1. Default Security of the GPMC
The
default security configuration for administering Group Policy in
Windows Server 2008 is similar to that in Microsoft Windows Server
2003. Of course, the changes from Microsoft Windows 2000 Server to
Windows Server 2003 were substantial, because the GPMC was introduced
with Windows Server 2003. The GPMC introduced a totally new set of
delegations and methods of delegating administration over Group Policy
management.
The GPMC is installed on a
Windows Server 2008 domain controller by default with some default
security delegation that existed in Windows Server 2003.
The default security for administration of Group Policy is divided into six categories:
Create GPOs
Link GPOs
Edit, delete, and modify security of GPOs
Edit GPOs (only)
Model GPOs
Perform Resultant Set of Policy (RSoP) of GPOs
For each of these delegations, Setup configures the default settings when it installs Active Directory directory service. Table 1 lists the default permissions for each of the delegations in the GPMC.
Table 1. Default Delegations in the GPMC
| Delegation | Permission | User or Group |
|---|
| Create GPOs | Create GPO in the domain | Domain Admins
Group Policy Creator Owners
SYSTEM |
| Link GPOs | Link GPO to specified node in Active Directory only | Administrators
Domain Admins
Enterprise Admins
SYSTEM |
| Edit settings, delete, modify security of GPOs | Edit GPO using GPME
Enable/Disable GPO and parts of GPO
Import Settings
Backup GPO
Restore from Backup
Link WMI Filters
Delete GPO
Modify Security Filtering
Modify Delegation on GPO | Domain Admins
Enterprise Admins
SYSTEM |
| Edit GPOs (only) | Edit GPO in GPME
Enable/Disable GPO and parts of GPO
Import Settings
Link WMI Filters | |
| Perform Group Policy Modeling analyses | Model GPOs for the specified Active Directory node | Administrators
Domain Admins
Enterprise Admins
SYSTEM |
| Read Group Policy Results data | Determine RSoP for the specified Active Directory node | Administrators
Domain Admins
Enterprise Admins
SYSTEM |
| Read (from Security Filtering) | View Settings
Backup GPO to existing folder | Authenticated Users |
As
you can see, unless you are in the Group Policy Creator Owners group or
have membership in the Domain Admins group, you do not have permission
to manage Group Policy by default.
2. Default Security of AGPM
AGPM
adds an additional, yet integrated, level of delegation to your Group
Policy management. Remember, AGPM is not a mandatory tool—it just makes
the administration of GPOs much easier and adds functionality that the
GPMC does not provide.
When you install
AGPM, no GPOs are automatically added to the AGPM server for
management. This could cause some undesired results, so the inclusion
(or controlling) of GPOs in AGPM is left up to the AGPM administrator.
Some
distinct delegations are set up during the installation of AGPM that
are carried out through the initial use of AGPM and control of GPOs.
Only two user accounts are even given control within AGPM as a default.
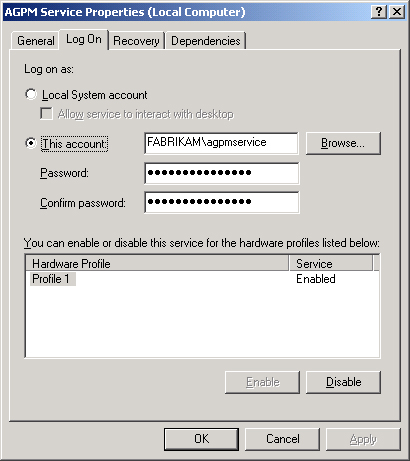
The
first user account, agpmservice, is not used for logging in and
managing AGPM; rather, it is a service account that the AGPM service
uses when it accesses the GPOs on the production domain controller.
This account is in essence the “proxy” account that does all of the
work when production GPOs are in any way touched by AGPM. This account
has privileges over creating new GPOs and the GPOs that it creates
through its inclusion in the Group Policy Creator Owners group and its
explicit permissions to the GPOs in SYSVOL of the domain controllers.
As you can see, a real administrator does not use this user account; it
is just the service account used by AGPM, as shown in Figure 1.
The
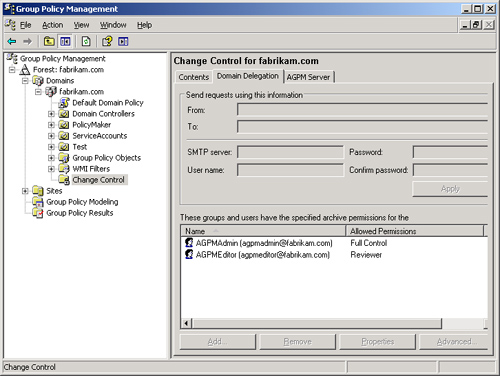
second user account used during installation will be used by a real
administrator. This user account becomes the AGPM administrator and has
full control over the AGPM environment, as shown in Figure 2.
The AGPM administrator account can be an existing user account that
will have full administrative privileges over all of AGPM, or it can be
a dedicated AGPM administrator account used only for the initial setup
of delegation in AGPM.
Best Practices
It
is a best practice to use a dedicated user account when defining the
AGPM administrator account during installation of AGPM. This simplifies
administration and provides a more flexible delegation model for future
configurations. If an existing user account, associated with an
employee, is used, this account might not always be in control of GPOs,
requiring the account to be changed when the user is no longer in
charge of GPOs. |
After
you install AGPM, the AGPM administrator will log in and create the
other delegations. At this time, you should configure another user
account to have full control over the AGPM; multiple user accounts
should have access to AGPM with this level of privilege so that
administrators do not use the original AGPM administrator account on a
regular basis.