NTFS permissions are always evaluated when a file
is accessed. NTFS permissions are fairly complex, and to understand
their management, you need to understand the following:
-
Basic permissions What the basic permissions are and how they are used
-
Special permissions What the special permissions are and how they are used
-
Ownership What is meant by file ownership and how file ownership is used
-
Inheritance What is meant by inheritance and how inheritance is used
-
Effective permissions How to determine the effective permissions on files
Understanding and Using the Basic Permissions
In Windows Vista, the owner of a file or a folder
has the right to allow or deny access to that resource, as do members
of the Administrators group and other authorized users. Using Windows
Explorer, you can view the currently assigned basic permissions by
right-clicking a file or a folder, selecting Properties on the shortcut
menu, and then selecting the Security tab in the Properties dialog box.
As shown in Figure 1,
the Group Or User Names list shows all the users and groups with
permissions set for the selected resource. If you select a user or a
group in this list, the assigned permissions are shown in the
Permissions For list. If permissions are shaded (unavailable), as shown
in the figure, it means they have been inherited from a parent folder.
Working with and Setting Basic Permissions
All permissions are stored in the file system as
part of the access control list (ACL) assigned to a file or a folder.
As described in Table 1,
six basic permissions are used with folders and five are also used with
files. Although some permissions are inherited based on permissions of
a parent folder, all permissions are defined explicitly at some level
of the file system hierarchy.
Table 1: Basic File and Folder Permissions
|
Permission
|
Description
|
|
Full Control
|
Grants the user or group full control over the
selected file or folder and permits reading, writing, changing, and
deleting files and subfolders. A user with Full Control over a folder
can change permissions, delete files in the folder regardless of the
permission on the files, and can also take ownership of a folder or a
file. Selecting this permission selects all the other permissions as
well.
|
|
Modify
|
Allows the user or group to read, write, change,
and delete files. A user with Modify permission can also create files
and subfolders but cannot take ownership of files. Selecting this
permission selects all the permissions below it.
|
|
Read & Execute
|
Permits viewing and listing files and subfolders
as well as executing files. If applied to a folder, this permission is
inherited by all files and subfolders within the folder. Selecting this
permission selects the List Folder Contents and Read permissions as
well.
|
|
List Folder Contents (folders only)
|
Similar to the Read & Execute permission but
available only for folders. Permits viewing and listing files and
subfolders as well as executing files. Unlike Read & Execute, this
permission is inherited only by subfolders but not by files within the
folder or subfolders.
|
|
Read
|
Allows the user or group to view and list the
contents of a folder. A user with this permission can view file
attributes, read permissions, and synchronize files. Read is the only
permission needed to run scripts. Read access is required to access a
shortcut and its target.
|
|
Write
|
Allows the user or group to create new files and
write data to existing files. A user with this permission can also view
file attributes, read permissions, and synchronize files. Giving a user
permission to write to but not delete a file or a folder doesn't
prevent the user from deleting the folder or file's contents.
|
Equally
as important as the basic permissions are the users and groups to which
you assign those permissions. If a user or a group whose permissions
you want to assign is already selected in the Group Or User Names list
on the Security tab, you can modify the assigned permissions using the
Allow and Deny columns in the Permissions For list. Select check boxes
in the Allow column to add permissions, or clear check boxes to remove
permissions.
To expressly forbid a user or a group from using a
permission, select the appropriate check boxes in the Deny column.
Because denied permissions have precedence over other permissions, Deny
is useful in two specific scenarios:
-
If a user is a member of a group that has been
granted a permission, you don't want the user to have the permission,
and you don't want to or can't remove the user from the group, you can
override the inherited permission by denying that specific user the
right to use the permission.
-
If a permission is inherited from a parent folder
and you'd rather a user or a group not have the inherited permission,
you can override the allowed permissions (in most cases) by expressly
denying the user or group the use of the permissions.
If users or groups whose permissions you want to assign
aren't already available in the Group Or User Names list on the
Security tab, you can easily add them. To set basic permissions for users or groups not already listed on a file or a folder's Security tab, follow these steps:
-
On the Security tab, click Edit. This displays the Permissions For … dialog box.
-
In the Permissions For … dialog box, click Add to display the Select Users Or Groups dialog box, shown in Figure 2.
Figure 2: Use Select Users, Computers, or Groups to specify the groups whose permissions you want to configure.
| Tip |
Always double-check the value of the From This
Location field. In workgroups, computers will always only show local
accounts and groups. In domains, this field is changeable and set
initially to the default (logon) domain of the currently logged on
user. If this isn't the location you want to use for selecting user and
group accounts to work with, click Locations to see a list of locations
you can search, including the current domain, trusted domains, and
other resources that you can access.
|
-
Type the name of a user or a group account in the
selected or default domain. Be sure to reference the user account name
rather than a user's full name. When entering multiple names, separate
them with semicolons.
-
Click Check Names. If a single match is found for
each entry, the dialog box is automatically updated as appropriate and
the entry is underlined. Otherwise, you'll see an additional dialog
box. If no matches are found, you've either entered an incorrect name
part or you're working with an incorrect location. Modify the name in
the Name Not Found dialog box and try again, or click Locations to
select a new location. When multiple matches are found, select the
name(s) you want to use in the Multiple Names Found dialog box and then
click OK. The users and groups are added to the Name list.
-
You can now configure permissions for each user
and group you added by selecting an account name and then allowing or
denying access permissions as appropriate.
Special Identities and Best Practices for Assigning Permissions
When you work with basic
permissions, it is important to understand not only how the permissions
are used but also how special identities can be used to help you assign
permissions. The special identities you'll see the most are Creator
Owner and Users, but others are also used occasionally, as described in
Table 2.
Table 2: Special Identities Used When Setting Permissions
|
Special Identity
|
Description
|
|
Anonymous Logon
|
Includes any network logons for which credentials
are not provided. This special identity is used to allow anonymous
access to resources, such as those available on a Web server.
|
|
Authenticated Users
|
Includes users and computers who log on with a
user name and password; does not include users who log on as Guest,
even if the Guest account is assigned a password.
|
|
Creator/Owner
|
The special identity for the account that created
a file or a folder. Windows Vista uses this group to identify the
account that has ultimate authority over the file or folder.
|
|
Dialup
|
Includes any user who accesses the computer with
a dial-up connection. This identity is used to distinguish dial-up
users from other types of users.
|
|
Everyone
|
Includes all interactive, dial-up, and
authenticated users. Although this group includes guests, it does not
include anonymous users.
|
|
Interactive
|
Includes any user logged on locally or through a remote desktop connection.
|
|
Network
|
Includes any user who logs on over the network.
This identity is used to allow remote users to access a resource and
does not include interactive logons that use remote desktop connections.
|
|
Users
|
Includes authenticated users and domain users only. In Windows Vista, the built-in users group is preferred over everyone.
|
A solid understanding of these special identities can
help you more effectively configure permissions on NTFS volumes.
Additionally, whenever you work with permissions, you should keep the
following guidelines in mind:
-
Follow the file system hierarchy Inheritance plays
a big part in how permissions are set. By default, permissions you set
on a folder apply to all files and subfolders within that folder. With
this in mind, start at the root folder of a local disk or a user's
profile folder (both of which act as top-level folders) when you start
configuring permissions.
-
Have a plan Don't set permissions without a clear
plan. If permissions get out of sync on folders, and you are looking
for a way to start over so that you have some continuity, you might
want to configure the permissions as they should be in
a parent folder and then reset the permissions on all subfolders and
files in that folder.
-
Grant access only as necessary An important aspect
of the file access controls built into NTFS is that permissions must be
explicitly assigned. If you don't grant a permission to a user and that
user isn't a member of a group that has a permission, the user doesn't
have that permission—it's that simple. When assigning permissions, it
is especially important to keep this rule in mind because it's tempting
just to give users full control rather than the specific permissions
they really need. Granting only the specific permissions users need to
do their job is known as the principle of least privilege.
-
Use groups to manage permissions more efficiently
Whenever possible, you should make users members of the appropriate
groups and then assign permissions to those groups rather than
assigning permissions to individual users. In this way, you can grant
permissions to new users by making them members of the appropriate
groups, and then, when a user leaves or goes to another group, you can
change the group membership as appropriate. For example, when Sarah
joins the sales team, you can add her to the SalesUS and SalesCan
groups so that she can access those groups' shared data. If she later
leaves the sales team and joins the marketing team, you can remove her
from the SalesUS and SalesCan groups and add her to the MarketingUS and
MarketingCan groups. This is much more efficient than editing the
properties for every folder Sarah will need access to and assigning
permissions.
Assigning Special Permissions
Windows Vista uses special permissions to
carefully control the permissions of users and groups. Behind the
scenes, whenever you work with basic permissions, Windows Vista manages
a set of related special permissions that specify exactly the permitted
actions. The special permissions that are applied for each of the basic
permissions are as follows:
Table 3 describes how Windows Vista uses each special permission.
Table 3: Special Permissions for Files and Folders
|
Special Permission
|
Description
|
|
Traverse Folder /Execute File
|
Traverse Folder allows direct access to a folder
in order to reach subfolders, even if you don't have explicit access to
read the data it contains. Execute File allows you to run an executable
file.
|
|
List Folder /Read Data
|
List Folder lets you view file and folder names. Read Data allows you to view the contents of a file.
|
|
Read Attributes
|
Allows you to read the basic attributes of a file or a folder. These attributes include Read-Only, Hidden, System, and Archive.
|
|
Read Extended Attributes
|
Allows you to view the extended attributes (named data streams) associated with a file.
|
|
Create Files /Write Data
|
Create Files allows you to put new files in a
folder. Write Data allows you to overwrite existing data in a file (but
not add new data to an existing file, because this is covered by Append
Data).
|
|
Create Folders /Append Data
|
Create Folders allows you to create subfolders
within folders. Append Data allows you to add data to the end of an
existing file (but not to overwrite existing data, because this is
covered by Write Data).
|
|
Write Attributes
|
Allows you to change the basic attributes of a
file or a folder. These attributes include Read-Only, Hidden, System,
and Archive.
|
|
Write Extended Attributes
|
Allows you to change the extended attributes (named data streams) associated with a file.
|
|
Delete Subfolders and Files
|
Allows you to delete the contents of a folder. If
you have this permission, you can delete the subfolders and files in a
folder even if you don't specifically have Delete permission on the
subfolder or the file.
|
|
Delete
|
Allows you to delete a file or a folder. If a
folder isn't empty and you don't have Delete permission for one of its
files or subfolders, you won't be able to delete it. You can delete a
folder that contains other items only if you have Delete Subfolders And
Files permission.
|
|
Read Permissions
|
Allows you to read all basic and special permissions assigned to a file or a folder.
|
|
Change Permissions
|
Allows you to change basic and special permissions assigned to a file or a folder.
|
|
Take Ownership
|
Allows you to take ownership of a file or a
folder. By default, administrators can always take ownership of a file
or a folder and can also grant this permission to others.
|
In
Windows Explorer, you can view special permissions for a file or a
folder by right-clicking the file or the folder you want to work with
and then selecting Properties. In the Properties dialog box, select the
Security tab and then click Advanced to display the Advanced Security
Settings dialog box, as shown in Figure 3.
In this dialog box, the permissions are presented much as they are on
the Security tab. The key differences are that you see individual allow
or deny permission sets along with whether and how the permissions are
inherited, as well as the resources to which the permissions will apply.
Once
you've accessed the Advanced Security Settings dialog box, you can set
special permissions using the Add, Edit, and Remove buttons. To add a
user or a group and then set special permissions for that user or
group, follow these steps:
-
On the Security tab, click Advanced to display the Advanced Security Settings dialog box.
-
On the Permissions tab, click Edit. This opens the Advanced Security Settings dialog box for editing.
-
Click Add. This displays the Select User Or Group dialog box.
-
Type the name of a user or a group account in the
selected or default domain. Be sure to reference the user account name
rather than a user's full name. Only one name can be entered at a time.
-
When you click OK, the Permission Entry For … dialog box, shown in Figure 4, is displayed.
Figure 4: Configure the special permissions that should be allowed or denied.
-
Allow or deny special permissions as appropriate.
If any permissions are shaded (unavailable), they are being inherited
from a parent folder. You can override the inherited permission if
necessary by selecting the opposite permission, such as Deny rather
than Allow.
-
If the options on the Apply Onto list are
available, choose the appropriate options to ensure the permissions are
properly inherited. The options include the following:
-
q This Folder Only The permissions will apply only to the currently selected folder.
-
q This Folder, Subfolders And Files The permissions will apply to this folder, any subfolders of this folder, and any files in any of these folders.
-
q This Folder And Subfolders
The permissions will apply to this folder and any subfolders of this
folder. They will not apply to any files in any of these folders.
-
q This Folder And Files The permissions will apply to this folder and any files in this folder. They will not apply to any subfolders of this folder.
-
q Subfolders And Files Only
The permissions will apply to any subfolders of this folder and any
files in any of these folders. They will not apply to this folder
itself.
-
q Subfolders Only The
permissions will apply to any subfolders of this folder but will not
apply to the folder itself or any files in any of these folders.
-
q Files Only The
permissions will apply to any files in any of these folders and any
files in subfolders of this folder. They will not apply to this folder
itself or to subfolders.
-
When you are finished configuring permissions, click OK.
File Ownership and Permission Assignment
The owner of a file or a folder has the right to
allow or deny access to that resource. Although members of the
Administrators group and other authorized users also have the right to
allow or deny access, the owner has the authority to lock out
non-administrator users and then the only way to regain access to the
resource is for an administrator or restore operator to take ownership
of it. This makes the file or folder owner important in terms of what
permissions are allowed or denied with respect to a given resource.
The default owner of a file or a folder is the person
who created the resource. Ownership can be taken or transferred in
several different ways. A current owner of a file or a folder can
transfer ownership to another user or group at any time. A member of
the Administrators group can take ownership of a file or a folder or
transfer ownership to another user or group at any time—even if they
are locked out of the resource according to the permissions. Any user
with the Take Ownership permission on the file or the folder can take
ownership, as can any member of the Backup Operators group (or anyone
else with the Restore Files And Directories user right, for that
matter).
Taking Ownership of Files and Folders
If
you are an administrator, an authorized user, or a backup operator, you
can take ownership of a file or a folder by completing the following
steps:
-
In Windows Explorer, access the file or folder's
Properties dialog box by right-clicking the file or folder and then
selecting Properties.
-
On the Security tab, click Advanced to display the Advanced Security Settings dialog box.
-
On the Owner tab, click Edit. This opens the Advanced Security Settings dialog box for editing, as shown in Figure 5.
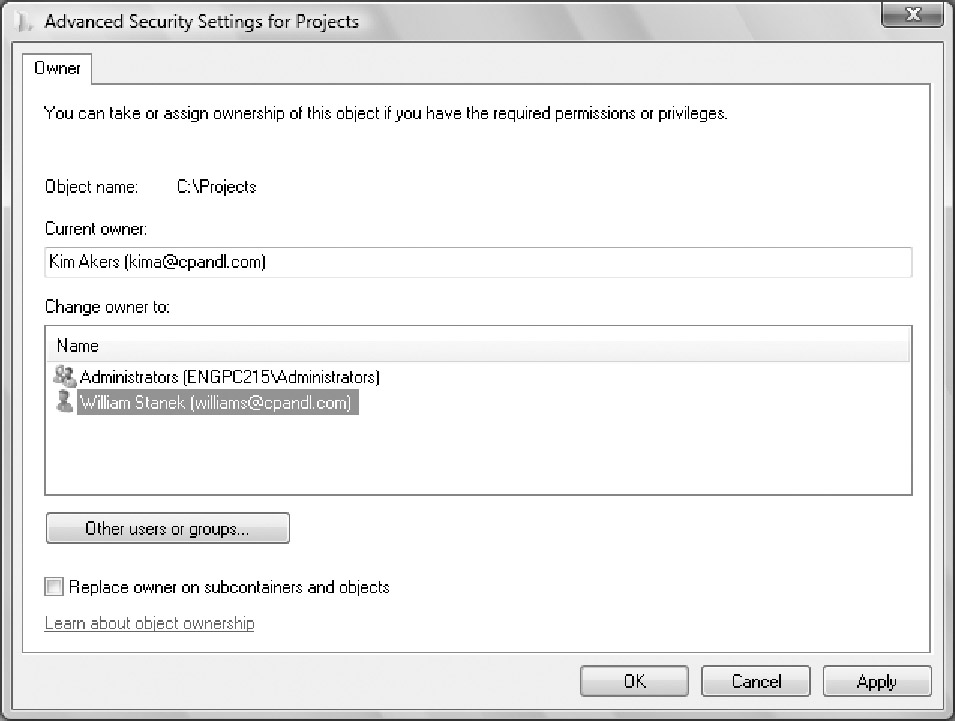
Figure 5: Use the Owner tab to take ownership of a file or a folder.
-
In the Change Owner To list box, select the new
owner. If you're taking ownership of a folder, you can take ownership
of all subfolders and files within the folder by selecting the Replace
Owner On Subcontainers And Objects option.
-
Click OK twice when you are finished.
Assigning Ownership
If you are an administrator or the current owner
of a file, you can assign ownership of a file or a folder to another
user or group by completing these steps:
-
In Windows Explorer, access the file or folder's
Properties dialog box by right-clicking the file or folder and then
selecting Properties.
-
On the Security tab, click Advanced to display the Advanced Security Settings dialog box.
-
On the Owner tab, click Edit. This opens the Advanced Security Settings dialog box for editing.
-
Click Other Users Or Groups to display the Select User Or Group dialog box.
-
Type the name of a user or a group and click
Check Names. If multiple names match the value you entered, you'll see
a list of names and will be able to choose the one you want to use.
Otherwise, the name will be filled in for you, and you can click OK to
close the Select User Or Group dialog box.
-
In the Change Owner To list box, select the new
owner. If you're assigning ownership of a folder, you can assign
ownership of all subfolders and files within the folder by selecting
the Replace Owner On Subcontainers And Objects option.
-
Click OK twice when you are finished.
Applying Permissions Through Inheritance
In the file and folder hierarchy used by Windows Vista, the root folder of a local disk and the %UserProfile%
folder are the parent folders of all the files and folders they contain
by default. Any time you add a resource, it inherits the permissions of
the local disk's root folder or the user's profile folder. You can
change this behavior by modifying a folder's inheritance settings so
that it no longer inherits permissions from its parent folder. This
would create a new parent folder, and any subfolders or files you added
would then inherit the permissions of this folder.
Inheritance Essentials
Inheritance is automatic, and inherited
permissions are assigned when a file or a folder is created. If you do
not want a file or a folder to have the same permissions as a parent,
you have several choices:
-
Stop inheriting permissions from the parent folder and then copy or remove existing permissions as appropriate.
-
Access the parent folder and configure the permissions you want all included files and folders to have.
-
Try to override an inherited permission by selecting the opposite permission. In most cases, Deny overrides Allow.
Inherited permissions are shaded (unavailable) on the
Security tab of a file or a folder's properties dialog box. It is also
important to note that when you assign new permissions to a folder, the
permissions propagate down to the subfolders and files contained in
that folder and either supplement or replace existing permissions. This
propagation lets you allow additional users and groups to access a
folder's resources or to further restrict access to a folder's
resources independently of a parent folder.
To better understand inheritance, consider the following examples:
-
On drive C, you create a folder named Data and
then create a subfolder named CurrentProjects. By default, Data
inherits the permissions of the C:\ folder, and these permissions are
in turn inherited by the CurrentProjects folder. Any files you add to
the C:\, C:\Data, and C:\Data\CurrentProjects folders will have the
same permissions—those inherited from the C:\ folder.
-
On drive C, you create a folder named Docs and
then create a subfolder named Working. You stop inheritance on the
Working folder by removing the inherited permissions of the parent. Any
files you add to the C:\Docs\Working folder inherit the permissions of
the C:\Docs folder and no other.
-
On drive C, you create a folder named Backup and
then create a subfolder named Sales. You add permissions to the Sales
folder that grant access to members of the Sales group. Any files added
to the C:\Backup\Sales folder inherit the permissions of the C:\ folder
and also have additional access permissions for members of the Sales
group.
| Real World |
Many new administrators wonder what the advantage
of inheritance is and why it is used. Although it occasionally seems
inheritance is more trouble than it's worth, inheritance enables you to
very efficiently manage permissions. Without inheritance, you'd have to
configure permissions on every file and folder you created. If you
wanted to change permissions later, you'd have to go through all your
files and folders again. With inheritance, all new files and folders
automatically inherit a set of permissions. If you need to change
permissions, you can make the changes in a top-level or parent folder
and the changes can be automatically applied to all subfolders and
files in that folder. In this way, a single permission set can be
applied to many files and folders without editing the security of
individual files and folders.
|
Viewing Inherited Permissions
To view the inherited permissions on a file or a
folder, right-click the file or folder in Windows Explorer and then
select Properties. On the Security tab of the Properties dialog box,
click Advanced to display the Advanced Security Settings dialog box,
shown previously in Figure 3.
The Permission column lists the current permissions assigned to the
resource. If the permission is inherited, the Inherited From column
shows the parent folder from which the permission has been inherited.
If the permission will be in turn inherited by other resources, the
Apply To column shows the types of resources that will inherit the
permission.
Stopping Inheritance
If you want a file or a folder to stop inheriting permissions from a parent folder, follow these steps:
-
In Windows Explorer, right-click the file or folder and then select Properties. On the Security tab, click Advanced.
-
On the Permissions tab, click Edit. This opens the Advanced Security Settings dialog box for editing.
-
Clear Include Inheritable Permissions From This Object's Parent.
-
As shown in Figure 6,
you now have the opportunity to copy over the permissions that were
previously applied or remove the inherited permissions and apply only
the permissions that you explicitly set on the folder or file. Click
Copy or Remove as appropriate. Assign additional permissions as
necessary.
| Tip |
If you remove the inherited permissions and there
are no other permissions assigned, everyone but the owner of the
resource will be denied access. This effectively locks everyone except
the owner out of a folder or file. However, administrators still have
the right to take ownership of the resource regardless of the
permissions. Thus, if an administrator was locked out of a file or a
folder and truly needed access, she could take ownership and then have
unrestricted access.
|
Restoring Inherited Permissions
Over time, the permissions on files and
subfolders can become so dramatically different from those of a parent
folder that it is nearly impossible to effectively manage access. To
make it easier to manage file and folder access, you might want to take
the drastic step of restoring the inherited permissions to all
resources contained in a parent folder. In this way, subfolders and
files get all inheritable permissions from the parent folder, and all
other explicitly defined permissions on the individual subfolders and
files are removed.
To restore the inherited permissions of a parent folder, follow these steps:
-
In Windows Explorer, right-click the file or folder and then select Properties. On the Security tab, click Advanced.
-
On the Permissions tab, click Edit. This opens the Advanced Security Settings dialog box for editing.
-
Select Replace All Existing Inheritable Permissions and click OK.
-
As shown in Figure 7,
you will see a prompt explaining that this action will replace all
explicitly defined permissions and enable propagation of inheritable
permissions. Click Yes.
Determining the Effective Permissions and Troubleshooting
NTFS permissions are complex and can be difficult
to manage. Sometimes a change—even a very minor one—can have unintended
consequences. Users might suddenly find they are denied access to files
they could previously access, or they might suddenly find they have
access to files to which access should never have been granted. In
either scenario, something has gone wrong with permissions. You have a
problem, and you need to fix it.
You should start troubleshooting these or other
problems with permissions by determining the effective permissions for
the files or the folders in question. As the name implies, the
effective permissions tell you exactly which permissions are in effect
with regard to a particular user or group. The effective permissions
are important because they enable you to quickly determine the
cumulative set of permissions that apply.
For a user, the effective permissions are based on all
the permissions the user has been granted or denied, no matter whether
they were applied explicitly or obtained from groups of which the user
is a member. For example, if JimB is a member of the Users, Sales,
Marketing, SpecTeam, and Managers groups, the effective permissions on
a file or a folder would be the cumulative set of permissions that JimB
has been explicitly assigned and those permissions assigned to the
Users, Sales, Marketing, SpecTeam, and Managers groups.
To determine the effective permissions for a user or a group with regard to a file or a folder, complete the following steps:
-
In Windows Explorer, right-click the file or
folder you want to work with and then select Properties. In the
Properties dialog box, select the Security tab and then click Advanced
to display the Advanced Security Settings dialog box.
-
To determine effective permissions that are
applied to a user or a group, click the Effective Permissions tab,
click Select, type the name of the user or group, and then click OK.
-
The Effective Permissions for the specified user
or group are displayed using the complete set of special permissions.
If a user has full control over the selected resource, he or she will
have the permissions, as shown in Figure 8.
Otherwise, you'll see a subset of permissions selected and you'll have
to carefully consider whether the user or group has the appropriate
permissions. Use Table 3 to help you interpret the permissions.
| Note |
You must have appropriate permissions to view the
effective permissions of any user or group. It is also important to
remember that you cannot determine the effective permissions for
implicit groups or special identities, such as Authenticated Users or
Everyone. Furthermore, the effective permissions do not take into
account those permissions granted to a user because he or she is the
Creator Owner.
|
|