Are your apps spying on you?
There are some Android apps which appear to
want to access everything on your phone before they will run. These are
apparently legitimate apps and yet the level of interference is high, leading
many to question whether or not they are actually spying on you. Whether they
are reading your phone status or modifying your SD card, they can appear rather
intrusive at times and it is not just the Facebook app which comes under such
criticism. Many apps want this level of access.
“I wouldn’t say these apps were spying on
you these permissions are very much a general thing,’’ says Ian Naylor, founder
of developer App Institute. “You may have a lazy developer turn on all
permission requests in the app as it’s the easy option, or equally a new
developer may not completely understand the specifics of each setting. They
wouldn't know the full effect that a few tick boxes in the integrated
development environment (IDE) and the subsequent warnings will have on the user
when installing."
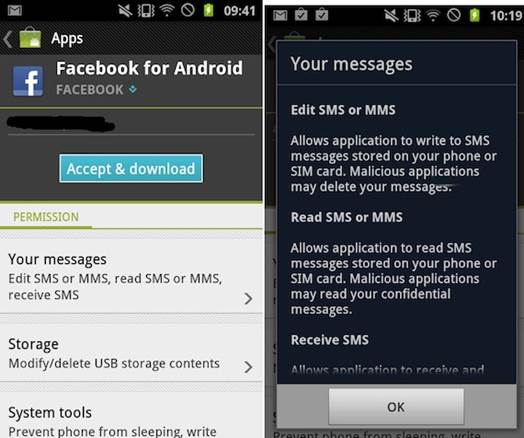
A
vulnerability in the Facebook and Dropbox apps for Android and iOS means your
data can be taken by anyone with access
Naylor says that in the majority of cases,
the app may not actually need access to those permissions and so it won’t
actually be doing anything with the data. “Newbie and lazy developers aside so
that's got to be 50 per cent at least of all apps covered an app might rightly
need those permissions it’s asking for. So it certainly won’t be used for
spying."
So why would an app need your contact
information? “Well,” Naylor continues, “an app might want to offer a simple
share function so you can recommend it to your friends. This would potentially
mean having to give them app permissions to your contacts to auto-complete the
names to send to.”
And the phone status? “The app will need to
check it has network signal to send the message," Naylor answers. “The
more functions you build into an app, the more likely it’s going to increase
the permissions needed.”
It is clear then that you may have little
to worry about when it comes to fears an app is spying on you. Either the
developer behind the app is too inexperienced to even know the data is being
accessed, much of the rest of the time those permissions are needed in order
for the app to function to the best of its ability.
That said, however, there are some elements
of snooping that you may not want. In 2010, researchers from Duke University,
Penn State University and Intel Labs found that some apps will send private
user information to advertising networks and the report concluded: “While some
mobile phone operating systems allow users to control applications’ access to
sensitive information, such as location sensors, camera images, and contact
lists, users lack visibility into how applications use their private data.”
And
why do apps need permissions such as access to your messages and phone calls?
Although these apps ask for your permission
when you install the app, what they do not do, by and large, is divulge exactly
how that information will be used so it was all the more disturbing when the
report found that phone numbers and GPS locations were being harvested off to
advertisers. Worse is later news which has shown that documents and photos have
been sent to remote servers in the past. The New York Times found that it could
build an app to do this and all that was needed was permission to access the
internet.
And why do apps need permissions such as
access to your messages and phone calls? This is opening users up to trouble.
It would be better if apps were more open about why they want your information,
which is why we list the most frequent permission requests across the pages as
a way to assist. It is heartening that some developers do try to explain. The
people behind the Any.Do task managing app do this, explaining that full
internet access is needed to access Google Tasks, that it needs to modify and
delete SD card contents to store backups, that it needs access to directly call
phone numbers for its missed call feature and so much more. But until this kind
of behaviour becomes a rule rather than an exception, then it is fair to say
there is a security risk, no matter how small It may turn out to be.
That said, developers believe the risk
really is minimal but that companies need to be more open and treat data with
care and a bit more respect. “I wouldn’t say the apps are spying on users but
in order to offer the services that we crave, intelligent apps that seem to
‘know’ what we need from them, they need to have access to the information we
supply through the device,” says Matt Sims, marketing director at mobile
technology company Ziconix. “I would hope that any business or individual
releasing an app would take the correct legal steps to protect users’
information".
|
Permission
|
What it means
|
What you need to know
|
|
Make phone calls
|
An app can dial a number on your phone
and connect. Google Voice and Google Maps use this.
|
Although apps could call premium rate
numbers, this is rare but do be sure that you trust an app before you
download. Those from recognised developers are likely to be fine.
|
|
Modify/delete SD card contents
|
Applications can read, write and delete
anything which is stored on your device’s SD card.
|
Apps which need to store data on the SD
card will ask for this permission and again, you need to be sure of the
integrity of the app developer and that access is necessary.
|
|
Read contact data, write contact data
|
This will allow your app to access the
contacts stored in your device and make additions to them.
|
Some applications need this - social
networks, contact management apps, SMS apps - but a lot do not, so if you
don’t feel an app should access your contacts, do not allow it.
|
|
Read calendar data, write calendar data
|
The app will access your calendar, read
it and have the ability to make additions to it.
|
Calendar events can track your
whereabouts and they can also contain contact information so if you do not
want this to be known to an app, disallow it.
|
|
Read sensitive logs
|
Access is granted to read what any other
applications have written as debugging/logging code.
|
No app should be given this permission
other than those you absolutely trust. The word sensitive is in there for a
reason so take care.
|
|
Find (GPS) location
|
An app will be able to locate the exact
position of your phone and, in many cases, yourself.
|
Location-based services and advertising
use this, and it is typical for cinema, restaurant and map apps to ask for
permission to access your location via GPS.
|
|
Full internet access
|
An app will be able to access the
internet for any means such as saving files to the cloud.
|
Granting this gives an app the potential
to be able to transfer data off your phone, but there are many legitimate
uses such as weather, social networking, web browsers and more.
|
|
View network state / Wi-Fi state
|
The app will be able to find out if you
are connected to the internet via 3G or Wi-Fi.
|
You need not worry about this because the
app is only working out whether you have network access at that particular
moment in time.
|
|
Manage accounts
|
Apps will be able to manage the accounts
on your Android smartphone.
|
There is a potential for apps to be able
to delete accounts but they can certainly add them. Facebook will ask for
this permission.
|
|
Prevent phone from sleeping
|
If an app needs to be always on in order
to work, it may ask to be prevented from sleeping.
|
Ensuring a phone does not sleep means
they remain useful. An alarm clock which goes to sleep is no good and neither
is a video player which closes halfway through a clip.
|