The most common
way to describe
cryptographic systems is to assume that one person (usually named
Alice) wants to send a message to another person (Bob). However, a
third person (Eve) is determined to eavesdrop on their conversation.
Figure 1 shows the relationship between Alice,
Bob, and Eve.
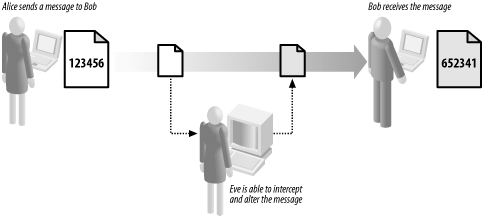
Let's assume that Eve will intercept and alter
messages between Alice and Bob irrespective of how those messages are
composed and sent. Although this might seem paranoid, there are
benefits to this way of thinking. By assuming that Eve can intercept
each message, you are, in effect, forced to regard the communications
channel as insecure—this is a realistic approach because
communications techniques that seem secure today may be compromised
in the future. By assuming that Eve can read any message, we focus on
the security of the message itself.
Cryptography has a long history, and different techniques for
protecting messages have been in use for thousands of years. For most
of that time, Alice, Bob, and Eve have represented real people or
organizations. With advances in technology, cryptography has become
irrevocably bound to the world of computers. Computers have
facilitated stronger cryptographic techniques but also allowed people
like Eve to mount stronger attacks on cryptography. Although we find
it useful to talk about Alice, Bob, and Eve, these names are often a
metaphor for computers.
When we say "Alice sends a message to
Bob," we do not consider the details of how she does
this, and as a result, we will be discussing techniques that are
applicable in many different situations. For example, Alice may use
her email client to compose and send a message, or she may have
written an application that will communicate automatically with her
bank to pay her bills while she is on vacation. Irrespective of how
Alice communicates with Bob, her need for cryptography can be broken
down into the three categories that we discuss in Section 1, Section 2, and Section 3.
1. Confidentiality
Confidentiality becomes
an issue when Alice wants to send a message containing a secret to
Bob. We assume that Eve can intercept and read the message, and that
Alice and Bob do not want Eve to know the secret contained in the
message.
The cryptographic solution to this problem is to obscure the contents
of the message using
encryption.
Encryption ensures that Eve cannot understand the messages sent
between Alice and Bob, even though she is able to intercept them.
Figure 2 illustrates the role of encryption in
confidentiality.
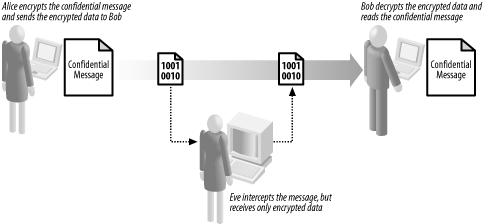
Encryption works on the basis that there is one piece of information
that Eve has not been able to acquire, known as the
key. The
key
is used as part of the encryption process and is kept secret. Alice
selects an encryption algorithm and uses the secret key to create the
encrypted data, as shown in Figure 3. When Bob
receives the encrypted text, he uses the secret key to restore the
confidential message so that he can read it.
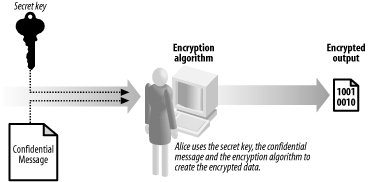
Using encryption changes the nature of the confidentiality
problem—Alice and Bob can exchange confidential messages as
long as Eve does not acquire the secret key. When Alice and Bob
exchange messages, they send the encrypted data only—they never
send the key, because they know that Eve can intercept it and then
read their messages.
This is the very essence of encryption—Alice uses one secret
that Eve does not know (the key) to protect another (the confidential
message). However, Eve can read the confidential messages if she
discovers or guesses the key.
In practice, using encryption becomes centered on protecting and
managing these secret keys. Some types of encryption require Alice
and Bob to know the key and are called
symmetric encryption (because Alice and Bob
have the same knowledge). The problem with symmetric encryption is
that Alice and Bob need to agree on what the secret key will be
before sending any messages.
Another approach is to use
asymmetric encryption, where only Bob has to
keep a secret. Bob creates a special pair of keys, one of which he
keeps secret (known as the private
key)
and one that is given out to anyone who wants to send him a message
(the public key). Bob can send Alice his public key
openly, because he does not care if Eve intercepts it.
When Alice wants to send Bob a confidential message, she uses an
asymmetric encryption technique to encrypt the data. This is similar
to the model shown in Figure 12-3; but instead of
using the secret key, Alice uses Bob's public key
and the contents of the message as inputs.
When Bob receives the message, he decrypts it using his private key
(which he always keeps secret) and restores the confidential message
from the encrypted data. Eve cannot read the message unless she
acquires Bob's secret key. Using this technique,
Alice and Bob do not have to agree on a key that they both know,
further reducing the chances that Eve can acquire the key during the
agreement process. The use of asymmetrical encryption is also known
as public key
cryptography.