Web applications require the ability to restrict
access to their content, to protect sensitive resources, or to authorize
access to resources to specific users. IIS 7.0 provides an extensive
set of features that you can use to control the access to application
content. These features are logically divided into two categories, based
on the role they play in the process of determining access to the
request resource:
Authentication
Authentication features serve to determine the identity of the client
making the request, which can be used in determining whether this client
should be granted access.
Authorization
Authorization features use the authenticated identity on the request or
other applicable information to determine whether or not the client
should be granted access to the requested resource. Authorization
features typically depend on the presence of authentication features to
determine the authenticated identity. However, some authorization
features determine access based on other aspects of the request or the
resource being requested, such as Request Filtering.
IIS 7.0 supports
most of the authentication and authorization features available in IIS
6.0, and it introduces several additional features. These features (role
services) are listed here in the order in which they apply during the
processing of the request:
1. | IP and Domain Restrictions.
Used to restrict access to requests clients make from specific IP
address ranges or domain names. The default install does not use this
feature.
|
2. | Request Filtering.
Similar to UrlScan in previous versions of IIS, request filtering is
used to restrict access to requests that meet established limits and do
not contain known malicious patterns. In addition, Request Filtering is
used to restrict access to known application content that is not meant
to be served to remote clients. Request filtering is part of the default
IIS 7.0 install and is configured to filter requests by default.
|
3. | Authentication features.
IIS 7.0 offers multiple authentication features that you can use to
determine the identity of the client making the request. These include
Basic Authentication, Digest Authentication, Windows Authentication
(NTLM and Kerberos), and many others. The Anonymous Authentication feature is part of the default IIS install and is enabled by default.
|
4. | Authorization features.
IIS 7.0 provides a new URL Authorization feature that you can use to
create declarative access control rules in configuration to grant access
to specific users or roles. In addition, it continues to support NTFS
ACL-based authorization for authentication schemes that yield Windows
user identities. IIS uses NTFS ACL-based authorization by default.
|
Note
In
IIS 7.0, all of these role services are available as Web server modules
that can be individually installed and uninstalled and optionally
disabled and enabled for each application. Be careful when removing
authentication, authorization, and other access control modules, because
you may unintentionally open access to unauthorized users or make your
application vulnerable to malicious requests. To review the list of
security-sensitive modules that ship with IIS 7.0, and considerations
when removing them. |
You should leverage
access control features to ensure that only users with the right to
access those resources can access them. To do this, you need to
configure the right authentication and authorization features for your
application.
In addition, you
should take advantage of Request Filtering to limit usage of the
application as much as is possible, by creating restrictions on content
types, URLs, and other request parameters. Doing so enables you to
preemptively protect the application from unexpected usage and unknown
exploits in the future.
IP and Domain Restrictions
The IP and
Domain Restrictions role service enables you to restrict access to your
application to clients making requests from a specific IP address range
or to clients associated with a specific domain name. This feature is
largely unchanged from IIS 6.0.
Note
The
IP and Domain Restrictions role service is not part of the default IIS
install. You can manually install it from the IIS \ Security feature
category in Windows Setup on Windows Vista, or from the Security
category of the Web Server (IIS) role in Server Manager on Windows
Server 2008.
|
You can use this feature
to allow or deny access to a specific range of IP addresses, or to a
specific domain name. The IP and Domain Restrictions role service will
attempt to match the source IP address of each incoming request to the
configured rules, in the order in which rules are specified in
configuration. If a matching rule is found, and the rule is denied
access to the request, the request will be rejected with a 403.6 HTTP
error code. If the rule allows access, the request will continue
processing (all additional rules will be ignored).
You
can specify any number of allow or deny rules and indicate whether
access should be granted or denied if no rules match. The common
strategies for using IP Address and Domain Restrictions rules include:
Denying access
by default and creating an Allow rule to grant access only to a
specific IPv4 address range, such as the local subnet. You can do this
to grant access only to clients on the local network or to a specific
remote IP address.
Allowing
access by default and creating a Deny rule to deny access to a specific
IP address or IPv4 address range. You can do this to deny access to a
specific IP address that you know is malicious.
Caution
Allowing
access by default and denying access for specific IP address ranges is
not a secure technique, because attackers can and often will use
different IP addresses to access your application. Also, clients that
use IPv6 addresses instead of the IP addresses will not match a Deny
rule that uses an IPv4 address range. |
If you are looking to
restrict access to your application to clients on the local network, you
may be able to implement an additional defense measure by specifying
that your site binding should listen only on the IP address associated
with the private network. For servers that have both private and public
IP addresses, this can restrict requests to your site to the private
network only. You should use this in conjunction with IP and Domain
Restrictions where possible.
Though you can create
rules that use a domain name instead of specifying an IP address, we
don’t recommend that you do so. This is because domain name-based
restrictions require a reverse Domain Name System (DNS) lookup of the
client IP address for each request, which can have a significant
negative performance impact on your server. By default, the feature does
not enable the use of domain name–based rules.
To configure the IP and Domain Restrictions rules, you will need to perform the following steps:
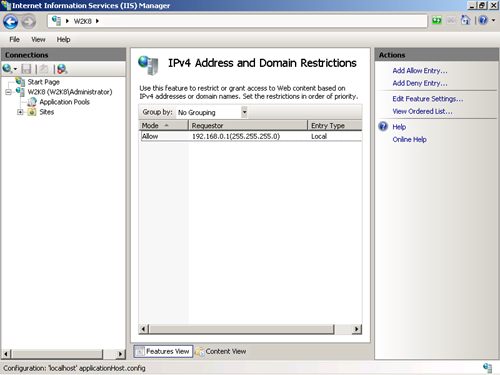
1. | Use
IIS Manager to configure the rules by selecting the Server node, a Site
node, or any node under the site in the tree view. Then double-click
the IP Address And Domain Restrictions feature, which is shown in Figure 1.
|
2. | Use the Add Allow Entry or the Add Deny Entry command in the Actions pane to create allow or deny rules.
|
3. | You
can also use the Edit Feature Settings command to configure the default
access (allow or deny) and whether or not domain name–based rules are
allowed.
|
Note
Although
the IP and Domain Restrictions feature enables you to use IPv6
addresses, you cannot configure addresses that use IPv6 rules using IIS
Manager. Also, requests that are made over IPv6 connections do not match
rules using IPv4 addresses. Likewise, requests made over IPv4
connections do not match rules that specify IPv6 addresses. |
Note
By default, the ipSecurity configuration section is locked at the server level. You can unlock this section by using the Appcmd Unlock Config command to specify IP and Domain Restriction rules in web.config files at the site, application, or URL level. |
You can also configure the IP and Domain Restrictions configuration by using Appcmd or configuration APIs to edit the system.webServer/security/ipSecurity configuration section.