1. Problem
If you are trying to make the compelling argument that your
session IDs are weak, WebScarab makes a very nice presentation. While
Burp has a stronger statistical method of determining session-identifier
randomness, WebScarab makes patterns in session identifiers visually
apparent.
2. Solution
Open WebScarab and configure Firefox to use it as a proxy,. Browse in your
application to pages that you think use session identifiers. Login pages
or pages that are restricted by authorization are good places to start.
It usually doesn’t matter which specific function you do, as long as
WebScarab can get unique session IDs each time it requests a page at
that URL. Generally speaking, session IDs are usually generated the same
way throughout an application, so finding a problem in one place is
applicable everywhere.
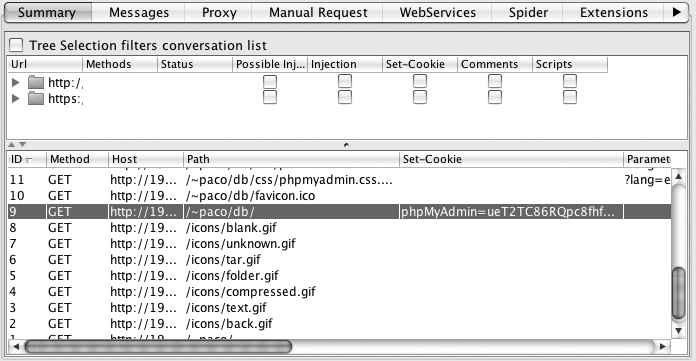
Select the Summary pane in WebScarab and look in the Set-Cookie
column. Figure 1 shows this summary pane.
Request ID 9 is highlighted because it is one of many that have cookies.
We will use this request as our request to analyze.
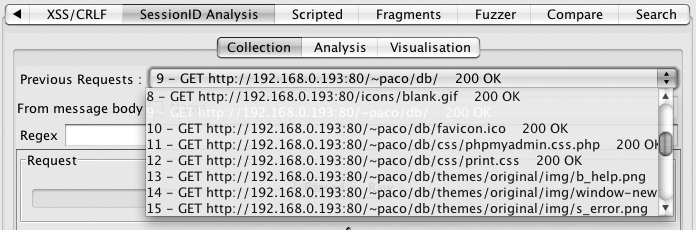
Select WebScarab’s “SessionID Analysis” pane and look at the
“Collection” tab within that pane. Click the drop down next to “Previous
Requests” and select the request that will set the session ID. Figure 2 shows the list, with request 9
selected. Once you’ve selected an appropriate request, press the Test
button. This will bring up a message indicating all the session IDs
WebScarab was able to find automatically within that request. Figure 3 shows the result of such a test. Two
cookies are visible in this Set-Cookie header: phpMyAdmin and pma_fontsize. The fact that the contents of
phpMyAdmin are opaque strings like
z316wV-lrq0w%2C-8lPF6-uvObKdf and the
fact that the other parameter’s name suggests that it controls font size
leads us to focus on phpMyAdmin.

Once you’ve found an appropriate session ID to model, enter a
sample size. We recommend at least 500 or more for a smooth graph. It’s
better to do 1,000 or 2,000 if you can. Then click the Fetch button to
initiate the requests. Each will receive a different session
identifier.
To see the graph, you must first go to the Analysis tab and select
the session identifier you’d like to visualize. Figure 4 shows the Analysis tab, with our
phpMyAdmin cookie selected. Select
that from the drop down options. There may be only one session
identifier available; that’s fine. With your session identifier set,
click on the Visualization tab. If WebScarab is still fetching session
identifiers, you’ll see them show up in real time on this graph—a
powerful demonstration in itself. Furthermore, there should be no
obvious pattern in the visualization graph. If there is, it’s likely the
session identifiers are easily predictable.

3. Discussion
WebScarab’s analysis of session identifiers, while statistically
weaker than Burp’s, provides a much more convincing diagram. Some
patterns are readily apparent in the graph of session identifiers over
time. Figure 5 shows a real web server that has
relatively predictable identifiers. They’re not as bad as
sequentially issued integers, but with some effort a hacker could
develop a program to predict them. This sort of graph can provide the
extra step you need to demonstrate predictability. A clearly visible
pattern makes a stronger impression than statistical confidence
intervals.
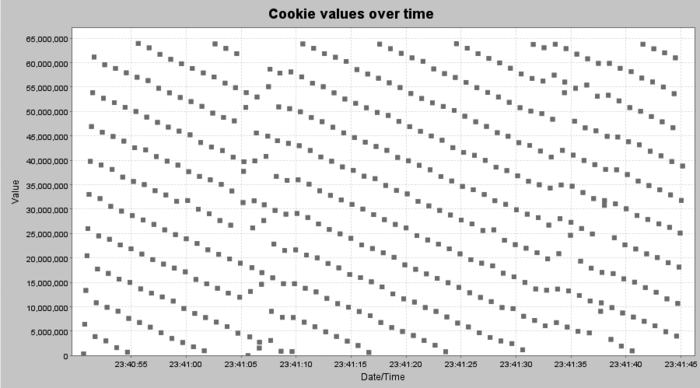
Consider the ten session IDs shown in Example 1. Visually inspecting them, you might
think they were pretty random. Aside from the LL6H at the beginning of each, they are very
long and they appear to have lots of randomness. They are from the same
site that produced the graph in Figure 5, however,
which shows how a little visualization can go a long way towards making
the pattern clear.
Example 1. Session IDs from WebScarab
LL6HZFzp1hpqSHWmC7Y81GLgtwBpx48QdhLT8syQ2fhmysyLcsGD
LL6H77rzbWlFLwwtnWhJgSxpZvkJvLWRy1lykQGvZh33VGJyvf9N
LL6H99QLLvB8STxLLbG9K7GQy1tncyYr6JSGYpCH4n29TTg1vcMZ
LL6HynM9MDj0WQGmTDhKPsvJnbGZhL2SSqBH78bYF2WxSs1kJ3nx
LL6HgMSCpHQH8LJjhbyfg47W5DN2y55SKSbSQM2GcTntSLmL1PHJ
LL6H1m8nLPpzyJylv0m21Znd8v7F1DNT2tDN2FZd0bXHVjVnhcB9
LL6LTMsy8lxfVyn86cZBp6qS3TLMDhfXB83x0Lx8cPCG6f0bzwGw
LL6H4n3G8QBQYWpvdzM8vsBzfyzdQPM6J4HMflZscvB4KDjlQGGT
LL6L4qPHk0PJ92svGQQtvGpd6BG12hqhmRnchLpTy31B08kMkflM
LL6L2TGwrW8XTp206r2CpQXS7LDh5KjkSs7yfW1wbv2GwD20TByG
|
Clear lines or shapes within the graph indicate poor
randomization. When testing an application, it’s easy to get
pseudorandom results and not see an obvious pattern. Laying out the
results in such a graph reveals some (but not all) patterns immediately.
Truly comprehensive analysis requires statistical analysis, such as the
methods used by Burp.
Note that WebScarab will find all sorts of identifiers inside
cookies, not just session identifiers. It may also find non-random
identifiers that record visitor details. Not every cookie value needs to
be random. Don’t be alarmed if one of the identifiers you select for
visualization is a flat, completely predictable line. It may just be a
non-unique token, rather than a session identifier.
That said, some applications will implement multiple session
identifiers to track different behaviors. If you do find an alternate
pseudosession identifier, such as “visitor number,” go ahead and examine
the predictability. It may be that by tampering with some other
identifier, one is able to trick the application into doing something
non-session related, but still just as problematic.
Figure 6 shows an example of a session
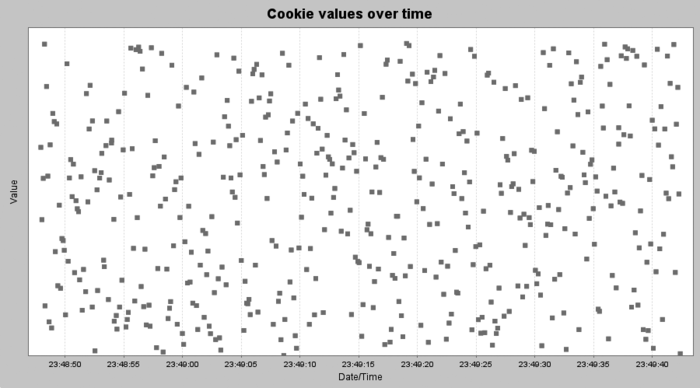
identifier that does not appear, visually, to be predictable. Remember
that your application can fail this test, but
cannot pass it. That is, just because your session IDs are not obviously
predictable from visual inspection doesn’t mean they’re random.