Application or software security should be a critical element of your
security program. Most enterprises with information security programs have
yet to institute an application security program to address this realm.
Designing and implementing applications targeted for deployment on a cloud
platform will require that existing application security programs
reevaluate current practices and standards. The application security
spectrum ranges from standalone single-user applications to sophisticated
multiuser e-commerce applications used by millions of users. Web
applications such as content management systems (CMSs), wikis, portals, bulletin
boards, and discussion forums are used by small and large organizations. A
large number of organizations also develop and maintain custom-built web
applications for their businesses using various web frameworks
(PHP, .NET, J2EE, Ruby on Rails, Python, etc.). According to SANS, until 2007
few criminals attacked vulnerable websites because other attack vectors
were more likely to lead to an advantage in unauthorized economic or
information access. Increasingly, however, advances in cross-site
scripting (XSS) and other attacks have demonstrated that criminals looking
for financial gain can exploit vulnerabilities resulting from web
programming errors as new ways to penetrate important organizations. In
this section, we will limit our discussion to web application security:
web applications in the cloud accessed by users with standard Internet
browsers, such as Firefox, Internet Explorer, or Safari,
from any computer connected to the Internet.Since the browser has emerged as the end user client for accessing
in-cloud applications, it is important for application security programs
to include browser security into the scope of application security.
Together they determine the strength of end-to-end cloud security that
helps protect the confidentiality, integrity, and availability of the
information processed by cloud services.
1. Application-Level Security Threats
According to SANS, web application vulnerabilities in open source as well as
custom-built applications accounted for almost half the total number of
vulnerabilities discovered between November 2006 and October
2007. The existing threats exploit well-known application
vulnerabilities (e.g., the OWASP Top 10; see http://www.owasp.org/index.php/Top_10_2007), including
cross-site scripting (XSS), SQL injection, malicious file execution, and other
vulnerabilities resulting from programming errors and design flaws.
Armed with knowledge and tools, hackers are constantly scanning web
applications (accessible from the Internet) for application
vulnerabilities. They are then exploiting the vulnerabilities they
discover for various illegal activities including financial fraud,
intellectual property theft, converting trusted websites into malicious
servers serving client-side exploits, and phishing scams. All web frameworks and all types of web
applications are at risk of web application security defects, ranging
from insufficient validation to application logic errors.
It has been a common practice to use a combination of perimeter
security controls and network- and host-based access controls to protect
web applications deployed in a tightly controlled environment, including
corporate intranets and private clouds, from external hackers. Web
applications built and deployed in a public cloud platform will be
subjected to a high threat level, attacked, and potentially exploited by
hackers to support fraudulent and illegal activities. In that threat
model, web applications deployed in a public cloud (the SPI model) must be designed for an
Internet threat model, and security must be embedded into the Software Development Life Cycle (SDLC); see Figure 31.
2. DoS and EDoS
Additionally, you should be cognizant of application-level DoS and DDoS
attacks that can potentially disrupt cloud services for an extended
time. These attacks typically originate from compromised computer
systems attached to the Internet (routinely, hackers hijack and control
computers infected by way of viruses/worms/malware and, in some cases,
powerful unprotected servers). Application-level DoS attacks could
manifest themselves as high-volume web page reloads, XML web services requests (over HTTP or HTTPS), or
protocol-specific requests supported by a cloud service. Since these
malicious requests blend with the legitimate traffic, it is extremely
difficult to selectively filter the malicious traffic without impacting
the service as a whole. For example, a DDoS attack on Twitter on August
6, 2009, brought the service down for several hours (see Figure 2).
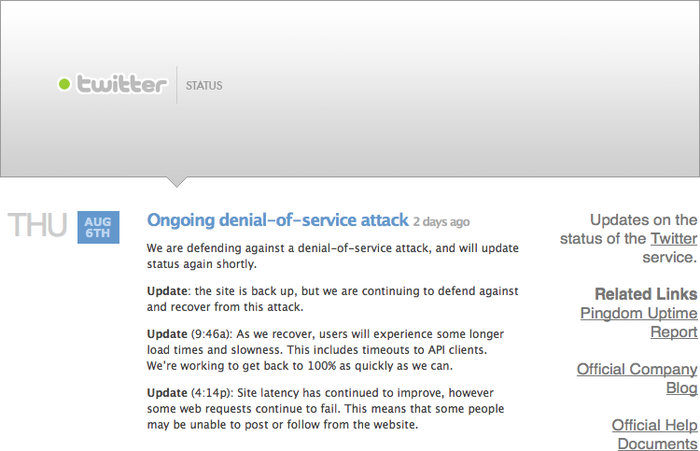
Apart from disrupting cloud services, resulting in poor user
experience and service-level impacts, DoS attacks can quickly drain your
company’s cloud services budget. DoS attacks on pay-as-you-go cloud
applications will result in a dramatic increase in your cloud utility
bill: you’ll see increased use of network bandwidth, CPU, and storage
consumption. This type of attack is also being characterized
as
economic denial of sustainability
(EDoS).
The low barriers for small and medium-size enterprises to adopt
cloud computing for legitimate use are also leveling the field for
hackers. Using hijacked or exploited cloud accounts, hackers will be
able to link together computing resources to achieve massive amounts of
computing without any of the capital infrastructure costs. In the
not-so-distant future, you might witness DoS attacks launched from IaaS
or PaaS clouds against other cloud services (such hostile and offensive
cloud models are being characterized as dark
clouds).
3. End User Security
You, as a customer of a cloud service, are responsible for end user security
tasks—security procedures to protect your Internet-connected PC—and for
practicing “safe surfing.” Protection measures include use of security
software, such as anti-malware, antivirus, personal firewalls, security
patches, and IPS-type software on your Internet-connected computer. The
new mantra of “the browser is your operating system” appropriately conveys
the message that browsers have become the ubiquitous “operating systems”
for consuming cloud services. All Internet browsers routinely suffer
from software vulnerabilities that make them vulnerable to end user
security attacks. Hence, our recommendation is that cloud customers take
appropriate steps to protect browsers from attacks. To achieve
end-to-end security in a cloud, it is essential for customers to
maintain good browser hygiene. The means keeping the browser (e.g.,
Internet Explorer, Firefox, Safari) patched and updated to mitigate
threats related to browser vulnerabilities. Currently, although browser
security add-ons are not commercially available, users are encouraged to
frequently check their browser vendor’s website for security updates,
use the auto-update feature, and install patches on a timely basis to
maintain end user security.
4. Who Is Responsible for Web Application Security in the
Cloud?
Depending on the cloud services delivery model (SPI) and service-level
agreement (SLA), the scope of security responsibilities will fall on the
shoulders of both the customer and the cloud provider. The key is to
understand what your security responsibilities are versus those of the
CSP. In that context, recent security surveys have highlighted the fact
that lack of transparency in security controls and practices employed by
CSPs is a barrier to cloud adoption.
To start with, cloud customers do not have the transparency
required in the area of software vulnerabilities in cloud services. This
prevents customers from managing the operational risk that might come
with the vulnerabilities. Furthermore, by treating their software as
proprietary, CSPs are impeding security researchers from analyzing the
software for security flaws and bugs. (The exception is cloud providers
that are operating on open source software.) Due to this lack of transparency,
customers are left with no choice but to trust their CSPs to disclose
any new vulnerability that may affect the confidentiality, integrity, or
availability of their application. For example, as of March 2009, no
prominent IaaS, PaaS, or SaaS vendors are participating in the
Common Vulnerability and Exposures (CVE) project. Case in
point: AWS took 7.5 months to fix a vulnerability that Colin Percival reported in May 2007. This vulnerability was a cryptographic weakness in
Amazon’s request signing code that affected its database API (SimpleDB) and EC2 API services, and it was not made
public until after it was fixed in December 2008. (Colin does
acknowledge that Amazon took this issue seriously at all times, and the
lengthy timeline was simply due to the large amount of work involved in
rolling out a patch to the affected services.)
Enterprise customers should understand the vulnerability
disclosure policy of cloud services and factor that into the CSP risk
assessment. The following sections discuss the web application security
in the context of the SPI cloud service delivery model.
5. SaaS Application Security
The SaaS model dictates that the provider manages the entire suite of
applications delivered to users. Therefore, SaaS providers are largely
responsible for securing the applications and components they offer to
customers. Customers are usually responsible for operational security
functions, including user and access management as supported by the
provider. It is a common practice for prospective customers, usually
under an NDA, to request information related to the provider’s
security practices. This information should encompass design,
architecture, development, black- and white-box application security
testing, and release management. Some customers go to the extent of
hiring independent security vendors to perform penetration testing (black-box security testing) of SaaS
applications (with consent from the provider) to gain assurance
independently. However, penetration testing can be costly and not all
providers agree to this type of verification.
Extra attention needs to be paid to the authentication and access control features offered by SaaS
CSPs. Usually that is the only security control available to manage risk
to information. Most services, including those from Salesforce.com and Google, offer a web-based
administration user interface tool to manage authentication and access
control of the application. Some SaaS applications, such as Google Apps, have built-in features that end users can
invoke to assign read and write privileges to other users. However, the
privilege management features may not be advanced, fine-grained access
and could have weaknesses that may not conform to your organization’s
access control standard. One example that captures this issue is the
mechanism that Google Docs employs in handling images embedded in
documents, as well as access privileges to older versions of a document.
Evidently, embedded images stored in Google Docs are not protected in
the same way that a document is protected with sharing controls. That
means if you have shared a document containing embedded images, the
other person will always be able to view those images even after you’ve
stopped sharing the document. A blogger discovered this access control quirk and brought it to
Google’s attention. Although Google has acknowledged the issue, its
response conveys that it believes those concerns do not pose a significant security risk to
its users.
Another incident related to Google Docs was a privacy
glitch that inappropriately shared access to a small fraction
(Google claims 0.05% of the documents were affected) of word processing
and presentation documents stored on its Google Apps cloud service.
Though the documents were shared only with people whom the Google Docs
users had already shared documents, rather than with the world at large,
the problem illustrates the need to evaluate and understand
cloud-specific access control mechanisms.
Cloud customers should try to understand cloud-specific access
control mechanisms—including support for strong authentication and
privilege management based on user roles and functions—and take the
steps necessary to protect information hosted in the cloud. Additional
controls should be implemented to manage privileged access to the SaaS
administration tool, and enforce segregation of duties to protect the
application from insider threats. In line with security standard
practices, customers should implement a strong password policy—one that
forces users to choose strong passwords when authenticating to an
application.
It is a common practice for SaaS providers to commingle their
customer data (structured and unstructured) in a single virtual data
store and rely on data tagging to enforce isolation between customer data. In that
multitenant data store model, where encryption may not be
feasible due to key management and other design barriers, data is tagged
and stored with a unique customer identifier. This unique data tag makes
it possible for the business logic embedded in the application layer to
enforce isolation between customers when the data is processed. It is
conceivable that the application layer enforcing this isolation could
become vulnerable during software upgrades by the CSP. Hence, customers
should understand the virtual data store architecture and the preventive
mechanisms the SaaS providers use to guarantee the compartmentalization
and isolation required in a virtual multitenant environment.Established SaaS providers, such as Salesforce.com, Microsoft, and
Google, are known to invest in software security and practice security
assurance as part of their SDLC. However, given that there is no
industry standard to assess software security, it is almost impossible
to benchmark providers against a baseline.
Table 1 lists
security controls at the application level.
Table 1. Security controls at the application level
| Threat
outlook | Medium |
|---|
| Preventive
controls | Identity management,
access control assessment, browser hardened with latest patches,
multifactor authentication via delegated authentication,
endpoint security measures including antivirus and
IPS |
| Detective
controls | Login history and
available reports from SaaS vendors |
6. PaaS Application Security
PaaS vendors broadly fall into the following two major
categories:
Software vendors (e.g., Bungee, Etelos, GigaSpaces,
Eucalyptus)
CSPs (e.g., Google App Engine, Salesforce.com’s Force.com,
Microsoft Azure, Intuit QuickBase)
Organizations evaluating a private cloud may utilize PaaS software
to build a solution for internal consumption. Currently, no major
public clouds are known to be using commercial
off-the-shelf or open source PaaS software such as Eucalyptus (Eucalyptus does offer a limited experimental
pilot cloud for developers at Eucalyptus.com, however). Therefore, given the nascent stage of PaaS
deployment, we will not discuss software security of standalone PaaS
software in this chapter. Nonetheless, it is recommended that
organizations evaluating PaaS software perform a risk assessment and
apply the software security standard similar to acquiring any enterprise
software.
By definition, a PaaS cloud (public or private) offers an
integrated environment to design, develop, test, deploy, and support
custom applications developed in the language the platform supports.
PaaS application security encompasses two software layers:
Security of the PaaS platform itself (i.e., runtime
engine)
Security of customer applications deployed on a PaaS
platform
Generally speaking, PaaS CSPs (e.g., Google, Microsoft, and
Force.com) are responsible for securing the platform software stack that
includes the runtime engine that runs the customer applications. Since
PaaS applications may use third-party applications, components, or web
services, the third-party application provider may be responsible for
securing their services. Hence, customers should understand the
dependency of their application on all services and assess risks
pertaining to third-party service providers. Until now, CSPs have been
reluctant to share information pertaining to platform security using the
argument that such security information could provide an advantage for
hackers. However, enterprise customers should demand transparency from
CSPs and seek information necessary to perform risk assessment and
ongoing security management.
6.1. PaaS application container
In the multitenant PaaS service delivery model, the core security tenets
are containment and isolation of multitenant applications from each
other. In that model, access to your data should be restricted to your
enterprise users and to applications that you own and manage. The
security model of the PaaS platform runtime engine is the CSP’s
intellectual property, and it is essential to delivering the “sandbox”
architecture in a multitenant computing model. Hence, the sandbox
characteristic of the platform runtime engine is central in
maintaining the confidentiality and integrity of your application
deployed in the PaaS. CSPs are responsible for monitoring new bugs and
vulnerabilities that may be used to exploit the PaaS platform and
break out of the sandbox architecture. This type of situation is the
worst case scenario for a PaaS service; the privacy implications for
customer-sensitive information are undesirable and could be very
damaging to your business. Hence, enterprise customers should seek
information from the CSP on the containment and isolation architecture
of the PaaS service.
Network and host security monitoring outside the PaaS platform
is also the responsibility of the PaaS cloud provider (i.e.,
monitoring of a shared network and system infrastructure hosting
customer applications). PaaS customers should understand how PaaS CSPs
are managing their platform, including updating of the runtime engine
and change, release, and patch management.
7. Customer-Deployed Application Security
PaaS developers need to get familiar with specific APIs to deploy and manage software modules that enforce
security controls. Furthermore, given that the API is unique to a PaaS
cloud service, developers are required to become familiar with
platform-specific security features—available to them in the form of
security objects and web services for configuring authentication and
authorization controls within the application. When it comes to PaaS API
design, currently no standard is available, nor is there any concerted
effort by CSPs to develop a ubiquitous and consistent API across
clouds—and that makes porting of an application across PaaS clouds a
monumental task. Currently, the Google App Engine supports only Python and Java, and Salesforce.com’s Force.com supports only a proprietary language called Apex. (Apex differs from languages such as C++, Java, and
.NET. Unlike those languages, Apex is much more limited in scope and is
specific to building business applications on the Force.com platform.)
In this regard, cloud services have the potential to retain customers
more forcefully than traditional software licensing. The lack of an API
standard has ramifications for both security management and portability
of applications across the cloud.
Developers should expect CSPs to offer a set of security features,
including user authentication, single sign-on (SSO) using federation, authorization (privilege management), and SSL or TLS
support, made available via the API. Currently, there is no PaaS
security management standard: CSPs have unique security models, and
security features will vary from provider to provider. In the case of
the Google App Engine, a developer using Python or Java objects can
configure the user profile and select HTTPS as a transport protocol.
Similarly, Force.com offers an Apex API to configure security
parameters, manipulate various runtime configurations, and assign
certain TCP ports for application-to-application connection-type
interactions using Apex objects.
Based on our assessment of major PaaS CSPs, the security features
available to PaaS applications are limited to basic security
configuration—SSL configuration, basic privilege management, and user
authentication using the provider’s identity store. In only a few cases,
user federation is supported using the Security Assertion Markup Language (SAML).
Table 2 lists
security controls applicable to PaaS applications.
Table 2. Security controls applicable to PaaS applications
| Threat
outlook | Medium |
|---|
| Preventive
controls | User authentication,
account management, browser hardened with latest patches,
endpoint security measures including antivirus and
IPS |
| Detective
controls | Application vulnerability
scanning |
8. IaaS Application Security
IaaS cloud providers (e.g., Amazon EC2, GoGrid, and Joyent) treat the
applications on customer virtual instances as a black box, and therefore
are completely agnostic to the operations and management of the
customer’s applications. The entire stack—customer applications, runtime
application platform (Java, .NET, PHP, Ruby on Rails, etc.), and so
on—runs on the customer’s virtual servers and is deployed and managed by
customers. To that end, customers have full responsibility for securing
their applications deployed in the IaaS cloud. Hence, customers should
not expect any application security assistance from CSPs other than
basic guidance and features related to firewall policy that may affect
the application’s communications with other applications, users, or
services within or outside the cloud.
Web applications deployed in a public cloud must be designed for
an Internet threat model, embedded with standard security
countermeasures against common web vulnerabilities (e.g., the OWASP Top
10). In adherence with common security development practices, they
should also be periodically tested for vulnerabilities, and most
importantly, security should be embedded into the SDLC. Customers are solely responsible for keeping their
applications and runtime platform patched to protect the system from
malware and hackers scanning for vulnerabilities to gain unauthorized
access to their data in the cloud. It is highly recommended that you
design and implement applications with a “least-privileged” runtime model (e.g., configure the
application to run using a lower privileged account).
Developers writing applications for IaaS clouds must implement
their own features to handle authentication and authorization. In line with enterprise
identity management practices, cloud applications should be designed to
leverage delegated authentication service features supported by an
enterprise Identity Provider (e.g., OpenSSO, Oracle IAM, IBM, CA) or
third-party identity service provider (e.g., Ping Identity, Symplified,
TriCipher). Any custom implementations of Authentication, Authorization, and Accounting (AAA)
features can become a weak link if they are not properly implemented,
and you should avoid them when possible.
In summary, the architecture for IaaS hosted applications closely
resembles enterprise web applications with an
n-tier distributed architecture. In an enterprise,
distributed applications run with many controls in place to secure the
host and the network connecting the distributed hosts. Comparable
controls do not exist by default in an IaaS platform and must be added
through a network, user access, or as application-level controls.
Customers of IaaS clouds are responsible for all aspects of their
application security and should take the steps necessary to protect
their application to address application-level threats in a multitenant
and hostile Internet environment.
Table 3 lists
security controls applicable to IaaS applications.
Table 3. Security controls applicable to IaaS applications
| Threat
outlook | High |
|---|
| Preventive
controls | Application developed
using security-embedded SDLC process, least-privileged
configuration, timely patching of application, user
authentication, access control, account management, browser
hardened with latest patches, endpoint security measures
including antivirus, IPS, host-based IDS, host firewall, and
virtual private network (VPN) for administration |
| Detective
controls | Logging, event
correlation, application vulnerability scanning and
monitoring |
9. Public Cloud Security Limitations
Customers evaluating the public cloud should keep in mind that there are
limitations to the public cloud when it comes to support for custom
security features. Security requirements such as an application
firewall, SSL accelerator, cryptography, or rights management using a
device that supports PKCS 12 are not supported in a public SaaS, PaaS,
or IaaS cloud. In the future, IaaS and PaaS providers may offer some of
these more sophisticated security features, depending on customer
demand. In general, any mitigation controls that require deployment of
an appliance or locally attached peripheral devices in the public
IaaS/PaaS cloud are not feasible at this time.