4. Advanced Firewall Configuration
It's for more advanced users and network and
security administrators who might need to configure Windows Firewall to
comply with an organization's security policy. All these options
require administrative privileges. I don't go into great detail on what
the various options mean because I assume you are working to comply with
an existing policy.
|
If you're
not a professional administrator, it's best to stay out of this area
altogether. You certainly don't want to guess and hack your way through
things just to see what happens. Doing so could lead to a real can of
worms that makes it impossible or extremely difficult to access the
Internet.
|
|
4.1. Open the Windows Firewall with Advanced Security Icon
To get to the advanced
configuration options for Windows Firewall, first open Windows Firewall
from the System and Security item in the Control Panel. Then click the
Advanced Settings link in the left pane. Or press  , type fire, and click Windows Firewall with Advanced Security. The Firewall console, shown in Figure 8, opens.
, type fire, and click Windows Firewall with Advanced Security. The Firewall console, shown in Figure 8, opens.
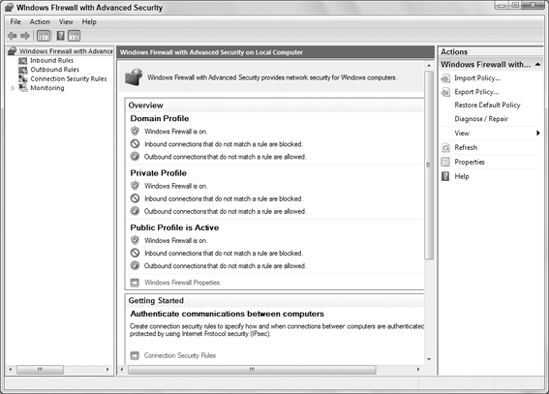
As you can see in
the figure, you have three independently configurable profiles to work
with. The Domain Profile is active when the computer is logged in to a
domain. The Private Profile applies to computers within a local, private
network. The Public Profile protects your computer from the public
Internet.
4.2. Changing Firewall Profile Properties
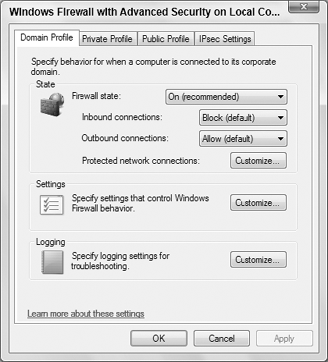
Clicking the Windows Firewall
Properties link near the bottom of the console (or the Properties item
in the Actions pane) takes you to the dialog box shown in Figure 9.
Notice that you can use tabs at the top of the dialog box to configure
the Domain, Private, and Public settings. The fourth option applies to
IPsec (IP Security), commonly used with VPNs (Virtual Private Networks),
described a little later in this section. By default, Inbound
connections are set to Block and Outbound ports are set to Allow. You
can change either setting by clicking the appropriate button.
4.2.1. Firewall alerts, unicast responses, local administrator control
Each profile tab has a
Customize button in its Settings section. Clicking that button provides
an option to turn off firewall notifications for that profile.
Administrators can also use options on that tab to allow or prevent
unicast responses to multicast and broadcast traffic. There's also an
option to merge local administrator rules with rules defined through
group policy.
4.2.2. Security logging
Each profile tab also
offers a Logging section with a Customize button. Click the Customize
button to set a name and location for the log file, a maximum size, and
to choose whether you want to log dropped packets, successful
connections, or both. You can use that log file to review firewall
activity and to troubleshoot connection problems caused by the firewall
configuration.
7.4.2.3. Customizing IPsec settings
|
Contrary to some
common marketing hype and urban myths, having outbound connections set
to Allow by default does not make your computer more susceptible to
security threats. Firewalls are really about controlling traffic between
trusted and untrusted networks. The Internet is always considered
untrusted because it's open to the public and anything goes. It's
necessary to block inbound connections by default so that you can
control exactly what does, and doesn't, come in from the Internet.
Things that are already
inside your computer (or local network) are generally considered
"trusted." That's because, unlike the Internet, you do have control over
what's inside your own PC or network. Your firewall and antimalware
programs also help to keep bad stuff out. Therefore, you shouldn't need
to block outbound connections by default.
There are exceptions, of
course. In a secure setting in which highly sensitive data is confined
to secure workstations in a subnet, it certainly makes sense to block
outgoing connections by default. That way, you can limit outbound
connections to specific hosts, programs, security groups, and so forth.
You can also enforce encryption on outbound connections.
|
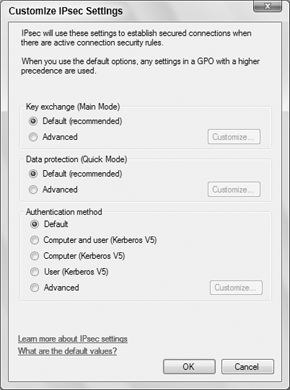
The IPsec Settings tab in the
firewall properties provides a way to configure IPsec (IP Security).
Clicking the Customize button under IPsec Defaults reveals the options
shown in Figure 10.
The Default settings in each case cause settings to be inherited from a
higher-level GPO (Group Policy Object). To override the GPO, choose
whichever options you want to apply to the current Windows Firewall
instance. When you override the default, you can choose key exchange and
data integrity algorithms. You can also fine-tune Kerberos V5
authentication through those settings.
Clicking OK or Cancel
in the Customize IPsec Settings dialog box takes you back to the IPsec
Settings tab. There you can use the IPsec Exemptions section to exempt
ICMP from IPsec, which may help with connection problems caused by ICMP
rules.
NOTE
IPsec is a set of
cryptographic protocols for securing communications across untrusted
networks. It is commonly associated with tunneling and virtual private
networks (VPNs).
That covers the
main firewall properties. You can configure plenty more outside the
Properties dialog box. Again, most of these go far beyond anything the
average home user needs to be concerned with, so I'm being brief here.
Advanced users needing more information can find plenty of information
in the Help section for the firewall.
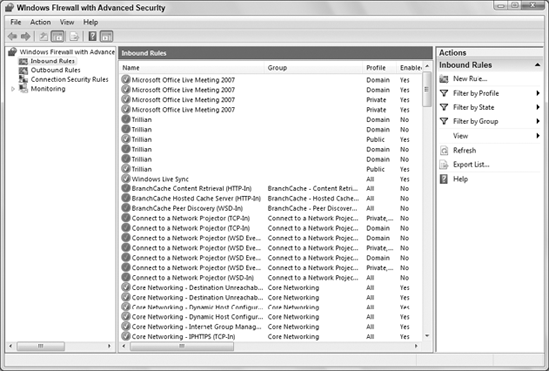
4.3. Inbound and Outbound Rules
In the left column of the main Windows Firewall with Advanced Security window shown back in Figure 7,
you see Inbound Rules and Outbound Rules links. These provide very
granular control over Windows Firewall rules for incoming and outgoing
connections. Figure 11 shows a small portion of the possibilities there. Use scroll bars to see them all.
5. Wrap-Up
A firewall is an important
component of a larger overall security strategy. Windows 7 comes with a
built-in firewall that's turned on and working from the moment you first
start your computer. The firewall is automatically configured to
prevent unsolicited Internet traffic from getting into your computer,
thereby protecting you from worms and other hack attempts. The 7
firewall also provides advanced options for professional network and
security administrators who need more granular control over its
behavior. In summary:
A firewall protects your computer from unsolicited network traffic, which is a major cause of worms and other hack attempts.
A firewall will not protect your computer from viruses, pop-up ads, or junk e-mail.
You
don't need to configure the firewall to use standard Internet services
such as the Web and e-mail. Those will work through the firewall
automatically.
When
you start an Internet program that needs access to the Internet through
a closed port, you'll be given a security alert with options to
Unblock, or Keep Blocking, the port. You must choose Unblock to use that
program.
Windows
Firewall is one of the programs in the Security Center. To open
Security Center, click the Start button and choose Control Panel => Security => Security Center.
From the Start menu, you can search on the keyword fire to get to Windows Firewall configuration options.
Exceptions in Windows Firewall are programs that are allowed to work through the firewall.
Professional
network and security administrators can configure Windows Firewall
through the Windows Firewall with Advanced Security console in
Administrative Tools.