Weighing Physical vs. Virtual Options
If your company is running a virtualized
environment, the question is bound to come up (if it hasn’t already): Does it
make sense to implement a virtual firewall? The answer, however, can depend on
numerous company specific factors. There are also questions as to where to
locate the firewall and what type of implementation is most appropriate for
your company.
We will explain how virtual fire walls
differ from traditional, on-premises firewalls, and then explore issues related
to determining whether your company needs a virtual firewall and how to
implement it.
Do
You Need A Virtual Firewall?
Physical vs. Virtual
As Jon Oltsik, Enterprise Strategy Group
(www.esg-global.com) senior principal analyst, aptly puts it, the biggest
difference between a virtual firewall and a physical firewall is fairly
obvious: A physical firewall is essentially a piece of standalone hardware,
while a virtual firewall is a virtual appliance installed on top of
virtualization management software. "This difference should not impact
functionality, but it may impact performance," Oltsik says. "Virtual
firewalls also require some security oversight to lock down the physical server
and hypervisor."
Mike Fratto, senior analyst with Current
Analysis (wwwxurrentanajysjs.com), says aside from certain performance
characteristics, in many cases a virtual and physical firewall from the same
vendor are functionally equivalent. "Virtual appliances typically support
less performance than hardware because virtual appliances are software-based,
are on shared hardware, etc.," he says. A physical firewall, meanwhile,
sits at a fixed position in the network and creates a hard exterior at the
perimeter "but does nothing for traffic running over the virtual network,"
he says.
Overall, Fratto says physical firewalls
make sense when trying to establish a hardened perimeter, including one that
protects the virtual infrastructure, services, etc., from unauthorized use.
Here, he says, "an existing data center firewall may suffice."
Virtual firewalls, meanwhile, are often targeted at a subset of services
running within the virtual environment rather than the entire environment.
Thus, he says, "you end up with a bunch of little perimeters based on
applications or departments," for example, rather than one large
perimeter. That means applications can be better protected from attack than if
using VLANs and other isolation techniques, he says.
Another distinction between physical and
virtual firewalls is that a virtual firewall and the servers it protects can
reside anywhere in the virtual environment, something that allows the movement
of virtual machines while maintaining the virtual perimeter, Fratto says.
Common firewall implementations
Currently, most organizations still use
firewall appliances vs. virtual firewalls, Oltsik says. "Sometimes, they
use multifunction security devices, but it is still a security device,"
he says. Oltsik anticipates virtual firewall implementations will increase as
users grow more comfortable with using virtualization technology and as
companies seek to increase their support of cloud computing and server
virtualization efforts.
Firewalls
Among the types of firewalls available,
Fratto says stateful packet filtering is the most commonly used among
businesses, as are application proxies that are specialized to a particular
protocol, such as HTTP, or a particular application, such as one enabling
access to company email via Web access.
In terms of where to locate a virtual
firewall compared to a physical firewall, Fratto says physical firewalls are
generally positioned at network choke points whereas virtual firewalls are
positioned closer to applications. "It doesn't make sense to try to
deploy a virtual firewall like a physical one because each hypervisor is its
own connection to the physical network," he says. This may change in the
future, Fratto says, but currently if you have 10 hypervisors you have to have
individual connections to the physical network.
Oltsik says that while companies should
place primary network firewalls in the same locations regardless of whether
they are physical or virtual in nature, "virtual firewalls are handy
because you can deploy them anywhere instantly. This gives a lot of new options
for network segmentation and access control," he says.
Is a virtual firewall practical?
When determining whether a virtual
firewall makes sense, performance is a significant factor, Fratto says. In
this context, performance means "more than bits per second."
Depending on the type of firewall, he says, "factors like connections per
second, number of concurrent connections, and any Layer 4-7 checking can be
significantly reduced on a virtual firewall," he says. Performance is one
reason why virtual firewalls are best-suited for targeted applications vs.
being used as a general physical firewall replacement, he says. "If the
virtual firewall can't support the traffic demands, then companies need to look
to either load balancing across more than one firewall or using a hardware
firewall."
Other factors can include a given company's
virtual environment and its future plans, Fratto says. Elsewhere, for companies
that already have a physical firewall in place, he says, implementing a virtual
firewall from the same company will ease deployment and manageability, as
"the learning curve is much shorter, if there is any at all." He
adds, though, that the virtual firewall and physical firewall "should be
manageable via the same management station so it simply appears to be a
firewall regardless." Companies can mix and match firewalls as needed,
such as by using a virtual firewall in the virtualization environment and a
physical firewall elsewhere, but "that means more management overhead."
Another issue to keep in mind, Fratto says,
is licensing. "Virtual firewalls can be pretty pricey compared to the
capabilities they provide." Usually, he says, virtual firewalls are
licensed per unit, "which can add up." Companies should also consider
the cloud platforms they're looking to support if planning to move to a private
cloud platform or a public cloud provider, he says. "While many of the
public cloud providers offer basic firewalls as part of their services, using
a known firewall is often easier operationally."
Where SMBs are specifically concerned,
Oltsik says a virtual firewall is preferable to a physical firewall only if
the company is comfortable with using virtualization technology and the
company is able to select a virtual firewall that's designed especially for
SMBs. That means it should provide good ease of use, standard configuration
templates, simple rule configuration, and other benefits. Fratto says the
question isn't whether an SMB should or shouldn't buy a virtual firewall. The
question is "whether a virtual firewall will be suitable or not. If an SMB
is running a virtual environment and it needs fire- walling closer to their
applications, then it makes sense. Otherwise not."
Other considerations
When deciding whether to use a virtual or
physical firewall or a hybrid approach combining the two, companies need to
mull over several primary considerations, including how comfortable it is using
virtualization technology. If the company is comfortable with provisioning,
maintaining, and securing a virtual firewall, Oltsik says, "then it
shouldn't be a problem." Oltsik notes that he sees virtual firewalls often
in remote offices of larger companies, as well as in hosting and cloud data
centers to segment resources for multi-tenancy. Though he doesn't see virtual
firewalls as much in SMBs, he says, "that may change."
VLANs
One consideration companies should keep in
mind regarding virtual firewalls is how regulated the company is. Highly
regulated companies, Oltsik says, should check with their auditors to
determine whether a virtual configuration constitutes a compliance violation.
Location is another consideration, he says, as "it may take weeks to get
a firewall appliance through customs in some countries, while a virtual
machine can be downloaded instantly."
If the company has numerous remote
offices, Oltsik says, "it may be best to deploy virtual firewalls in
standard configurations and then centrally manage them." Further, he says,
"I would also think long and hard about whether you want to dedicate a
physical server to the firewall or run multiple virtual machines on a server
that hosts virtual firewalls. From a security perspective, running multiple
virtual machines could be a bad idea, and I can't imagine it would meet
regulatory compliance requirements."
Where hybrid configurations are concerned,
Fratto says, locating a physical firewall in front of a virtual environment can
make sense "just to restrict access to the underlying virtual
environment, which is separate from restricting access to servers in the
virtual environment." The primary consideration of which firewall setup
to use, however, is whether the company's security policies or external
requirements (such as regulations) dictate that a more targeted firewall
strategy is necessary, he says. "A related consideration is whether the
company has to document and prove out their security architecture," Fratto
adds.
A physical firewall sitting at the
perimeter of the virtual network can provide adequate protection for
applications running in the virtual environment, Fratto says. "IT can
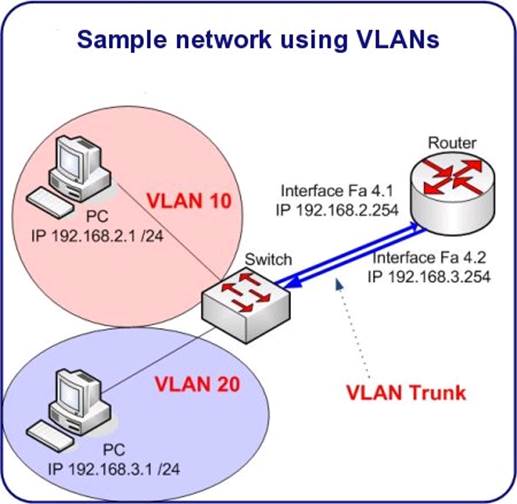
create traffic separation within the virtual environment using VLANs, for
example. If a server on one VLAN wants to talk to another server on a different
VLAN, the traffic has to pass through a router that can reside at the perimeter
or at the edge, or the server has to have multiple interfaces on multiple
VLANs," Fratto says. "Either way, you probably only want to allow
access to a subset of services on the server, so a virtual firewall can limit
connections to exactly what is needed to allow the application to work."
The additional burden comes when it's time
to prove that an application was only accessed by authorized systems, as
there might be issues demonstrating that VLAN separation is good enough, he
says. "The best thing to do is work with whoever manages your company's
security policy and regulatory compliance to determine how your company will
meet the requirements," he says.
Key points
Performance is a key factor in determining
whether using a virtual firewall makes practical sense.
A virtual firewall can be preferable to a
physical firewall for an SMB if the company is comfortable with virtualization
technology and the virtual firewall is designed for SMBs.
Beyond some performance traits, a virtual
and physical firewall from the same vendor often can be functionally
equivalent.
When considering the use of a virtual
firewall, keep in mind how highly regulated the company is.