Digital gold: passwords and mail
addresses
Hackers who struck gold in the hunt for
user accounts hold the most valuable digital product in their hands: passwords.
These passwords are not just keys to unlimited data from the personal accounts
of the victims. In many cases they also open doors to more user accounts:
Google, Amazon, PayPal, mail services and many more.
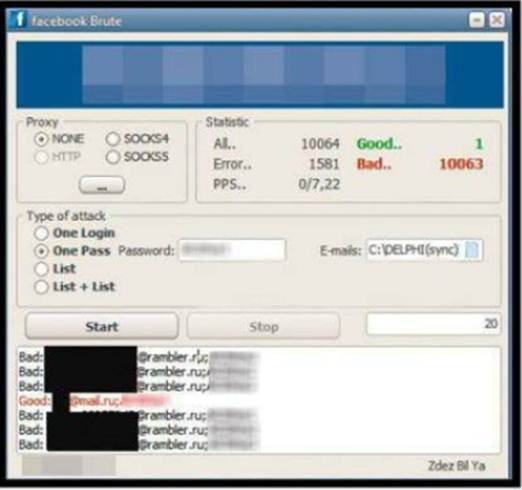
Attackers
can actually hack user accounts by using authentic password-crackers like this
one.
Various surveys undertaken in the last few
years show that more than half of web users use the same password for several
(¡f not all) of their user accounts. A single password can be worth up to $200,
contrary to the value in cents of pure, unadulterated personal user data. This
was revealed in the process of a court battle between two Kuwaiti Billionaires,
wherein one of them instructed the Chinese hacker group, "Invisible
Hacking Group", to crack open the password of the other.
This business-related case shows that Social
Hacking threatens not just the private user, but also into other areas. This is
also claimed in a recently published study by the security service provider
Imperva. This study perceives companies and government organisations as the
ones fuelling such attacks. There can also be a threat to human lives if, for
example, details of planned military operations are inadvertently revealed in
the open on the social networks.
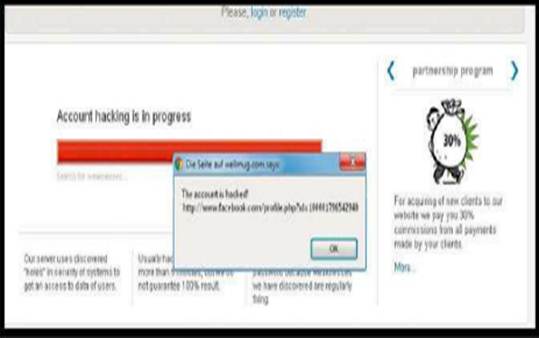
Social
Hacking is so popular that many of its rip-offs also exist, used by the hacker to
fool people.
This happened in an Israeli military
mission in March 2010. The mission had to be called off when a soldier divulged
the time and place of the mission by an update on Facebook. It sparked fears
within the military of a possible counter-attack triggered by this information.
Similarly, it can pose a problem for
companies when an employee publishes internal details on his personal profile
on social networks. It can be information related to the personnel structure,
when his official position in the company is posted on the network (or even on
career related networks like Xing). Information from closed user groups on
Facebook which are used by companies as discussion platforms can also be the
target. Such data can rarely be of real value, particularly on the black
market. But it can be the basis for further and more Social Engineering attacks
with a higher potential of causing harm.
When the hacker gains control of a user
profile, he or she can use this identity to attack more users - without using a
password bypass at all! The security loophole that the hacker makes use of is
the implicit trust of the user and the gullibility of other users, either known
or unknown. The biggest strength of Facebook, according to the hackers, now
reveals itself here: whoever sees a link or video posted on Facebook, does not,
as a rule, think about where it has originated from.
The Bait: "Like" buttons
Symantec's security expert Stefan Wesche
says that "Like- baiting" is the prevailing, most employed method.
The hacker sends links as baits in the form of posts, chat or direct
notifications under the assumed identity of the hacked user. These links refer
users mostly to fan pages which, for example, promise users a gif: voucher upon
becoming a "fan" of that page. The coupon can be provided simply by
clicking on the "Like" button. That is followed by a survey to be
taken by the user through which provides the hacker with more personal
information about the user. This enables the hacker to make more money. "That's
because, as an intermediary, the hacker earns a commission from anywhere
between 20 cents to $50, depending on the amount of the information and its
scope. This commission is paid by the survey provider", says Stefan
Wesche. Social networks are also very lucrative for blackmailers.
The unrestricted behaviour of users on the
social network is very gainful for blackmailers! In February, a US student was
threatened by an alleged Facebook friend from England. He threatened to publish
a private video of the victim if he was not paid $500. In another case, a
Californian man has racked the email passwords of hundreds of women. What
helped him was the "forgotten password" function of email services
wherein he could answer the security questions with the helpful information
from the victim's Facebook profiles (like the favourite colour or the second
name of the father). He blackmailed some women with the photos found in the
email accounts, partially naked photos, or directly mailed these photos to the
email contacts of the victims. This hacker also used some mail addresses to
reset the Facebook password and hijack these accounts.
Hackers who are active on Facebook under
the victims' identities enjoy a great benefit which was not available in Social
Engineering before the advent of Facebook. Earlier, such attacks took place
over telephone calls using false names.
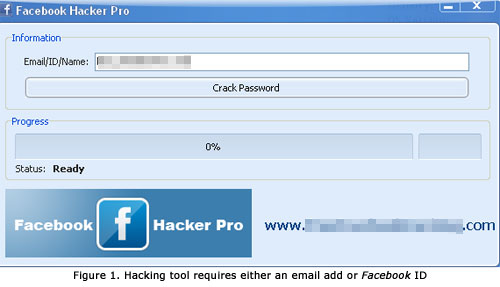
Hackers
who are active on Facebook under the victims' identities enjoy a great benefit
which was not available in Social Engineering before the advent of Facebook
The hacker had to react in real time, had
to have a convincing story which he had to convey without the slightest bit of
hesitation. On the other hand, Facebook enables him to take more time to react
to notifications or chat at his own leisure. He utilises this time to
investigate deeper into the victim's personal information and think up a good
answer. Stefan Schumacher says, "This asynchronism in communication is one
of the biggest advantages available to hackers on Facebook".
Given these conditions, Facebook shall
remain a much preferred target of hackers even in the future - with newer
attack strategies. Schumacher says that Spear-phishing can be the next step.
Spear-phishing are targeted phishing attacks - based on psychological profiles
- which will be automatically drawn up on from Facebook. Facebook has set up a
team of around 300 security engineers and an analysis system which will
supervise the network against these attacks. For this purpose, Facebook
collaborated with security firms McAfee, Sophos, Symantec and Trend Micro at
the end of April this year to effectively filter such dangerous links. However,
each person can, on his own, cover these security loopholes with disciplined
user behaviour, and by nursing a healthy distrust towards contents and people
on the social networks.