Action Modes
Group
Policy Preferences settings come with a suite of action modes that
control the preference being configured. The action modes perform a
general set of actions, but each preference might have a slightly
unique way of dealing with the action specified—it is important that
you review the online Help for Windows Server 2008 for further
clarification. The action modes and behavior are defined as follows:
Create Create the object only if it does not already exist.
Replace Delete the object first, then create it.
Update Create the object if it does not exist; otherwise modify it.
Delete Delete the object.
Migrate Modify an item if it exists; otherwise do nothing.
Common Tab
The
advanced features and settings for Group Policy Preferences are
available on the Common tab when you are configuring any of the Group
Policy Preferences within the GPME, as shown in Figure 1.
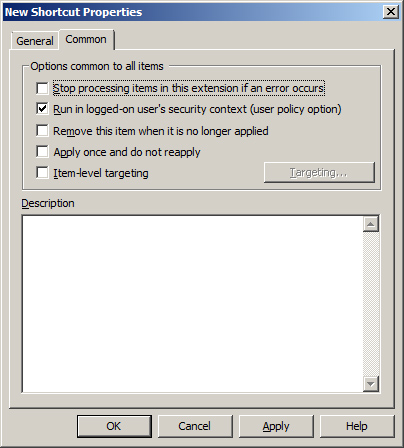
The
settings on the Common tab include four check boxes, an option to
configure targeting, and a text box for entering a description of the
GPO setting for documentation and troubleshooting purposes. The
settings include the following:
Stop processing items in this extension if an error occurs
The default behavior of Group Policy processing is that all settings
will be processed, even if there are multiple settings with the same
CSE and one of those settings fails. If you want the processing of the
settings to take place within a single CSE stop after one of the
settings within that CSE fails, enable this option. This setting has
only the scope of the current GPO.
Run in logged-on user’s security context (user policy option)
When Group Policy settings (both policies and preferences) apply, they
apply using the local System account. Because the local System account
has access only to the system environment variables and local
resources, the user context is not available. To allow access to the
user environment variables and network resources, you can enable this
option to process Group Policy Preferences using the logged-on user’s
account.
Remove this item when it is no longer applied Group
Policy Preferences settings are not removed from the registry when the
GPO is removed from the user or computer, nor when the user or computer
falls out of scope of management of the GPO. To have preferences
settings removed when the GPO no longer applies to the user or computer
object, you can enable this option.
Warning
Enabling
the option to remove the item when it is no longer applied will not
replace the Group Policy Preferences setting with the original value.
Instead, it will remove the registry value. If the operating system
relies on the value that has associated data, the system could receive
a stop error, causing a blue screen on the computer. Before configuring
any setting with this option, you should fully test the option and
understand how the registry value associated with the particular Group
Policy Preferences setting is used by the operating system. |
Apply once and do not reapply
Group Policy has a default refresh interval of approximately 90
minutes. This refresh interval allows new settings to be applied, and
old settings to be reapplied, without requiring the computer to restart
or the user to log off and log back on. If the Group Policy Preferences
setting that you are configuring should apply to the computer one time
only and never update on a refresh interval, you can enable this
setting. This is an excellent setting for establishing an initial array
of configurations that Group Policy Preferences can affect, while still
allowing users to create customized environments by changing the
settings after logging on and not having their settings overwritten. If
the setting appears under User Configuration, Group Policy Preferences
will apply these settings once on each computer the user logs on to. If
the setting appears under Computer Configuration, Group Policy
Preferences will apply the setting once per computer affected.
Item-Level Targeting
By default, all users and computers under the scope of management of
the GPO will receive the settings within the GPO. If you want the Group
Policy Preferences settings configured in a GPO to apply only to a
subset of the default users and computers, you can use targeting. Over
25 targeting items are available that can be used alone or in
conjunction with other items.
Description
Because every Group Policy Preferences setting allows for these
advanced features and settings, it is important to document the
configurations of each setting. You can use the Description text box to
describe the settings, options, and targeting items for each Group
Policy Preferences setting. The text that you enter into this text box
will appear when the Group Policy Preferences setting is selected
within the GPME (without requiring you to edit the Group Policy
Preferences setting itself), as shown in Figure 2.