How to beat 2012’s web threats
(Part 2)
Mobile malware

Mobile phones are increasingly being targeted through SMS messages
or as they access the web. Parents buying smartphones for their children should
also be aware of what their offspring can do with them
- Probably more than you can. If you’re handing over a phone with
a limited data plan, note that apps accessing the web on demand can rack up
huge bills. Switch off the phone’s GPS function when it’s not needed
- This will also extend battery life. And avoid unsecured Wi-Fi
networks like the plague.
Recent research by Get Safe Online revealed just how fast
smartphone malware is growing. The government-backed body found an 800 percent
increase in the number of malware apps aimed at mobiles in just four months
(see tinyurl.com/czcp9c8).
Dodgy apps often appear in app stores as free versions or updated levels
for popular games and apps. Ring tones are another route of attack for malware
writers. Once downloaded to your phone, malicious apps might copy your
contacts, emails and saved passwords. Some even forward photographs taken by
your phone.
An emerging mobile scam secretly sends premium text messages from
your phone to a number owned by the fraudster.
Rik Ferguson, director at Get Safe Online and of security research
at Trend Micro. explains: “This type of malware is capable of sending a steady
stream of text messages to premium-rate numbers - in some instances, we’ve seen
a message sent every minute. With costs of up to £6 per message, this can be
extremely lucrative. The user won’t know this is taking place, even if they
happen to be using the device at the same time.”
App attack
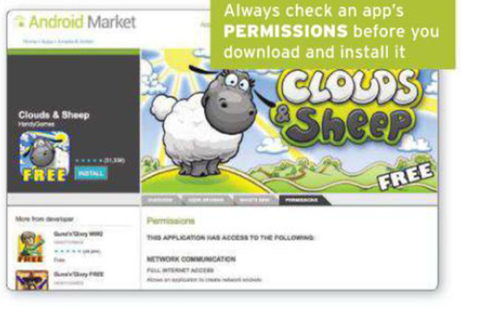
Another emerging trend for mobile devices is apps that snoop on
more information than you realise. Even official apps suck up an extraordinary
amount of information from your handset. How safe and well protected this data
is depends partly on the apps you install and partly on your faith in the app
developer concerned. Always read the details of what the app wilt have access to.
Research from Kaspersky Labs found large numbers of mobile malware
strains offered for sale in official app stores and elsewhere. Many users
believe anything they find in the Android Market, for example, is safe. The
reality is there are no such guarantees. Kasperksy’s boffins revealed a 30
percent hike in dodgy Android apps and found 34 percent of these had tried to
steal users’ personal data.
A big trend next year is likely to be scams that exploit a
smartphone’s GPS. As more people use genuine apps with location technologies,
the more scammers will follow.
The security industry is starting to take this market seriously,
but the scammers are already there. Independent researchers at AV-Test.org
looked at free Android antivirus apps and found 90 percent missed known malware
strains. Even paid-for apps from vendors such as Kaspersky and F-Secure
detected only 50 percent of dodgy software. This is a topic we’ll continue to
monitor.
Facebook and friends
Social networking’s primary danger is that you might give away
enough information about yourself to make identity theft possible. If your
profile includes your date of birth and address, an ID thief is well on his
way. A ‘happy birthday’ message to your mum could lead to her maiden name,
which is a common security question for many services.
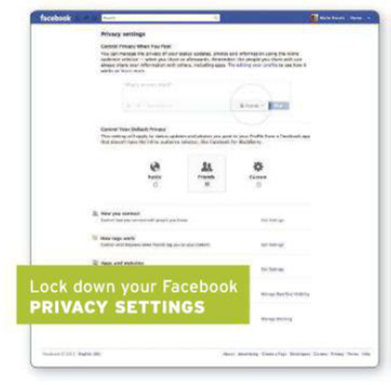
Start with the basics and dig into Facebook’s security and privacy
settings. Turn off everything, then start thinking about what you want to allow
rather than the other way around. Look again at what Information you are giving
away and who can see it.
Remember that your privacy depends on your friends, too. It
doesn’t matter how private your profile is if a friend with weak security
settings tags you in a picture.
Facebook is also increasingIy used as a medium for virus and spam
transmission.
Requests to join game networks or sharing platforms that
apparently come from friends might in fact come from criminals. Even if they
are genuine, it’s not imperative to accept the request and hand over more
information than you’re happy with.
Some of these services might be scams, but many exist to collect
your information and make money from selling it on. Be aware that it might be a
corporation rather than a hacker after your data, then consider what happens to
that information once it’s collected and whether it’s properly discarded when
it’s no longer needed.
Twitter is another service on which it’s all too easy to
over-share information. A rapper tweeted about his bling gold necklace and how
much he was looking forward to wearing it at his next gig. Someone saw the
tweets, went to that gig and relieved him of his chain. Burglary is nothing
new, but telling the world via Twitter when, for example, you’re going on
holiday, makes crooks’ lives much easier.