Data
theft, expensive long-distance calls, and even spying: Virus writers are going
mobile and targeting smartphones. How safe you are depends not just on your
phone, but also on you.

Mobile malware writers celebrated
their first huge success in March this year: security experts found more than
50 unsafe apps in the Android market, which had infected about 200,000 devices
within a few days. The compromised apps – system tools, games and porn
applications – sent personal data like the devices’ unique identification
number (IMEI/IMSI) to servers in Russia and China.
Attackers have already accessed a lot
more than just telephone numbers. The malware known as AndroidOS/Fakeplayer.A,
automatically sends out premium rate SMS messages, running up your bill and
earning the attackers a commission. Other examples, like the Trojan
Android/Adrd.A and the iPhone worm iKee.B, secretly connect your system to
so-called command and control servers, turning it into one of the zombies in a
huge botnet.
Your device then starts sending spam
without your knowledge, is involved in DDoS attacks on websites, and installs
other malware at the attacker’s whim. Secondary attacks can be in the form of
keyloggers which capture every input. ZeuS even spies on PIN codes during
mobile online banking.
For users in countries with lower
smartphone penetration, these malware have luckily not caused much damage – so
far.
However this should not give anyone a
false sense of security: many of the mobile malware examples were not really
dangerous – they have been serving as trial runs for the creation of a much
more dangerous criminal infrastructure that is still being set up.
Android is the current preferred
target for hackers. With a market share of more than 30 percent, it has
definitely left all its competitors behind. BlackBerry, with their low market
share, are quite unattractive for hackers. Symbian is hardly used any longer in
modern smartphones and is losing favor too. On the other hand, Apple’s iOS is
becoming more risky thanks to the discovery of several security loopholes, most
notably a series of vulnerabilities in the PDF reader of the Safari browser,
using which attackers can access your device in no time. To exploit this,
attackers need to divert you to a specially doctored web page. Such pages can
be used to jailbreak your device, but they can also load malware unnoticed.
Then again, Apple quickly rectifies most such problems that crop up: the
described loophole was closed with the release of iOS 4.3.4.
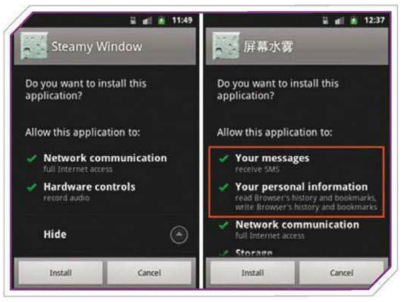
Sneaky
tactics: Android Trojans try to pass themselves
off as normal apps, but they tend to ask for noticeably more access rights.
Don’t just blindly approve anything that you download!
It is generally harder for malware
writers to penetrate iOS or Android because Google and Apple have efficient
methods of protection. These include digital certificates, limited
authorizations, and isolation of apps from the kernel as well as from other
apps. Malware has only limited access to critical parts of the operating
system. The approaches of both the companies are quite similar, though their
ways of implementation are rather different. The closed ecosystem of the iOS is
often criticized, but this makes it difficult to hack. The digital certificates
that Apple signs apps with are very important for this to work. They ensure the
authenticity and legitimacy of apps, which are supposed to be obtained only
from the official App Store. Registration for the iOS Developer Program costs
about 100 US dollars, and is mandatory for releasing an app. Because Apple
checks all submitted applications for malicious code before releasing them, the
chance of a rogue app hitting mainstream users is miniscule. Considering the
number of new applications constantly being released, it is not really clear
how comprehensively Apple analyses all of them. Nevertheless, should a
malicious app still pass the test, Apple is able to delete it remotely,
effectively wiping it from all infected devices.
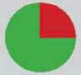
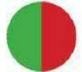
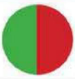
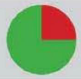
That’s how (un)safe mobile systems are:
|
Protection function
|

Apple iOS
|

Google Android
|
|
Verification of app
How
safe are the apps and software sources?
|
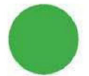
|
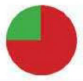
|
| | | |
|
Isolation of apps
How
easily can malware infiltrate the system?
|
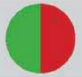
|
|
|
Access rights of apps
How
effective is the protection against data theft?
|
|
|
|
File encryption
How
well are the storage areas protected?
|
|
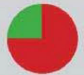
|
Verdict: iOS is safer because of the
clean App Store, Android isolates running apps well, but is also more open and
therefore vulnerable than the iOS.