One
of the most overlooked but perhaps most critical components of server
security is the actual physical security of the server itself. The most
secure, unbreakable web server is powerless if a malicious user can
simply unplug it. Worse yet, someone logging in to a SharePoint SQL
database role server could potentially copy critical data or sabotage
the machine directly.
Physical security is a must for
any organization because it is the most common cause of security
breaches. Despite this fact, many organizations have loose levels, or no
levels, of physical security for their mission-critical servers. An
understanding of what is required to secure the physical and login
access to a server is a must.
Restricting Physical Access to Servers
Servers should be
physically secured behind locked doors, in a controlled-access
environment. Soft-felt cubicles do not provide much in the realm of
physical security, so it is therefore unwise to place mission-critical
servers at the feet of administrators or in similar, unsecure locations.
Rather, a dedicated server room or server closet that is locked at all
times is the most ideal environment for the purposes of server security.
Most hardware
manufacturers also include mechanisms for locking out some or all the
components of a server. Depending on the other layers of security
deployed, it may be wise to use these mechanisms to secure a server
environment.
Restricting Login Access
All
servers should be configured to allow only administrators to physically
log in to the console. By default, such use is restricted on systems
such as Active Directory domain controllers, but other servers such as
SharePoint servers and SQL servers must specifically forbid these types
of logins. To restrict login access, follow these steps:
1. | Choose Start, All Programs, Administrative Tools, Local Security Policy.
|
2. | In the left pane, navigate to Security Settings, Local Policies, User Rights Assignment.
|
3. | Double-click Allow Log On Locally.
|
4. | Remove any users or groups that do not need access to the server, as shown in Figure 1. Click OK when finished.
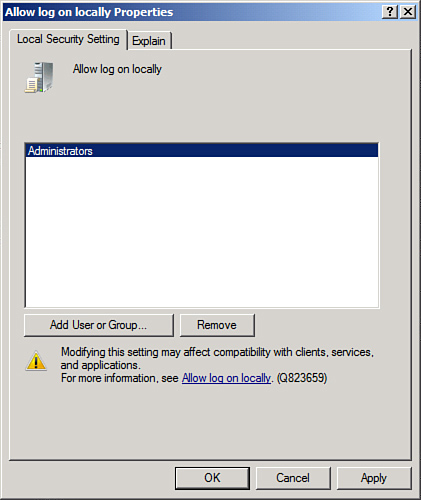
|
Note
A group policy set on an OU
level can be applied to all SharePoint servers, simplifying the
application of policies and negating the need to perform it manually on
every server.
Physically Securing SharePoint Access by Using Smartcards
The ultimate in secured
infrastructures utilizes so-called smartcards for login access; these
smartcards are fully supported in Windows Server. A smartcard is a
credit card-sized piece of plastic with an encrypted microchip embedded
within. Each user is assigned a unique smartcard
and an associated PIN. Logging in to a workstation is as
straightforward as inserting the smartcard into a smartcard reader and
entering the PIN, which can be a combination of numbers and letters,
similar to a password.
Security can be raised even
higher by stipulating that each smartcard be removed after logging in
to a console. In this scenario, users insert into the smartcard reader a
smartcard physically attached to their person via a string. After
entering their PIN, they log in and perform all necessary functions.
Upon leaving, they simply remove the smartcard from the reader, which
automatically logs them off the workstation. In this scenario, it is
nearly impossible for users to forget to log off because they must
physically detach themselves from the computer to leave.