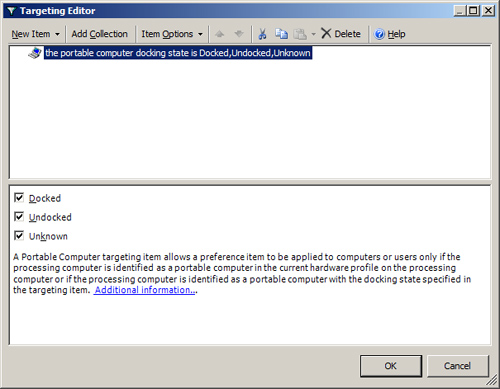
Portable Computer
A Portable Computer targeting item, shown in Figure 15,
allows a preference item to be applied to computers or users only if
the processing computer is identified as a portable computer in the
current hardware profile on the processing computer, or if the
processing computer is identified as a portable computer with the
docking state specified in the targeting item. Selecting a docking
state in the targeting item is optional. If no states or all states are
selected, the targeting item detects only whether the processing
computer is a portable computer.
Best Practices
Using
the Battery Present item and PCMCIA Present item in conjunction with
the Portable Computer Query item can also be useful for targeting
portable computers. |
Processing Mode
A Processing Mode targeting item, shown in Figure 16,
allows a preference item to be applied to computers or users only if
the Group Policy processing mode or conditions on the processing
computer match at least one of those specified in the targeting item. Table 4 defines each option for the Processing Mode item.
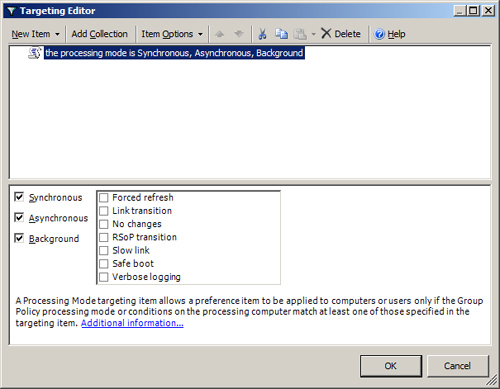
Table 4. Processing Mode Configuration Options
| Processing Mode or Condition | Description |
|---|
| Synchronous | GPO processing is set to synchronous. |
| Asynchronous | GPO processing is set to asynchronous. |
| Background | GPO processing is performed in the background, not foreground. |
| Forced refresh | The background refresh was forced. |
| Link transition | A change in link speed occurred between the current application and an earlier application of Group Policy. |
| No changes | No new Group Policy settings are applied to the computer or user. |
| RSoP transition | A
change in Resultant Set of Policy (RSoP) logging occurred between the
current application and an earlier application of Group Policy. |
| Slow link | Group Policy is applying over a slow network connection. |
| Safe boot | Windows is operating in safe mode. |
| Verbose logging | Verbose logging is enabled. |
RAM
A
RAM targeting item allows a preference item to be applied to computers
or users only if the total amount of physical memory in the processing
computer is greater than or equal to the amount specified in the
targeting item. The MB list accepts preference processing variables.
Press F3 to display the Select a Variable dialog box, which lists the
system-defined variables from which you can select.
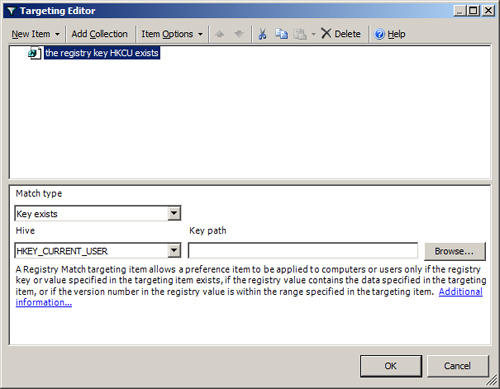
Registry Match
A Registry Match targeting item, shown in Figure 17,
allows a preference item to be applied to computers or users only if
the registry key or value specified in the targeting item exists, if
the registry value contains the data specified in the targeting item,
or if the version number in the registry value is within the range
specified in the targeting item. If the targeting item allows the
preference item and if Get Value Data is selected in the targeting
item, the targeting item saves the value data of the specified registry
value to the environment variable specified in the targeting item. The
Key Path text box and Value Name text box accept preference processing
variables. Press F3 to display the Select a Variable dialog box, which
lists the system-defined variables from which you can select.