3. Assessing and Assigning Role Scope
You can see what access has been granted to
individual roles by expanding the Components section of the COM+
application display. You can see which roles
have been granted access to the SecurityProTracker
component by right-clicking on the component icon, picking the
Properties menu item, and selecting the Security tab, illustrated by
Figure 7.
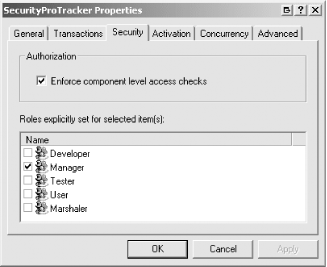
You will see that the Manager role is checked, meaning that user
accounts assigned this role are permitted to access all of the
members defined by the SecurityProTracker
component. If you expand the Interfaces item, you will see a list of
the interfaces that the SecurityProTracker
component implements; most of these are created by the COM+ system
automatically. Expanding the IDefectTracker item
lists the individual methods defined by our functional interface,
shown by Figure 8.
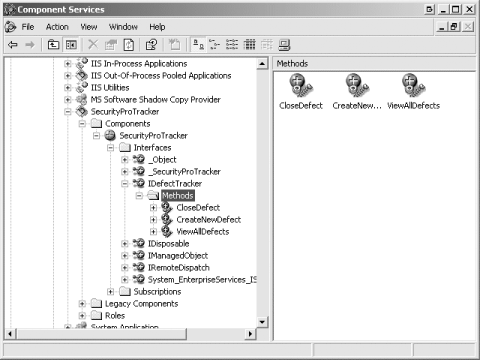
You can see which roles are granted access to a specific method by
right-clicking on a method icon, selecting the Properties menu item
and choosing the Security tab from the properties window; Figure 9 shows the roles granted access to the
ViewAllDefects method.
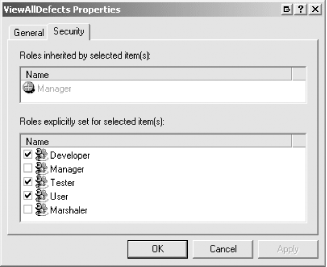
You will see that the Developer, Tester, and User roles are checked,
indicating that they are granted explicit access to this method. The
Manager role is listed in the Roles inherited by selected items(s)
section, because the role was assigned to a parent object—in
this case, to the component itself, which has the effect of
implicitly granting access to all of the members defined by the
interfaces it implements.
You can change the role configuration for a component by adding or
removing check marks from the Security property page. For example, if
you were to uncheck the Tester role for the
ViewAllDefetcs method, the Tester role would have
no access to any of the methods defined by the
SecurityProTracker component, because the
ViewAllDefects method was the only one to which
you applied the Tester role.
COM+ allows both the component developer and the system administrator
to manage the scope and application of RBS. In effect, this means
that the configuration provided by the component developer provides
an "out of the box" baseline
configuration, which can be adapted to provide a customized
configuration by the system administrator. It falls to the component
developer to provide clear documentation explaining the baseline
configuration and the effect of altering it. It falls to the system
administrator to read this documentation and consider carefully the
impact of making changes to the RBS configuration.
4. Managing COM+ Security
4.1. Managing the application
Figure 10
illustrates
the Security properties for our COM+ application example, which you
can view by right-clicking on the application icon, choosing the
Properties menu item, and clicking on the Security tab. These
properties specify the settings for the security of the entire COM+
application, which applies to all of the components in the
application. The options displayed in this window are equivalent to
the functionality provided by the
ApplicationAccessControl attribute.
The Enforce access checks for this application check box (indicated
by the number 1 in Figure 10), enabling and
disabling RBS and PAS at the application level, equivalent to the
Value property; bear in mind that access controls
must also be enabled individually for the components within the
application. The Security Level radio buttons (indicated by the
number 2 in Figure 10) specify whether PAS or PAS
and RBS will be enabled for the application; this is equivalent to
the AccessChecksLevel property.
The Authentication Level for Calls and Impersonation Level
combination boxes (indicated by the numbers 3 and 4 in Figure 10) are equivalent to the Authentication and
ImpersonationLevel properties; the drop-down list
contains the definitions represented by the
AuthenticationOption and
ImpersonationLevelOption enumerations.
4.2. Managing the component
Figure 11
illustrates the security properties for our
serviced component, which you can obtain by right-clicking on the
component icon, choosing the Properties menu item, and clicking on
the Security tab. These properties specify the security settings for
the component, and each component within a COM+ application can be
configured individually.
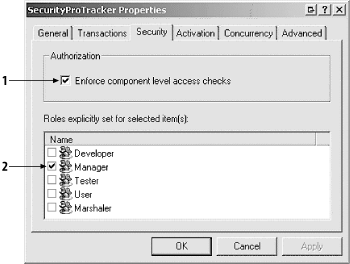
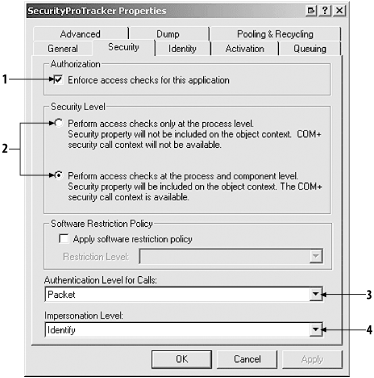
The Enforce component level access checks (indicated by the number 1
in Figure 11) enables RBS for the selected
component and is equivalent to the
ComponentAccessControl attribute that we applied
to the SecurityProTracker class. If this checkbox
is not checked, then RBS will not be applied to this component,
irrespective of the application-wide setting.