Files
secured on Windows Server 2008 R2 are only as secure as the permissions
that are set on them. Subsequently, it is good to know that Windows
Server 2008 R2 does not grant the Everyone group full control over
share-level and NTFS-level permissions. In addition, critical operating
system files and directories are secured to disallow their unauthorized
use.
Despite the overall
improvements made, a complete understanding of file-level security is
recommended to ensure that the file-level security of a server is not
neglected.
Understanding NT File System (NTFS) Security
The
latest revision of the NT File System (NTFS) is used in Windows Server
2008 R2 to provide for file-level security in the operating system. Each
object that is referenced in NTFS, which includes files and folders, is
marked by an access control entry (ACE) that physically limits who can
and cannot access a resource. NTFS permissions utilize this concept to
strictly control read, write, and other types of access on files.
File servers should make
judicious use of NTFS-level permissions, and all directories should have
the file-level permissions audited to determine if there are any holes
in the NTFS permission set. Changing NTFS permissions in Windows Server
2008 R2 is a straightforward process; simply follow these steps:
1. | Right-click the folder or file onto which the security will be applied, and choose Properties.
|
2. | Select the Security tab.
|
3. | Click the Advanced button.
|
4. | Click the Change Permissions button.
|
5. | Uncheck the Include Inheritable Permissions from This Object’s Parent check box.
|
6. | Click Remove when prompted about the application of parent permissions.
|
7. | While
you’re in the Advanced dialog box, use the Add button to give access to
the groups and/or users who need access to the files or folders.
|
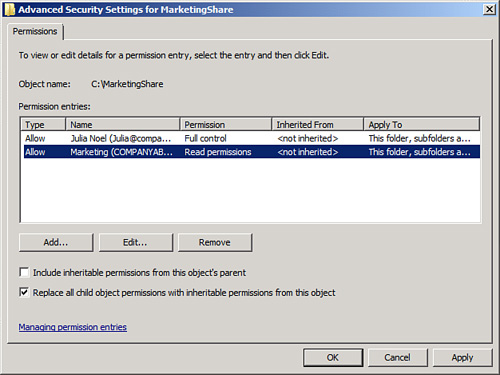
8. | Check the Replace All Child Object Permissions with Inheritable Permissions from This Object check box, as shown in Figure 1, and click OK.
|
9. | When prompted about replacing security on child objects, click Yes to replace child object security and continue.
|
10. | Click OK and then click OK again to close the property pages.
|
Examining Share-Level Security Versus NTFS Security
Previous Windows security
used share-level permissions, which were independently set. A share is a
file server entry point, such as \\sfofs01\marketing, that enables
users to have access to a specific directory on a file server. Older
file systems such as FAT, HPFS, and FAT32 did not include file-level
security, so the security was set instead on the share level. Although
share-level security can still be set on files, it is preferable to use
NTFS-level security, where possible. Share-level security is not very
secure because it cannot secure the contents of subdirectories easily.
Auditing File Access
A good practice for
file-level security is to set up auditing on a particular server,
directory, or file. Auditing on NTFS volumes enables administrators to
be notified of who is accessing, or attempting to access, a particular
directory. For example, it might be wise to audit access to a critical
network share, such as a finance folder, to determine whether anyone is
attempting to access restricted information.
Note
Audit entries are
another example of security settings that can be automatically set via
security templates in Windows Server 2008 R2. It is wise to consider the
use of security templates to more effectively control audit settings.
The following steps illustrate how to set up simple auditing on a folder in Windows Server 2008 R2:
1. | Right-click the folder or file onto which the auditing will be applied, and choose Properties.
|
2. | Select the Security tab.
|
3. | Click the Advanced button.
|
4. | Select the Auditing tab.
|
5. | Click the Edit button.
|
6. | Using the Add button, enter all users and groups that will be audited. If you’re auditing all users, enter the Everyone group.
|
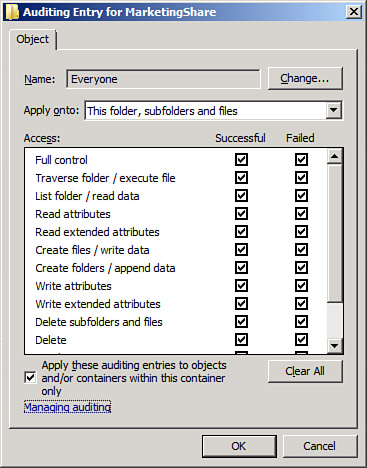
7. | On
the Auditing property page, select all types of access that will be
audited. If you’re auditing for all success and failure attempts, select
all the options, as indicated in Figure 2.
|
8. | Click OK to apply the settings.
|
9. | Click OK twice to save the settings.
|
Note
An
effective way of catching “snoops” in the act is to create
serious-looking shares on the network, such as Financial Statements,
Root Info, or similar such shares, and audit access to those folders.
This mechanism, known as a honeypot, has been successfully used to
identify internal (or external) saboteurs before they could do some
serious damage.
Encrypting Files with the Encrypting File System
Windows Server 2008 R2
continues support for the Encrypting File System (EFS), a method of
scrambling the contents of files to make them unintelligible to
unauthorized users. EFS has proven to be valuable for organizations that
desire to keep proprietary data, especially those stored on laptops,
out of the wrong hands. A more comprehensive approach to client
encryption is with Windows 7/Vista BitLocker Drive Encryption, which
encrypts all files on the entire hard drive, with the exception of a few
files required for startup.