Symmetric
encryption
is the oldest and most established
way of ensuring message confidentiality, dating back for many
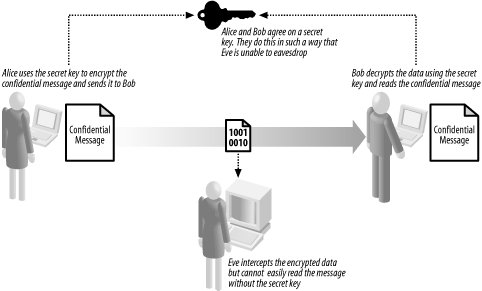
thousands of years. Figure 1 illustrates the
basic approach, which is as follows:
Alice and Bob agree on a secret key.
Alice composes a confidential message to Bob and encrypts it using
the secret key.
Alice sends the encrypted data to Bob.
Bob uses the secret key to decrypt the encrypted data, and reads the
confidential message.
The most important aspect of symmetric encryption is that Alice and
Bob agree on a secret key without Eve eavesdropping. If Eve acquires
the secret key, she will be able to read, modify. and forge messages
between Alice and Bob. The traditional means of agreeing on secret
key has been to meet in person at a private location, or to rely on a
secure and trusted courier service, both of which can be difficult to
arrange securely.
1. Creating the Encrypted Data
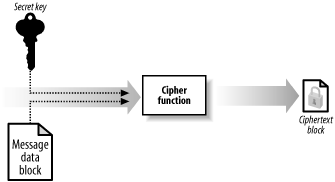
At the heart of a symmetric encryption
algorithm is a cipher function that transforms
fixed-size blocks of message data, known as
plaintext, into blocks of encrypted
data, known as
ciphertext,
illustrated by Figure 2. This type of function is
a block cipher, because it processes blocks of data sequentially and
independently. The output of a block ciphers is deterministic; this
means that a given block of plaintext encrypted using a given key
will always result in the same block of ciphertext. Different block
ciphers process differently sized blocks of plaintext.
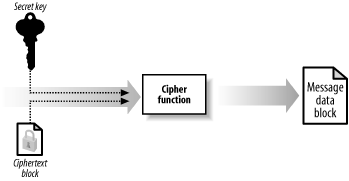
You can restore a block of plaintext from a block of ciphertext by
reversing the transformation, as illustrated by Figure 3. Both the transformation into ciphertext and
the restoration of the plaintext require the secret key; therefore,
Bob can decrypt the data only if he uses the same secret key that
Alice used to encrypt the message. Creating a hash code is a
"one-way" process, and the original
message data cannot be determined from the hash code data easily.
An
encryption
algorithm is the protocol for using a cipher function to encrypt
plaintext, in the same way that a hashing algorithm specifies how to
use a hash function to create a hash code. The algorithm specifies
how the plaintext is broken into blocks and how to use the output of
the cipher function in creating the ciphertext; the details of how to
perform these tasks differ between algorithms.
On a practical basis, the .NET Framework provides a standardized
model for using symmetric encryption algorithms, and you do not have
to understand the inner workings of any specific block ciphers.
However, you should understand some of the different ways that you
can configure an algorithm, which we discuss in the following
sections.