When you are browsing the Internet, Internet Explorer 8 runs in
Protected Mode. This isolates it from other applications in
the operating system and prevents add-ons from writing content in any
location beyond temporary Internet file folders without explicit user
consent. By isolating Internet Explorer from other applications and
restricting write locations, Windows 7 prevents many types of malicious
software from exploiting vulnerabilities on your computer. Protected Mode
also restricts the way domains, web addresses, and security zones are
used.Protected Mode is a key component in Internet Explorer’s
comprehensive safety and security suite, but many other safety and
security features work together to protect your computer from malicious
software. These additional security features include a pop-up blocker and
a phishing filter. They also include privacy and content settings.
1. Viewing and Managing Add-Ons
Protected Mode limits the ActiveX controls and other add-ons that
can run in Internet Explorer. Protected Mode also gives you better
control over the add-ons that are installed and used. Internet Explorer
organizes add-ons into four broad categories:
Toolbars and extensions
Search providers
Accelerators
InPrivate filtering
As I’ve already talked about search providers and filtering, I’ll
focus on toolbars, extensions, and accelerators. You manage these and
other add-ons using the dialog box shown in Figure 1. To access this dialog
box, click Tools→Manage Add-ons while working with Internet
Explorer.
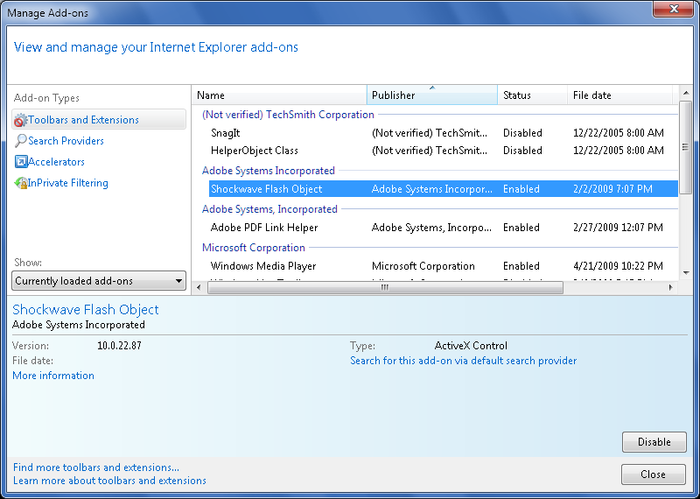
1.1. Configuring toolbars and extensions
When you select Toolbars and Extensions as the add-on type in the Manage
Add-ons dialog box, you can view and manage add-ons, in these unique
categories:
All add-ons
Lists all the add-ons that Internet Explorer has used
since you installed Windows or the latest version of Internet
Explorer.
Currently loaded add-ons
Lists the add-ons that Internet Explorer is currently
using.
Run without permission
Lists the add-ons configured for use on your
computer.
Downloaded controls
Lists the add-ons you’ve downloaded from the Internet and
configured for use.
In the “Run without permission” list, you’ll find default
add-ons that are included with Internet Explorer or that you’ve
downloaded through updates from Microsoft, as well as add-ons that you
have installed and granted permission to run. For example, if you
downloaded the ActiveX control for Flash and granted run permission to
this control, you’ll see it on the “Run without permission” list and
the “Downloaded controls” list. Although you can enable or disable any
ActiveX controls and other add-ons, you can delete only ActiveX
controls and other add-ons that you’ve downloaded.
Disabling and enabling add-ons is easy. Click the add-on you
want to work with. To disable the add-on, click “Disable” to prevent
the add-on from running in Internet Explorer. To enable the add-on,
click “Enable” to allow the add-on to run in Internet Explorer.
To remove an add-on, select the add-on by clicking it and then
click the “More information” link. In the More Information dialog box,
click Remove. When prompted to confirm that you want to delete the
add-on, click Yes. If the add-on has an entry in the Uninstall a
Program control panel, you should use that to remove it. This makes it
more likely that you will remove all trace of it.
Rather than disabling or deleting an add-on you’ve installed,
such as the Adobe Shockwave Flash Object, you can specify the websites
on which the control can run. To do this, select the add-on by
clicking it and then click the “More information” link. In the More
Information dialog box, you can configure the add-on so it can run on
all sites or only specific sites. To allow the add-on to run on all
sites when enabled, click “Allow on all sites.” To allow the add-on to
run only on specified sites, click “Remove all sites.” Next, to allow
the add-on to run, you’ll need to enable it and then when you visit
websites, you’ll need to allow it to run when prompted. This will
allow the add-on to run whenever you visit the website.
1.2. Configuring accelerators
Accelerators are a new feature in Internet Explorer 8
that help you quickly perform routine tasks without having to navigate
to other websites. To use accelerators, you highlight text on any web
page and then click the blue accelerator icon that appears above your
selection. You can then select one of the installed accelerators to
perform a specific task, such as:
Blog with Windows Live
E-mail with Windows Live
Map with Bing
Search with Bing
Translate with Bing
While you are working with the accelerator shortcut menu, you
can click All Accelerators to view additional accelerators that may be
available. If you click All Accelerators→Find More Accelerators,
you’ll open the Accelerators gallery in a new tab and be able to
browse for additional accelerators to install.
When you select “Accelerators” as the add-on type in the Manage
Add-ons dialog box, you can view and manage accelerators, as shown in
Figure 2.
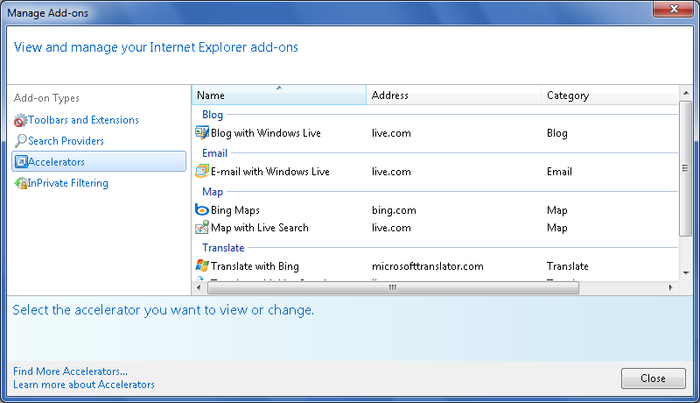
Each type of accelerator you can install has a specific
category. For example, the Blog with Windows Live accelerator is in
the Blog category. For each category, you can specify a default
accelerator to use in the Manage Add-ons dialog box. Click the
accelerator in the name list and then click “Set as default.” To stop
using an accelerator as the default, simply select another default for
the related category. Alternatively, you can click the accelerator in
the name list and then click “Remove as default.”
Disabling and enabling accelerators is easy. Click the
accelerator you want to work with. To disable the accelerator, click
Disable to prevent the accelerator from running in Internet Explorer.
To enable the accelerator, click Enable to allow the accelerator to
run in Internet Explorer.
To remove an accelerator, select the accelerator by clicking it
and then click Remove. When prompted to confirm that you want to
delete the accelerator, click Yes.