. |
Computer Name
A Computer Name targeting item, shown in Figure 3,
allows a preference item to be applied to computers or users only if
the computer’s name matches the specified computer name in the
targeting item. The Computer Name text box accepts preference
processing variables. Press F3 to display the Select a Variable dialog
box, which lists the system-defined variables from which you can select.
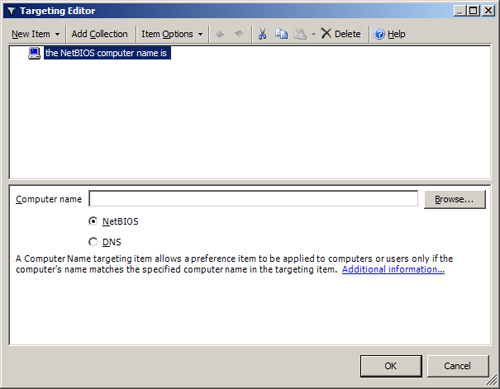
CPU Speed
A
CPU Speed targeting item allows a preference item to be applied to
computers or users only if the processing computer’s CPU speed is
greater than or equal to the value specified in the targeting item. The
MHz box accepts preference processing variables. Press F3 to display
the Select a Variable dialog box, which lists the system-defined
variables from which you can select.