1. Problem
If the session identifier can be predicted, an attacker can steal
the next user’s session and thus impersonate the user. Random,
unpredictable session identifiers are crucial to the security of a web
application. Analyzing randomness can be a difficult statistical
procedure. Fortunately there is a handy tool, the Burp suite, that can
aid in this test.
2. Solution
Fire up the Burp suite and configure the proxy for use with
Firefox . Turn the
automatic intercept option off. Then, navigate to your web application.
Once Burp has recorded a request and response from your web application
in the proxy history, right-click on the request and select “send to
sequencer,” as shown in Figure 1.
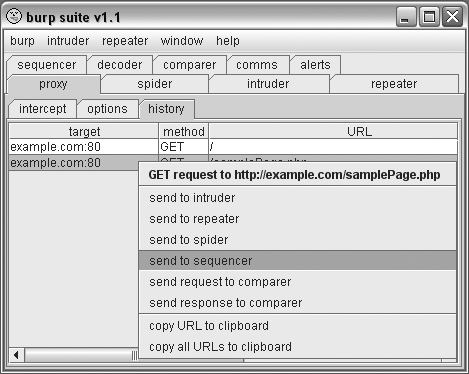
The Sequencer tab will light up red; go ahead and click on it.
Sometimes the Burp sequencer can identify the session identifier (it
refers to it as the “token”) on its own; if not, you’ll have to
highlight the session identifier yourself within the server response.
Burp will pick it up from there.
If you’re unable to find a session identifier, it’s likely because
the server didn’t set one via that response. Navigate to wherever in
your site session cookies are first set. If you don’t know where that
is, open the Edit Cookies extension, set the filter to your site, and
delete all known cookies. Then, after browsing to each new page, refresh
Edit Cookies to display cookies for your site again—if one shows up, you
know it was set on this particular page response.
Once you have a session identifier located within Burp sequencer,
press the Start Capture button on the lower right. This will send
repeated requests to your application, retrieving a new session
identifier each time. Capture a statistically viable number of session
identifiers (we recommend 10,000—but 100 will work for a
demonstration).
Once a sizable enough sample has been collected, pause the
collection and select the Analyze Now button.
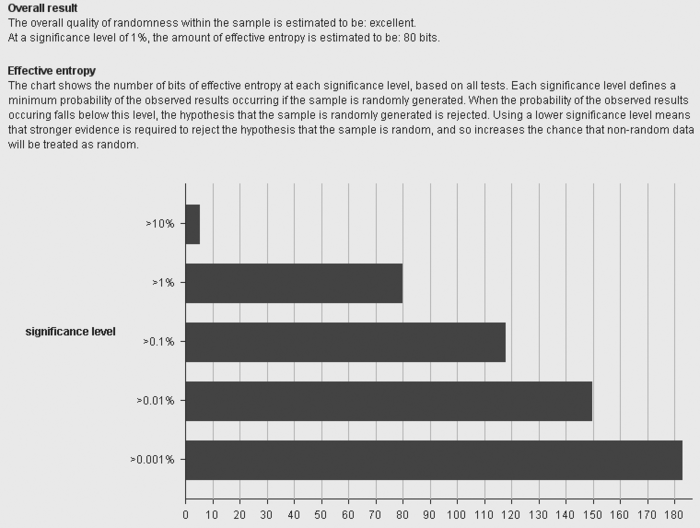
The results will contain a great deal of statistics, but the
general summary is contained within the first page, shown in Figure 2. In fact, the first line will tell
you mostly what you need to know. It will read that “The overall quality
of randomness within the sample is estimated to be:” very
good, good, reasonable, poor, or very poor. The rest of the statistics
are there if you need them.
3. Discussion
The Burp sequencer can’t provide 100% assurance that your session
IDs are truly random. That would take an advanced degree relating to
statistics and information theory, towards the beginning of which you’d
learn that 100% assurance is impossible. Meanwhile, if you don’t have
time for an advanced degree, the Burp sequencer provides extremely
comprehensive analysis. It shouldn’t be trusted absolutely, but given
the choice between no statistical analysis and Burp, you should at least
try Burp.
Ensuring session-identifier randomness can be difficult. The
randomness will usually be determined by the framework. Fortunately,
this test can be performed as soon as a session is set, even if not a
single page of the application is working. If the developers build a
“Hello World” page that sets a session ID, you can run this test—long
before any problems relating to sessions start to become important.
Because it can be done so early, this recipe makes an excellent test to
evaluate a framework.