How to set up your own
virtual private network (Part 2)
Set up a mesh VPN
The process to set up a VPN with Hamachi
depends on the network you want to make. A mesh network is suitable for most
domestic purposes and easy to set up. To begin, just need to install client
application and click the large button “Power On”. You will be asked to name
your computer on Hamachi: default suggestion is the name of your computer using
on the current Windows network; but because Hamachi is completely private, you
can choose another name if you want.
When you complete it, your computer will be
assigned IPv4 and IPv6 for Hamachi (you will see them on the top of the
window). They are only used on Hamachi network, and will not interfere with
current connections. The only exception is that while Hamachi works, you can’t
access to any websites using IPv4 address in the range 5.x.x.x: Hamachi uses
this range for VPN connections, but it is also used by an internet registration
company based in Netherland. However, in reality, it just affects to a small
number of special websites, so it’s not sure that you will have problems.
When your computer is registered with
Hamachi, you can set a mesh network by clicking blue button “Create a new
network” and enter new name and password for the network. The name of the
network must be unique all over the world, so it could waste time searching for
a valid name, and of course, password should be hard to be guessed.
Now you can set up VPN from this PC to
other connected PC – or Mac – around the world. Just need to install the
software on remote system, press the power button and name this client. Click
“Join an existing network”, enter the name and password of the network and you
will be connected – it’s really simple.
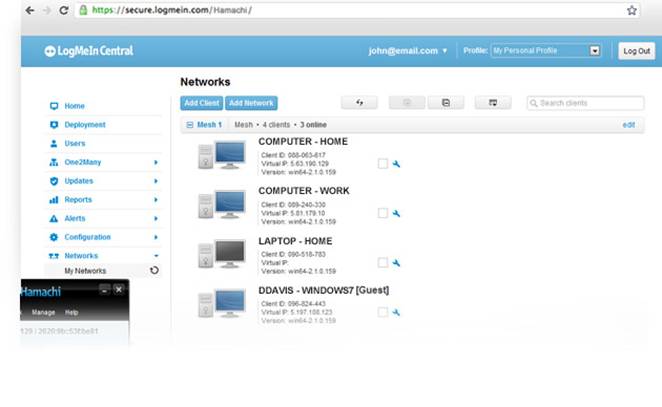
In the main Hamachi window, you will see
the name and address of other computers and if you return the first computer,
you will see your new client listed there. On the left of each name of clients,
you will notice a color indicator. Green means that the client is connected
successfully with the VPN; blue means that it may get trouble with the
transition between gates on the router: in this case, read Hamachi guideline to
find the instruction for TCP gate or static UDP configuration.
The communication throughout VPN
When your client is present in Hamachi
interface, you can click right on its name to see many different menu options.
Ping option will send a TCP package to the client to confirm that it actually
works and reacts. Chat allows you to open a window to communicate directly with
other PC users. The network admin can also evict a client from the network, if
necessary.
A more useful option is Browse, which opens
a new Explorer window shows available network resources on selected computers.
All traffic transferred Hamachi is encrypted with 256bit AES encryption – in
the words of LogMein, it ‘uses the same encryption as banks” – so you can
consider the security of this connection as same as local LAN. However, note
that Hamachi just provide the connection: you also need a valid account on a
remote PC to access shared drivers, and you may be asked to enter the password.
If you are trying to access shared resources stored on Mac from the PC client,
you have to make sure that SMB sharing option is enabled.
If you want to perform more advanced online
tasks, you can use Hamachi name and IP address of the remote PC, as described
in the client list, to access it directly, as if it stayed on your home
network. By this way, you can easily access shared documents along with
printers, storage forms and other resources such as webpages. You are able to
configure game and internet tool to work with one or many PC connected to VPN
as well.
Advanced networks
Mesh is the most convenient network for
normal use because it is simple to set up and manage. If you want to create a
hub-and-spoke network, you need a more advanced configuration. It is done
through LogMein web interface – an interface you will be familiar if you used
remote desktop service of the company. From the web control panel, you can
establish a new network, accept or decline participation requests, and
configure access permission.
It is a similar story if you want to
configure a gateway network yourself. Here you have to use web administration
interface to let network nodes act as gateway servers, and to manage client
access. There are some technical limitations to consider: Mac can’t act like a
gateway node now, as well as spokes can’t be members of a domain. For more
details about how to set up and manage hub-and-spoke and gateway network, you
will find more documents on LogMeIn website.
|
Free
VPN for free talk
VPN is not the only way to share private resources.
Combining with a remote proxy, it can be a valuable tool to access limited
websites and services.
For example, in some countries, important websites of
local authorities may be blocked or the access can be tracked. By using a VPN
to connect to the proxy server outside the country, local people can access
blocked website that nobody knows their location or track their traffic.
Similarly, browsing through a proxy connected VPN enables secure
transactions – for instance, online shopping or banking – when you are
connected to unsafe network, such as wireless public network. Without VPN,
wireless traffic could be blocked by a blocking application and transactions
are recorded by the administrator of that public network.
Although VPN is a vital part of this formula, only it is
not enough – you also need someone to run a proxy to access. Luckily, there
are several online services that you can use, often free, though some
services may limit bandwidth or set limits on data transfer monthly. You will
find free client application – Hotspot Shield on DVD, under Resources |
Security or you can download at http://hotspotshield.com.
Other options compose of CyberGhost (http://cyberghostvpn.com) and OpenVPN (http://openvpn.net).
|