Before getting to the
details of securing your PC, it helps to take a step back and look at
the security and privacy tools that Windows 7 makes available.
These
tools include your user account password, Windows 7's User Account
Control and Parental Controls features, the Windows Firewall, the
Windows Defender programs, and the anti-phishing and anti-spam features
of Internet Explorer and Windows Live Mail.
User Account Password
Windows 7 security
begins with assigning a password to each user account on the computer.
This prevents unauthorized users from accessing the system, and it
enables you to lock your computer. See "Protect an Account with a
Password" and "Lock Your Computer," later in this chapter.
User Account Control
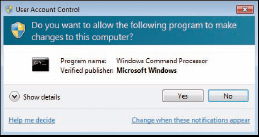
User Account Control asks you to
confirm certain actions that could conceivably harm your system. If you
have an administrator account, you click Yes to continue; if you have a standard account, you must enter an administrator's user name and password to continue.
Parental Controls
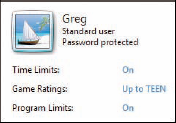
If one or more children use
your computer, you can use Windows 7's Parental Controls to protect
those children from inadvertently running certain programs, playing
unsuitable games, and using the computer at inappropriate times. See
"Set Up Parental Controls," later in this chapter.
Windows Firewall
Because when your computer is
connected to the Internet, it is possible for another person on the
Internet to access your computer and infect it with a virus or cause
other damage, Windows 7 comes with its Windows Firewall feature turned
on. This prevents intruders from accessing your computer while you are
online.

Windows Defender
Spyware
is a software program that installs on your computer without your
knowledge or consent. This program surreptitiously gathers data from
your computer, steals your passwords, displays advertisements, and
hijacks your Web browser. To prevent spyware from installing on your
computer, Windows 7 includes the Windows Defender program.
Phishing
Phishing
refers to e-mail messages or Web sites that appear to come from
legitimate businesses and organizations, but actually come from a scam
artist. The purpose of the message or site is to fool you into divulging
personal or private data, such as passwords and credit card numbers.
Internet Explorer and Windows Live Mail come with anti-phishing features
to help prevent this.
Junk E-mail
Junk e-mail — or spam
— refers to unsolicited, commercial e-mail messages that advertise
anything from baldness cures to cheap printer cartridges. Many spams
advertise deals that are simply fraudulent, and others feature such
unsavory practices as linking to adult-oriented sites, and sites that
install spyware. Windows Live Mail comes with a junk e-mail filter; see
"Set the Junk E-mail Protection Level," later in this chapter.