4. IP Block and IP Allow Providers
Arguably, block list providers are one of the most
effective ways to prevent spam from reaching your users. The block list
is an effective way to block spam, but some mail administrators
consider block lists to be one step above evil incarnate. If you have
ever had one of your public IP addresses incorrectly listed on one of
these lists, you may sympathize with them since getting off some lists
can be challenging.
An IP block list provider is better known as a
real-time block list (RBL) provider. This is a service that keeps track
of known sources of spam, open relays, open proxies, IP addresses used
by dial-up connections, and IP addresses used by DHCP ranges. These are
all frequent sources of spam. Conversely, an IP allow list provider is
a service provider that maintains a list of IP addresses that are
likely not to send spam.
The most common configuration is an IP block list
provider. When an SMTP client connects to your Edge Transport (or Hub
Transport) server, the Edge Transport server issues a DNS query using
the reverse format of the IP address along with the DNS suffix of the
block list provider. For example, if an SMTP client at IP address
192.168.254.10 connects to an Edge Transport server, it will issue the
DNS query 10.254.168.192.zen.spamhaus.org if it is configured to use the Spamhaus ZEN list.
|
We are fans of block list providers (also known as
real-time block lists) and encourage our customers to use them. On
average, a typical block list, such as the Spamhaus ZEN list, will help
you cut in half or more the amount of spam that you receive.
In one particular situation, we used Exchange
Server's performance monitoring tools to determine how many messages
per day the Exchange Server content filter considered a spam confidence
level of 7 or higher. This particular organization was receiving nearly
40,000 messages per day that had an SCL of 7 or higher.
After enabling the IP block list provider to use the zen.spamhaus.org
block list, the average daily count of messages with an SCL of 7 or
higher dropped to 16,000. The messages identified by the RBL as spam
were dropped at the Hub Transport and were not transferred. This saved
on bandwidth as well as Hub Transport processing capacity.
|
If the IP address is not on the Spamhaus block list,
the DNS query will return a Host Not Found message. However, if the
entry is on a block list, the DNS query will return an IP address such
as 127.0.0.1, 127.0.0.2, and so on. The different return codes have
different meanings for different providers.
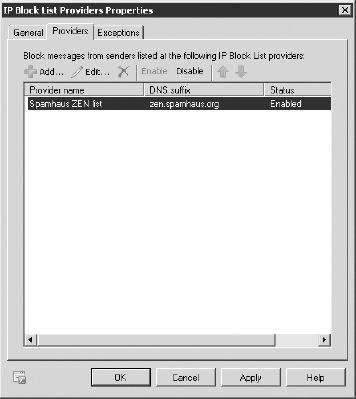
Figure 4 shows the IP Block List Providers Properties dialog; in this figure, one block list provider has been configured.
If you click the Add button, you can add RBL providers (there are none configured by default). Figure 5
shows part of the Add IP Block List Provider dialog box and the custom
error messages screen. The information that is required in the Add IP
Block List Provider dialog box is a name for the provider and the DNS
suffix or the lookup domain. You get the DNS suffix from the block list
provider.
When you add a new IP block list provider, you can
also configure it so that it responds only to certain error codes. This
could be useful, for example, if the provider returns different error
codes for different types of hosts and you only want to block mail for
certain error codes.
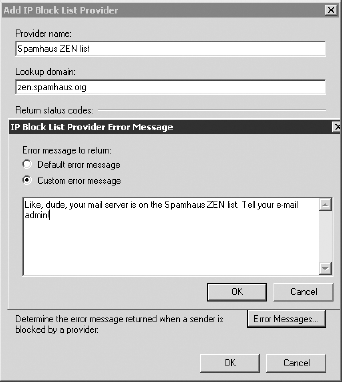
For each block list provider, you can configure a
custom error message. This can be useful for administrators whose
systems may be on a block list. We recommend configuring a message that
would be helpful for the administrator of a system from which you are
rejecting mail.
The Exceptions tab is useful if you want to specify SMTP addresses to which the RBL blocking should not apply.
A lot of RBL providers are available on the
Internet, and almost all are free. Some of these providers are pretty
accurate, and some are not. Some are more aggressive than others. The
more aggressive RBLs will often block entire IP subnets or entire IP
ranges from regions of the world. Other IP block lists make it
difficult to remove your IP address if you get on their list. Table 2
lists some of the RBLs we recommend using. We usually recommend
choosing two RBLs; in the table, they are listed in order of
preference. Our preference is to choose less aggressive RBLs and also
use other filtering technologies, such as content filtering or sender
reputation.
Table 2. Recommended IP Block List Providers
| Provider | Provider's Website | Provider's DNS Suffix |
|---|
| Spamhaus | www.spamhaus.org | zen.spamhaus.org |
| Composite Blocking List | cbl.abuseat.org | cbl.abuseat.org |
| SORBS | www.sorbs.net | dnsbl.sorbs.net |
| SpamCop | www.spamcop.net | bl.spamcop.net |