3. Control User Account Control
It
works like this: Windows Vista, like its predecessors, supports
different "levels" of user accounts, some with administrator
rights—necessary to install software and configure the system—and others
with lesser privileges. But Vista doesn't give administrators carte
blanche like Windows XP and 2000. Instead, an administrator (you, for
instance) operates in a more-restrictive standard
user account mode most of the time. Only when you make a change that
supposedly affects other users on your PC (whether there are any or
not), like installing a new hardware driver or changing Windows Firewall
settings, does Vista request your permission with the UAC prompt like
the one in Figure 9.
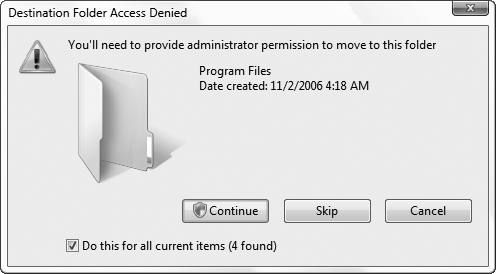
If you click Continue, Windows permits the action, and thereafter, it's smooth sailing. Or, click Cancel, and Windows forbids the request. As with any preventive measure, there are costs and benefits to Vista's UAC.
First, the good:
It can make Windows safer
In theory, nothing bad can happen to your PC without your approval. This means so-called drive-by installations
from nasty web sites you view in Internet Explorer, the source of some
spyware and adware, are a thing of the past (in theory).
It can make Windows more stable
Provided you take a few
extra steps, UAC makes it harder for incompetent users to damage a PC by
deleting or replacing files, making unauthorized changes to the
Registry, and screwing up network settings.
It can make Windows easier to administer
It's possible to require a
password at each UAC prompt, meaning a PC's administrator doesn't have
to create a separate account to make changes. The PC's day-to-day user
doesn't know the password and can't make changes, but the administrator
can sit down and fix a problem in minutes, without even logging out.
Now for the bad:
It breaks some programs
UAC may break software not
expressly written for Vista and the UAC feature. For instance, any
program that attempts to write files to the Program Files folder
(even its own application folder) will be denied access; this is why
lots of older applications can't save their settings on Vista, and some
programs can't start up or even be installed. And unless the software is
UAC-aware, it won't attempt to "elevate" itself to the administrator
level, and you'll never see the UAC prompt; Windows just denies it. In
short, you won't know why the program doesn't work.
It's annoying
(OK, this one should be
first, but that just seemed a bit self-serving.) How many times today
have you sat and watched your screen go black while you waited... and
waited... for the UAC prompt to appear? And have you noticed that some
features require two UAC prompts: one
that warns you that you're about to be asked for your permission, and
the other that actually makes the request? Couldn't Microsoft have found
a less cumbersome way to do this, such as a single window that elevates
the current session to administrator status for, say, the next 20
minutes?
It's easily defeated
The UAC feature can be
disabled with a single setting; it's only a matter of time before some
hacker figures out how to do this without you knowing about it. And if
you install software that registers a Windows service (managed with services.msc), that service could be used to carry out administrator-level requests by any program, even one run under the lowly standard user account.
Nobody reads prompts anyway
It's only a matter of time before an average PC user becomes accustomed to the prompt and gets into the habit of clicking Continue
without reading the message. Even if it were an otherwise flawless
system, there's no system in place to make sure the user knows what he
is doing.
When designing Windows Vista, Microsoft
tried to please everybody by making UAC strict enough to prevent certain
mischief, yet lenient enough that it wouldn't be such a nuisance that
you'd want to turn it off. Of course, the result is a system that is
either too much or not enough for most people. The solution, of course,
is to customize it.
3.1. Fix a program broken by UAC
So,
you've got a program that won't install on Vista, or perhaps it won't
remember its settings. The problem is likely that UAC is preventing the
application (or the installer) from doing what it was designed to do.
And since the application isn't UAC-aware, it doesn't request
"elevation," the step necessary to tell Windows that it's time for the
UAC prompt. The result? Vista prevents the change and keeps its mouth
shut, and the application doesn't work.
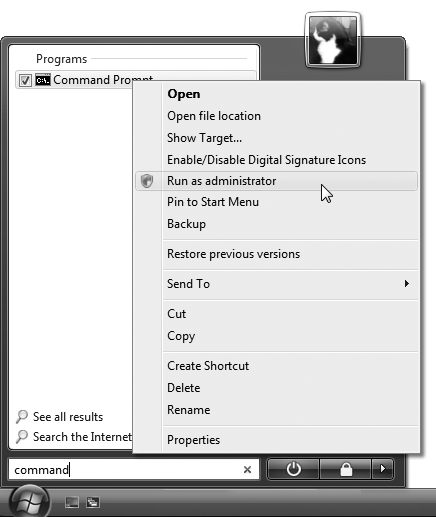
The solution is to elevate the application by hand. You can't do this while it's running, but, as shown in Figure 10,
you can do it when you start the application. Just right-click the
application's icon on your desktop or Start menu (or the program's .exe file), and select Run as administrator.
This time, you'll see the UAC prompt, and assuming you click Continue, Windows will elevate the application and it should work as designed.
If you don't see the Run as administrator
option, it means that the icon you've clicked isn't a standard Windows
shortcut. In this case, just open Windows Explorer, navigate to the
program's application folder (usually found under C:\Program Files), and right-click the main .exe file. Of course, Windows won't show the Run as administrator option when you right-click documents, so be sure you only do this with the main application icon. |
|
This
trick also works for application installers, but beware: if the
installer needs this workaround, the application is likely to need it,
too. Before you install, check the software publisher's web site for an
update or a new version that's compatible with Vista.
If the program won't run unless you use the Run as administrator feature, you may want to make the change more permanent. Right-click the program icon (or .exe file), select Properties, and choose the Compatibility tab. In the Privilege Level box, turn on the Run this program as an administrator option, and click OK.
3.2. Turn off User Account Control
The
easiest way to turn off UAC is through the User Accounts window in
Control Panel. On the "Make changes to your user account" page, click
the Turn User Account Control on or off link, and then turn off the Use User Account Control (UAC) to help protect your computer option.
But turning off UAC altogether isn't necessarily the best choice if you just want to get rid of the incessant UAC prompts.
If you're using the Ultimate or Business editions of Vista, open the Start menu Search box, type secpol.msc, and press Enter to display the Local Security Policy editor, shown in Figure 11.

Expand the Local Policies branch and click the Security Options folder. In the right pane, double-click the User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode setting. Here you have three choices:
Elevate without prompting.
This is the best choice if you want to skip the UAC window altogether.
Even
though this option gets rid of the UAC prompts, it does not disable
UAC. This means that applications that aren't UAC-aware won't request
elevation, and thus Vista will still block any changes it considers
dangerous. |
|
Prompt for credentials.
Use this to toughen
security on your PC by requiring a password each time. The UAC prompt
still appears, but the user can't click Continue if she doesn't know the password.
If
you're an administrator who's setting up this PC for someone else to
use, your best course of action is to give that person a standard account. Then, in the Local Security Policy editor, set the User Account Control: Behavior of the elevation prompt for standard users option to Prompt for credentials.
Prompt for consent.
This is the default in
Windows Vista. The UAC prompt appears every time an application requests
administrator-level access, but all you have to do is click Continue to permit the action.
As
you've probably noticed, there are at least nine different settings for
UAC here, and while most are fairly self-explanatory, there are a few
that deserve special attention.
Windows
Vista tries to automatically elevate most software installers to
administrator-level, which may not be such a great idea if you want to
cut your odds of a spyware infestation on your PC. If you've turned off
the UAC prompt as described above, then set the User Account Control: Detect application installations and prompt for elevation option to Disabled. Otherwise, if you've chosen to leave UAC prompts intact, you may want to set the User Account Control: Only elevate executables that are signed and validated option to Enabled.
Finally, see the "File and Registry Virtualization Explained" sidebar, next, for details on the User Account Control: Virtualizes file and registry write failures to per-user locations setting, and an explanation of something else that can break UAC-unaware programs.
Vista's UAC feature is designed to prevent changes to operating system folders like Program Files,
as well as protected areas of the Registry. If a program wasn't
designed with UAC in mind, it won't request elevation to
administrator-level access, and its attempt to, say, write to its own
application folder in Program Files will fail. Microsoft had to come up with a compromise that would allow some of these older programs to work. That compromise is virtualization, a system that redirects older (legacy,
as Microsoft puts it) applications to special, protected areas of your
hard disk and Registry. So, if a program with an auto-update feature
tries to write files to C:\Program Files\Acme Update\newversion.dll, Windows will instead send it to C:\Users\{your_username}\AppData\Local\VirtualStore\Program Files\Acme Update\newversion.dll. Likewise, if a program tries to make a change to the Registry, in the HKEY_ LOCAL_MACHINE\Software\Acme key, the change will be made instead to the HKEY_ CURRENT_USER\Software\Classes\VirtualStore\MACHINE\Software\Acme key. By default, your Program Files and Windows folders, and most of their subfolders, are protected, as well as almost all of the HKEY_LOCAL_MACHINE\Software branch in the Registry. UAC does not protect a user's own folder C:\Users\{your_username}\, nor does it lock out changes to the HKEY_CURRENT_USER\Software branch of the Registry. To turn virtualization off, set the User Account Control: Virtualizes file and registry write failures to per-user locations option in the Local Security Policy editor to Disabled.
But keep in mind that turning off virtualization won't, in itself,
permit older applications to write in these protected areas; instead, it
will cause more of your older programs to stop functioning, since
Windows will no longer give them a safe place to play. To see which of your running programs are subject to virtualization, right-click an empty area of your taskbar and select Task Manager. Choose the Processes tab, and then go to View → Select Columns. Turn on the Virtualization column, and then click OK. Now, in the Processes list, you'll see that some programs—particularly the older ones—have virtualization set to Enabled, as do explorer.exe and iexplore.exe (because of the danger of add-ons). UAC-aware programs will have virtualization set to Disabled, and programs already running as the administrator will have it set to Not Allowed. |