Shoring up your security starts with your
employees
Even the most sophisticated software, the
strictest policies, and a religious adherence to the best of best practices
cannot prevent someone from making a mistake that will compromise the company’s
security. People are the weakest link in the chain of security; they willfully
yield sensitive information, log onto unsecured networks with company hardware,
bring their own devices in to work, and open questionable email attachments.
These well-meaning but misguided employees are one of the biggest threats your
business faces, but there are steps you can take to mitigate the risk.
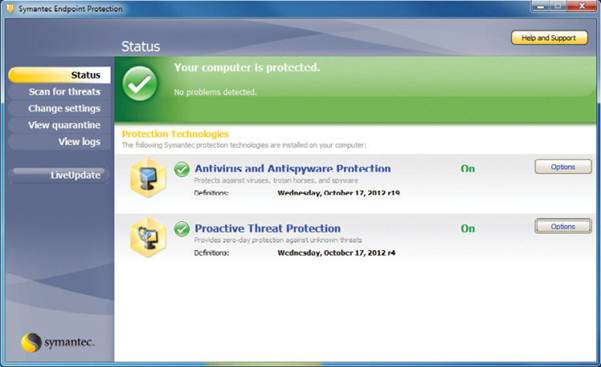
Making
sure your software is up-to-date is an important aspect of securing your
devices
The soft solution
Some problems (many, in fact) can be solved
by installing security software, such as antivirus, anti-malware, and
firewalls. But software isn’t a set-it-and-forget-it proposition. To
effectively protect your organization’s PCs, notebooks, and smartphones, every
employee needs to make sure this software is running on each device he or she
uses. Security software is typically very easy to use and you can often see if
it’s working by looking at the notification area of Windows-based PCs. Never use
a device on which the security software is not working or out of date. It’s
also important to keep up on Windows updates as well. Employees may need
minimal training for how to enable this software, check for and install
updates, and what to do if they suspect that the software is not working
properly. Employees also need to be cautioned against disabling the software
for any reason. People are the weakest link in the chain of security; they
willfully yield sensitive information, log onto unsecured networks with company
hardware, bring their own devices in to work, and open questionable email
attachments.
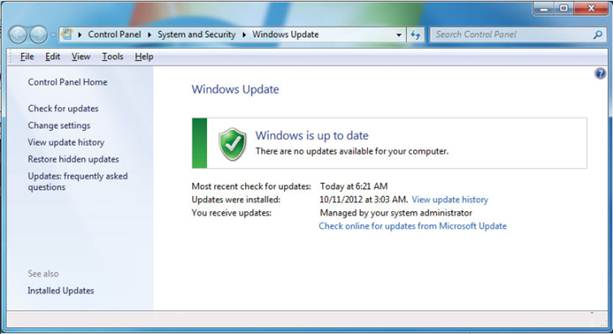
Get
to know your security software and how to keep it working properly
Impose limits
You should look at your organization’s
security the same way you look at securing the premises: Not everyone needs a
master key. Employees in IT may need complete access to the network, but don’t
hesitate to set up group policies that restrict access to certain areas of the
network for certain positions. If each group is properly isolated, any
potential outbreak or breach will likely be limited to a single division. IT
personnel should also be logging their access of sensitive data as well, so you
can follow the paper trail in the event of a security breach.
Old dog, meet new tricks
We mentioned it before, but training is the
key to bolstering your organization’s security. Take time out of the regular
work week to occasionally review safe working habits, such as avoiding bringing
in outside devices to access the network, accessing open Wi- Fi networks with
company equipment, and how to recognize and deal with suspected spam and
malware infections.
Cut off former employees
Former employees, disgruntled or not, can
be a real security threat for organizations. As soon as an employee is no
longer on premises, his user accounts should be locked or purged, access rights
revoked, and any hardware he used accounted for and reset to factory settings.
If the former employee in question has access to sensitive data and
administrator rights on any machines or to parts of the network, it’s
imperative to immediately change the passwords and logins for those areas.
Regularly
review security policies and best practices with employees
Take responsibility
To effectively manage your organization’s
security, you need to recognize that simple mistakes are the reason you’ll
become a target. With the right training, a little software, and policies that
minimize the chance for mistakes, however, you can lock the bad guys out for
good.
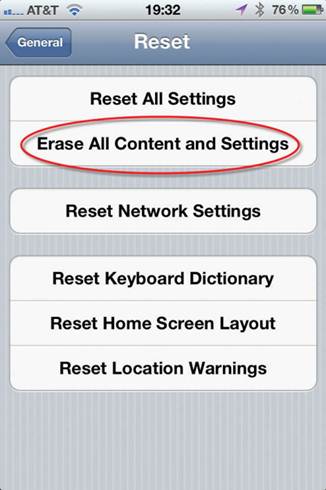
Make
sure to reclaim any hardware an employee was using before he or she leaves, and
reset it to factory specifications immediately