4. Blocking Pop-Ups
Some web pages contain pop-ups. A
pop-up is a subwindow that is displayed when you
access a web page. Sometimes pop-ups appear on top of the browser
window; other times they appear under the browser window. Because most
pop-ups contain ads or are otherwise unwanted content, Internet Explorer
blocks most types of pop-ups it recognizes by default in all security
zones, except the Local Intranet zone. This means Internet Explorer uses
the Pop-up Blocker when you are browsing sites on the public Internet,
trusted sites, and restricted sites, but does not use the Pop-up Blocker
when you access sites on your local network.
By default, when a pop-up is blocked, Internet Explorer displays a
message on the Information bar stating this. If you click the
Information bar and select Temporarily Allow Pop-ups, Internet Explorer
will allow pop-ups from the site until you navigate away from the page.
Alternatively, if you click the Information bar and select Always Allow
Pop-ups from This Site, Internet Explorer will configure the site as an
Allowed Site, and all pop-ups for the site will then be
displayed.
You can enable or disable pop-up blocking by completing the
following steps:
In Internet Explorer, click Tools→Internet Options. This
displays the Internet Options dialog box.
On the Privacy tab, select the Turn on Pop-up Blocker checkbox
to enable the Pop-up Blocker, or clear the Turn on Pop-up Blocker
checkbox to disable the Pop-up Blocker.
With pop-up blocking enabled, you can configure the way the Pop-up
Blocker works by completing the following steps:
In Internet Explorer, click Tools→Internet Options. This
displays the Internet Options dialog box.
On the Privacy tab, select Settings under Pop-up Blocker. This
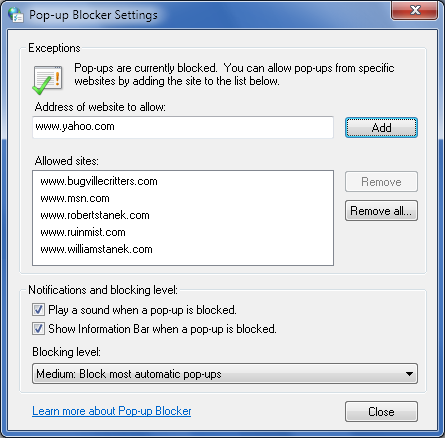
displays the Pop-up Blocker Settings dialog box shown in Figure 7-20.
You can use these options to add or remove allowed
sites:
- Add
To allow a site’s pop-ups to be displayed, type the
address of the site in the field provided, such as www.msn.com, and then click
Add. This site is then permitted to use pop-ups regardless of
Internet Explorer settings.
- Remove
To remove a site that is currently allowed to display
pop-ups, click the site address and then click Remove.
- Remove All
To remove all sites that are currently allowed to
display pop-ups, click Remove All. When prompted to confirm
the action, click Yes.
To stop playing a sound when a pop-up is blocked, clear “Play
a sound when a pop-up is blocked.”
To stop displaying an information message in the browser when
a pop-up is blocked, clear “Show Information Bar when a pop-up is
blocked.”
By default, most types of automatic pop-ups are blocked when
the Pop-up Blocker is enabled. You can use the following options of
the Blocking Level list to control the types of pop-ups that are
blocked:
- High: Block all pop-ups (Ctrl-Alt to override)
With this setting, Internet Explorer tries to block all
pop-ups. To temporarily override this setting, press Ctrl-Alt
while clicking a link to open a page and its related
pop-up.
- Medium: Block most automatic pop-ups
With this setting, Internet Explorer tries to block
pop-ups most commonly used to display ads or other unwanted
content. Some types of pop-ups are allowed. To override this
setting temporarily, press Ctrl-Alt while clicking a link to
open a page and its related pop-up.
- Low: Allow pop-ups from secure sites
With standard (HTTP) connections, Internet Explorer
attempts to block pop-ups most commonly used to display ads or
other unwanted content. With secure (HTTPS) connections,
Internet Explorer allows pop-ups.
Click Close and then click OK to save your settings.
5. Protecting Your Computer from Phishing
Phishing is a technique whereby a
site attempts to trick you into giving them personal information by
impersonating your bank or other trusted establishment that you have a
relationship with. Internet Explorer 8 includes SmartScreen filter, which is a phishing filter that is
designed to warn you about potential phishing sites and known phishing
sites. The warning is displayed on the Status bar as discussed
previously.
SmartScreen filter is active by default for all security zones,
except the Local Intranet zone. This means Internet Explorer uses the
phishing filter when you are browsing sites on the public Internet,
trusted sites, and restricted sites, but does not use the phishing
filter when you access sites on your local network.
The phishing filter is always on by default. In Internet Explorer,
you can turn off this feature by clicking Safety→SmartScreen Filter→Turn
Off SmartScreen Filter. You can then manually check sites if desired by
using the Check This Website option. If you suspect a site is
collecting personal information without your knowledge or consent, you
can report the site by using the Report Unsafe Website option. Keep in mind that you may
have granted implied consent to a site when you signed up to use a site,
or when you downloaded and installed a particular browser add-on or
related Internet software.