We look at some of the ways in which
you can become invisible while online
There’s little doubt that the current focus
of security and snooping in the world press is, for story of the century. Our
increasing digital communications make an easy target for government agencies
and nefarious hackers. Let's face it, how many of us are actively taking
measures to be anonymous? It's not a new concept, by any stretch of the
imagination. There have been umpteen Hollywood movies in which the so-called
evil security agencies have targeted an individual and accessed their entire
digital life and, of course, there have been whistle-blowing individuals who
have surfaced in a storm of publicity before being silenced into submission. As
long as we use some kind of traceable form of communication, then there will
groups who will attempt to access and infiltrate that communication. whether
for outright hacking purposes or under the thin veil of anti-terrorism.

How
to be completely Anonymous online?
We're not going to discuss the various
political and ethical issues related to this; that's for a different feature
altogether. Of course, governments bodies and private organizations should not
be spying on us all at, but the fact remains that they do. Therefore, we need
to do something that will make their jobs a little more difficult. We're not
saying that you can be totally anonymous; such a thing is virtually impossible
(although doable, if you know how to manipulate IP addresses and so on). The
resources the groups on the other side of the digital line have are effectively
limitless, but what we can do is attempt to make our online communications
somewhat more clandestine but not in an illicit sense.
Before we show you how to do this, it's
worth mentioning a quote from Google's CEO, Eric Schmidt: "If you have
something that you don't want anyone to know, maybe you shouldn't be doing it
in the first place." In a way, that's a fair comment, but I have a problem
with it. Yes, I totally agree that unscrupulous individuals who are planning to
harm others do need to be caught, but I do not believe that the government has
the right to store all our personal and digital information. It should not be
able to freely access any of my digital history or read/ analyze any digital
communications between me and any of my contacts. I have nothing to hide (in
fact I'm actually very digitally boring compared to some people), but I'd like
to think that what I say privately to another person remains private.

Becoming
Anonymous
It's also worth mentioning that,
realistically, the sheer volume of digital information travelling through the
ether is in the order of 144 billion emails per day, and of the supposed 2.4
billion internet users worldwide. It's hardly likely that a team of analysts,
hidden deep in some bunker in GCHQ (Government Communications Headquarters),
are going through it all with a fine-toothed comb. Even with the best software
ever devised, the resources needed to meter every person are far beyond the
capabilities of the government. In most cases, they are targeting the
individuals and groups who have already been thoroughly investigated or who
frequently send digital communications with certain keywords in the body (the
old wives tale of mentioning a combination of president, bomb and the Middle
East during a telephone conversion may have more clout than you would imagine).
Also, those who regularly visit certain tagged websites that contain
information that may be deemed as dangerous or under the current anti-terrorism
act will no doubt be under strict surveillance. Therefore, it's doubtful that
you or I or any other 'normal' person on the street will be under the scrutiny
of secret government agencies.
That said, though, there are also groups
who are not affiliated with some Machiavellian one world order. These are the
hackers, phishers and other disreputable organizations who will try to gain
access to your accounts, online information and contacts in order to scam you
in every conceivable way. Those are the people whose attention we should
concentrate on avoiding when online.
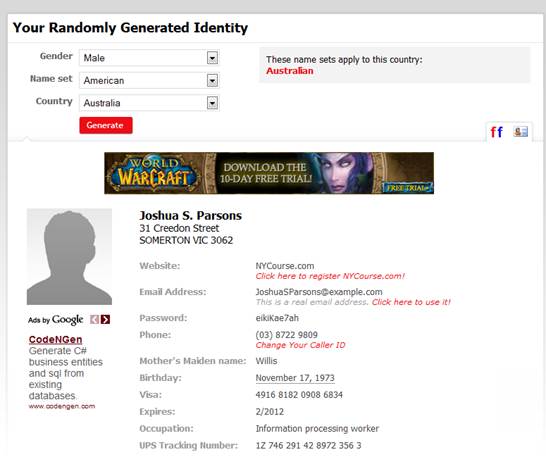
Create
a totally fake alias to use online
Becoming anonymous, the basics
Before we go into the more selective
processes of encryption and using any third-party tools or utilities, we'll
start with some of the basics of becoming anonymous online, keeping your
privacy and avoiding spammers and scammers as much as possible.
Be incognito
Private browsing mode or 'Incognito' mode
is a feature that has rapidly become the second most used option in current web
browsers. Despite its alternative name, 'porn mode', private browsing
functionality is useful for more than just looking at sites of scantily clad
ladies (or, indeed, gents). It's also perfectly acceptable for instances where
you could be on another user's computer and you want to check your Facebook,
Twitter or online mail accounts. Similarly, it's perfect for testing sites that
are heavily laden with cookies, and it's good for those times when you're using
a public computer or even on your home PC and you don't want any sites knowing
where you've previously been.
Private browsing isn't totally fingerprint-free;
items such as DNS lookups and certain cookies can stay behind after a private
browsing session, so it's best to treat private browsing as a temporary,
perhaps on-the- go mode of being anonymous. If you want to see a good example
of this, open up a private browsing session and browse through a number of
sites, then exit the session, drop into a Command Prompt and enter the
following command:
ipconfig
/displaydns
This will list all the cached DNS entries
that your computer has visited, regardless of whether you used a private
browsing session or not. To remove the entries, enter the following:
ipconfig
/flushdns
way, the list will be clear and attempts to
gain access to that list will be thwarted. A good idea could be to set up a
batch file of some description, one that would launch the browser in private
browsing mode, then when closed will automatically flush the DNS entries. It's
not 100% anonymity, but it can be used to retain a certain level of privacy.