Open vs. limited access
The mobile device market continues to
evolve and consumers have access to more powerful technology than ever before.
Bob Hafner, managing vice president with Gartner (www.gartner.com), remembers a time when
“sophisticated” technology was “relatively expensive and generally not
affordable for the individual.” Then, people started buying home PCs, even
though they were less powerful than those they had at the office. However,
that’s not the case anymore. Consumers have more information to draw from and
feel more comfortable making technology decisions.

Consumerization
is “about the consumer deciding what they want in a device,”
When the moment came that smartphones went
past targeting business-people and widened their focus to the general public,
consumerization was born. Consumerization is “about the consumer deciding what
they want in a device,” says Hafner. And to help companies embrace
consumerization, they started creating BYOD (bring your own device) policies,
which “allow these devices in the workplace and give employees what they want,
while [companies] still have some modicum of control,” he says.
Employees simply want more control over the
devices they use in the workplace. But for many IT workers and administrators,
the influx of consumer devices could be viewed as a threat to their role in the
organization. The key to fully embracing consumerization and implementing
successful BYOD policies is to understand what your employees want and find
ways to fulfill those needs without making the organization vulnerable.
Prepare for a major culture change
Consumerization, which in its most basic
sense can be described as an educational renaissance in how consumers view
technology, flies in the face of traditional logic from an IT administrator
point of view. According to Paul DeBeasi, research vice president with Gartner,
employees are starting to believe that “they know what’s best for their job,”
whereas this used to be the role of the IT department. But instead of seeking
advice from IT experts, many consumers are forgoing a personal life and
business life separation in favor of blending the two together with mobile
devices.

Employees
are starting to believe that “they know what’s best for their job,”
“The first thing to overcome is the
cultural shock of employees telling IT what to do,” says DeBeasi. “That’s an
obstacle for many enterprises because for as long as personal computing has
been around, it has been the IT department for the most part being the experts,
being the most knowledgeable, making the rules, buying the equipment, deploying
it, and supporting it. That’s been their role in life, and for some of these IT
staff people it has been for decades. Now, that has been completely turned
upside down, so there’s sort of a cultural mindset that must be overcome, and I
wouldn’t underestimate that.”
The role of the IT administrator and of the
IT department as a whole is starting to shift away from total control to more
of a support role within the organization. “IT people are entrusted with
ensuring corporate information is not lost out in the public domain and that
there are no viruses or malware that get into the corporate environment that
can cause security issues,” says Hafner. And now that well-established
responsibility must apply to personal devices, to varying degrees.
Determine the level of support
BYOD is becoming a way of life, so it’s not
a matter of whether or not you’ll support consumerization and the influx of
employee-owned devices, it’s a matter of how much support you’ll provide.
DeBeasi says is starts with something as simple as determining whether or not
employees should be able to contact the help desk for personal device support,
but it doesn’t stop there. Executives and IT administrators need to work
together to decide what types of hardware, operating systems, and applications
should be allowed. You have to ask yourself whether you want to include support
for only enterprise apps or if you want to extend that support to personal
apps.

BYOD
is becoming a way of life
It used to be that email was one of the
only true business uses for mobile devices in the workplace, but that has
changed significantly thanks to the proliferation of productivity apps and the
increased performance of mobile networks. Employees can now use sales apps with
access to sensitive information, says Hafner. This is information that you
“don’t really want to get out to the public domain,” he says. So, de-pending on
the applications that you choose to support, you’ll need security and
management solutions in place to mitigate any risks.
You may already have what you need
If a majority of your employees or multiple
departments in your organization only use business email on their personal
devices, then you may already have sufficient tools in place that you weren’t
previously aware of. “At the very minimum, you have to use Exchange ActiveSync,
which allows you to enforce several policies on the device, so [you can]
remotely wipe the device if it’s lost or stolen,” says Hafner. ActiveSync also
provides password enforcement and other security features to help you get more
control over your employee’s devices in the workplace. And perhaps the best thing
about ActiveSync is that it is already built into Microsoft Exchange and is
free to use.
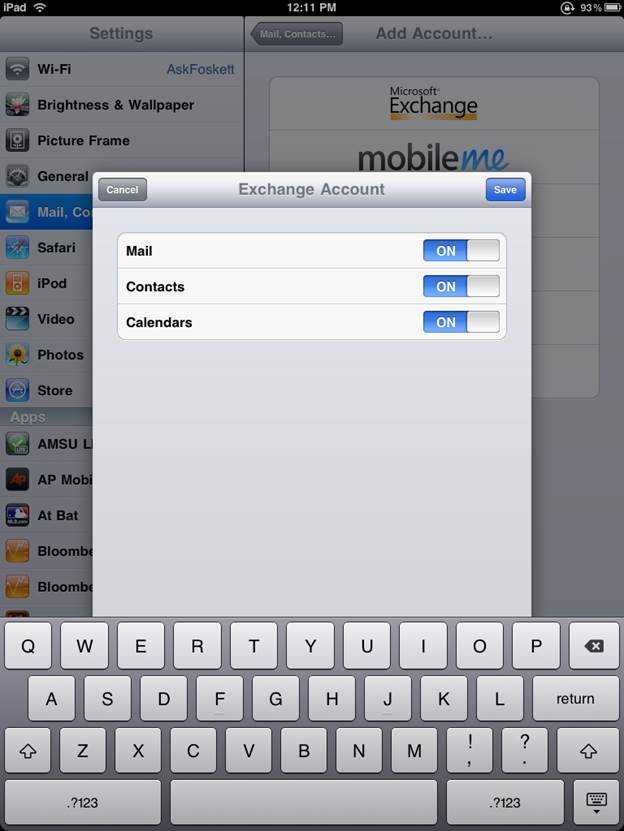
At the very minimum, you have to use
Exchange ActiveSync, which allows you to enforce several policies on the device
Hafner says that ActiveSync is “great for
email, and if you’re only allowing users to access email, then perhaps that’s
good enough for you right now.” The only problem with ActiveSync is that it
really only works for email, and most employees are going far beyond email in
terms of how they use their devices for business. Hafner says that email is
very well-understood and taken care of for the most part, but it’s with other
applications that companies need to consider the level of security they need to
fully protect devices and data.