Windows SmartScreen
Microsoft added an interesting and
useful security feature to Internet Explorer 9 called SmartScreen that
helps guard your PC against malicious software downloads. IE 9’s
SmartScreen feature works very well, but of course it can’t help you if
you use a different browser, such as Google Chrome or Mozilla Firefox,
or if you download a malicious file through another means, such as an
e-mail application or USB storage device.
SmartScreen uses a Microsoft hosted
“reputation” service that uses actual user feedback to help determine
whether files are trustworthy. So that means you can help make the
service more useful for everyone simply by using this feature.
To help protect you against malicious software
more globally, Windows 8 includes a special version of SmartScreen,
called Windows SmartScreen, which protects the filesystem against
malicious files, no matter where they come from. Windows SmartScreen
works exactly like IE 9’s SmartScreen feature, meaning it utilizes both
holistic sensing technologies and an Internet-hosted service to determine whether files are malicious or at least suspected of being so.
Configuring Windows SmartScreen
To configure Windows SmartScreen,
you’ll need to launch Action Center, which is available via the system
tray (it’s the icon that resembles a cute little white flag) or through
Start Search.
Using the Action Center route, you’ll see an
option on the left of the window called Change Windows Start Screen
settings. Click this option to display the window shown in Figure 3.
We recommend using the default setting, which is
“Get administrator approval before running an unrecognized app from the
Internet.” Unless you’re regularly hanging out in torrent sites or
other gray areas of the Interwebs, you’ll find this isn’t too annoying.
Using Windows SmartScreen
When Windows SmartScreen fires up, you’ll know it: The full-screen notification shown in Figure 4 displays, interrupting whatever you were doing.
As with any full-screen notification, you’ll want
to deal with this before proceeding. And while SmartScreen can
certainly suffer from false positives, our advice is to think very
carefully before just dismissing this. It’s warning you for a reason.
Action Center Improvements
If you’re familiar with Action Center
from Windows 7, you know that it’s an improved version of the Security
Center that dates all the way back to Windows XP with Service Pack 2.
In Windows 8, Action Center carries forward largely unchanged in that
it still performs the same function of tracking security and
troubleshooting items in the OS and popping up notifications when
something goes wrong.
What’s changed is that Action Center now tracks
far more items than it did in Windows 7. And while many of the items it
tracks are, as you might expect, related to new features in Windows 8,
some aren’t. It’s just fleshed out better.
In Windows 8, Action Center now tracks these additional items:
- Windows SmartScreen: This
security feature, described earlier, debuted in Windows 8 and provides
anti-malware protection directly through the Windows filesystem.
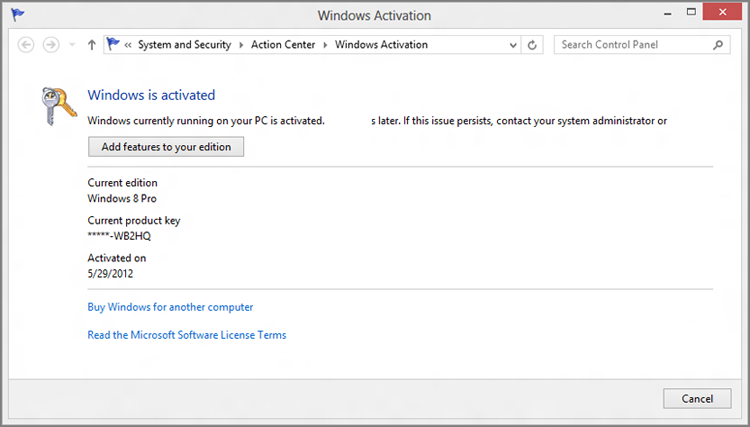
- Windows activation: While
activation is hardly new to Windows 8, Microsoft has created an Action
Center experience in this release that tracks whether your copy of
Windows is activated, and thus valid. You can see this interface in Figure 5.
Figure 5: Windows is activated
- Microsoft account: The
ability to sign in to Windows 8 with a Microsoft account is obviously
new to this version of the OS, but the underlying technology that
Action Center is actually tracking here is whether your account is
working properly and syncing settings from the PC to SkyDrive (and thus
to other PCs) and vice versa.
- Automatic maintenance: Like
previous Windows versions, Windows 8 will automatically run a scheduled
maintenance routine at a set time, 3:00 a.m. What’s changed in Windows
8 is that this activity is now tracked by Action Center to ensure that
it completes successfully. But you can use the Start maintenance link
to run a manual check or Change maintenance settings to configure a new
time.
- HomeGroup: Action
Center now checks to see whether you’re part of a homegroup. This is
important because signing in with a Microsoft account breaks the normal
workgroup-style home network sharing we used to use.
- File History: The
new File History feature works with the Push Button Reset functionality
in Windows 8 to create a more flexible way of restoring lost data than
the old method, a combination of Previous Files (which no one even knew
existed) and Windows Backup (which was ponderous and slow).
- Drive status: Action Center now checks to see whether all of the fixed disks attached to your computer are working properly.
When Action Center detects an issue, it provides
notifications via its system tray icon. Clicking these, or the
associated warnings that appear in the Action Center control panel,
brings you to the user interface you need to mitigate the issue. For
example, as part of its overall system performance and reliability
tracking, Action Center could eventually warn you to disable
app[lication]s to help improve performance. This slightly off-base
recommendation—it really means, “disable startup applications to
improve boot-time performance” and has nothing to do with Metro-style
apps—links to the Task Manager. In Windows 8, the Task Manager now
provides a Startup tab that lets you enable and disable applications
(but not Metro-style apps) that are configured to run at boot time.
This can be seen in Figure 6.
But Wait, There’s More
In addition to the features discussed
previously, Microsoft has improved a number of security features that
debuted in previous Windows versions, too. Most of the features don’t
require any user interaction. They simply work in the background,
ensuring that Windows 8 is as secure as it can be.
A small sampling includes the following:
- Credential Manager: Windows
has long included a Credential Manager interface—previously called
Windows Vault—that helps you combine the usernames and passwords for
the local network and for websites with your Windows user account. New
to this release is that you can now tie these other sign-ins with your
Microsoft account for the first time, since most people will be signing
in to Windows 8 with that account type.
- Windows kernel: The
innermost part of Windows has been shored up with protection
technologies that were curiously available only to other Windows
components in previous OS versions.
- ASLR: Since
Windows Vista, Windows has employed a technique called address space
layout randomization (ASLR) to randomly load code and data into
different memory addresses at run time, cutting down on an entire class
of memory-based attacks. In Windows 8, ASLR has been improved with even
more randomness. And it’s been extended to even more Windows components.
- Memory: Modern Windows
versions have of course always included various forms of protection
against memory-based attacks, and the move to isolated Metro-style apps
will help in this and other regards. But Windows 8 also includes new
protections against “use after free” vulnerabilities, where rogue or
malicious applications are able to examine and exploit freed up memory
that still includes valuable data or other code.
There’s still more, but you get the idea. While
many Windows 8 security features are in your face when required, some
simply work behind the scenes, tirelessly keeping you safe without you
doing a thing. What’s missing is the “security theater” that used to
dog older Windows versions, where the security features were
purposefully made to be overly chatty and interruptive, providing you
with a sense that something good was happening.