Security Group
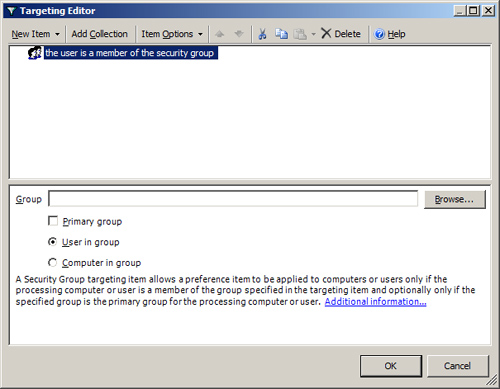
A Security Group targeting item, shown in Figure 18,
allows a preference item to be applied to computers or users only if
the processing computer or user is a member of the group specified in
the targeting item and, optionally, only if the specified group is the
primary group for the processing computer or user. The group’s security
identifier is used to determine group membership, not the display name
of the group. The types of groups that are supported include:
Domain groups
Global groups
Universal groups
Local groups
Site
A
Site targeting item allows a preference item to be applied to computers
or users only if the processing computer is in the site in Active
Directory specified in the targeting item. The Site box accepts
preference processing variables. Press F3 to display the Select a
Variable dialog box, which lists the system-defined variables from
which you can select.
Terminal Session
A
Terminal Session targeting item allows a preference item to be applied
to users only if the processing user is logged on to a terminal
services session with the settings specified in the targeting item.
Time Range
A
Time Range targeting item allows a preference item to be applied to
computers or users only if the current time on the end user’s computer
is within the time range specified in the targeting item.
User
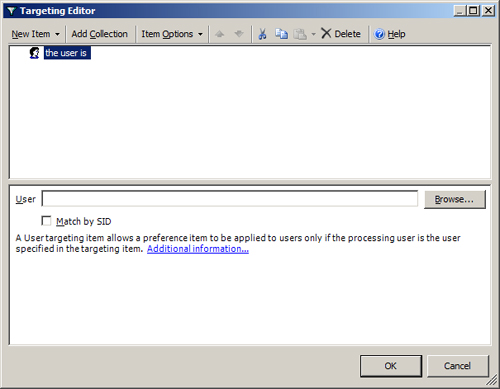
A User targeting item, shown in Figure 19,
allows a preference item to be applied to users only if the processing
user is the user specified in the targeting item. When the Match by SID
option is enabled, you must browse to select the user. If you do not
select Match by SID, a string match is performed. Although the domain
and user name of that user at the time of selection are displayed, the
targeting item saves the user’s SID for comparison to that of the
processing user. The User text box accepts preference processing
variables. Press F3 to display the Select a Variable dialog box, which
lists the system-defined variables from which you can select.
Note
User targeting is available only for preference items under User Configuration. |
WMI Query
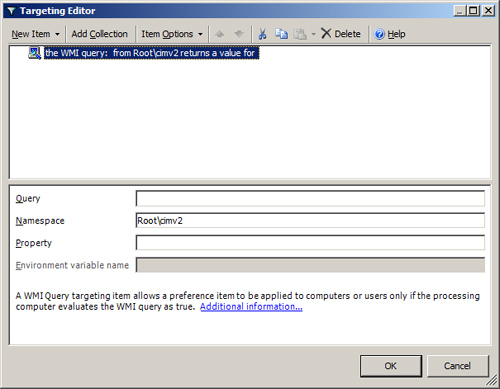
A WMI Query targeting item, shown in Figure 20,
allows a preference item to be applied to computers or users only if
the processing computer evaluates the WMI query as true. If any of the
value is returned from the query, the filter will return true.
Note
For
all of the item-level targeting items, text boxes for Computer Name
(NetBIOS only), Domain, Site, Terminal Session, and User (if not
matched by SID) accept single-character (?) and multiple-character (*)
wildcards. |