FIM
is a very capable and powerful tool. With the right configuration and
some fancy scripting, it can be configured to perform an incredible
variety of automatic tasks. Today’s environments are rife with
directories, which increase the amount of administration required to
create accounts, delete accounts, and update user information manually.
FIM can greatly ease these requirements, improving administration and
security. The next section focuses on some of the most valuable
capabilities of FIM and how to effectively use them.
Managing Identities with FIM
FIM can be used for the most
basic and easiest configurations. For example, FIM can be used to
synchronize identity information between accounts in different
directories. Identity information could include names, email and
physical addresses, titles, department affiliations, and much more.
Generally speaking, identity information is the type of data commonly
found in corporate phone books or intranets. To use FIM for identity
management between Active Directory and an LDAP directory server, follow
these high-level steps:
1. | Install the Metadirectory services component of FIM.
|
2. | Create a management agent for each of the directories, including an Active Directory management agent and an LDAP agent.
|
3. | Configure the management agents to import directory object types into their respective connector namespaces.
|
4. | Configure
one of the management agents—for example, the Active Directory MA—to
project the connector space directory objects and directory hierarchy
into the metaverse namespace.
|
5. | Within
each of the management agents, a function can be configured called
attribute flow to define which directory object attributes from each
directory will be projected into the respective metaverse directory
objects. Configure the attribute flow rules for each management agent.
|
6. | Configure
the account-joining properties for directory objects. This is the most
crucial step because it will determine how the objects in each directory
are related to one another within the metaverse namespace. To configure
the account join, certain criteria such as an employee ID or first name
and last name combination can be used. The key is to find the most
unique combination to avoid problems when two objects with similar names
are located—for example, if two users named Tom Jones exist in Active
Directory.
|
7. | After
completely configuring the MAs and account joins, configure management
agent run profiles to tell the management agent what to perform with the
connected directory and connector namespace. For example, perform a
full import or an export of data. The first time the MA is run, the
connected directory information is imported to create the initial
connector namespace.
|
8. | After
running the MAs once, they can be run a second time to propagate the
authoritative metaverse data to the respective connector namespaces and
out to the connected directories.
|
These steps can be used to
simplify account maintenance tasks when several directories need to be
managed simultaneously. In addition to performing identity management
for user accounts, FIM can also be used to perform management tasks for
groups. When a group is projected into the metaverse namespace, the
group membership attribute can be replicated out to other connected
directories through their management agents. This allows a group
membership change to occur in one directory and be replicated to other
directories automatically.
Provisioning and Deprovisioning Accounts with FIM
Account provisioning in
FIM allows advanced configurations of directory management agents,
along with special provisioning agents, to be used to automate account
creation and deletion in several directories. For example, if a new user
account is created in Active Directory, the Active Directory MA could
tag this account. Then, when the respective MAs are run for other
connected directories, a new user account can be automatically generated
in those other accounts.
The provisioning and
deprovisioning process in FIM can be an extremely useful tool in
situations where automatic creation and deletion of user accounts is
required. For example, a single user account can be created in an HR
Oracle database, which can initiate a chain-event of account creations,
as illustrated in Figure 1.
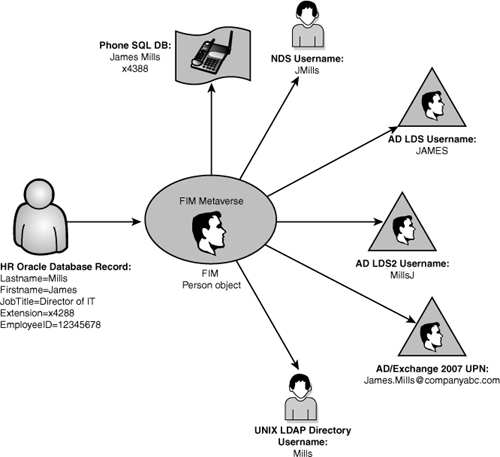
In
addition to creating these accounts, all associated accounts can be
automatically deleted or disabled through a deprovisioning process in
FIM. By automating this process, administration of the multitude of user
accounts in an organization can be simplified and the risk of
accidentally leaving a user account enabled after an employee has been
terminated can be minimized.
The following high-level
example demonstrates the steps required to set up simple account
provisioning. In this example, a connected AD DS domain is connected to
FIM. Any user accounts created in that domain have corresponding
Exchange mailboxes created in a separate Active Directory resource
forest:
1. | Install FIM.
|
2. | Configure a management agent for the connected AD DS domain.
|
3. | Configure the AD DS MA so that the attributes necessary to create a resource mailbox flow into the metaverse.
|
4. | Configure the attribute flow between the AD DS MA attributes and the FIM metaverse.
|
5. | Configure an additional MA for the AD DS Exchange Resource domain.
|
6. | Ensure
that the AD DS Exchange Resource MA attributes that FIM will need to
create the mailbox are set. These include the object types container,
group, inetOrgPerson, organizationUnit, and user.
|
7. | Using
Visual Studio, configure a custom Rules Extension DLL to provide for
the automatic creation of a mailbox-enabled user account in the resource
forest. In this case, the DLL must use the MVExtensionExchange class in the script.
|
8. | Install this rules extension DLL into the metaverse.
|
9. | Configure run profiles to import the information and automatically create the mailboxes.
|
The example described
previously, although complex, is useful in situations in which a single
Exchange Server forest is used by multiple organizations. The security
identifier (SID) of the AD DS account is imported into the metaverse and
used to create a mailbox in the resource forest that has the external
domain account listed as the Associated External Account. Through a
centralized FIM implementation, the Exchange resource forest can support
the automatic creation of resource mailboxes for a large number of
connected domains.