The last article covered Tripwire,
which ensures the integrity of the file system. This article extends the
security from the operating system and application files a level further. Disk
encryption is predominantly used in critical open source infrastructures, for
which TrueCrypt is widely used.
In the past, the security of data residing
on the disks was seldom a priority. This led to the situation in which data was
only securely stored and accessed as long as the disk was in the system. Having
physical access to remove the hard disk, however, could let the attacker gain
complete access to the data by simply plugging in the drive as a secondary
volume in another system. This problem was more serious for desktops, where
systems could be easily moved between locations, thus resulting in possible
data leakages. This called for a means of encrypting the data in such a way
that even if the disks are moved to a different machine, the contents of the
volume are protected, and accessible only to authenticated owners. This
required a strong encryption system on the disk itself, with the necessary
authentication services.
How TrueCrypt works
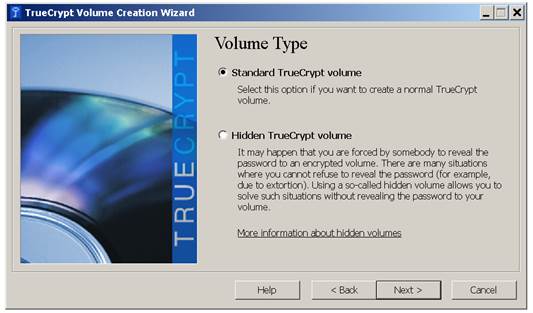
A
sample installation screen on Windows
TrueCrypt is a great open source tool for
this purpose. It supports Windows and Mac platforms, and also supports almost
all Linux distros. Typically, on Ubuntu and CentOS systems running in a
business-critical data center, TrueCrypt is widely used to encrypt disk
volumes, to keep data safe from physical theft by prying attackers. It works on
the principle of ‘on the fly’ encryption, whereby the encryption and decryption
operations are performed once the authentication key is provided, and the
process takes place transparently to the user. To achieve this, the utility
installs kernel-level drivers (Linux) or device drivers (Windows) by hooking up
with the disk management modules of the OS, thus acting as an agent between
disk read/writes and the application layer. TrueCrypt can also create a single
encrypted hidden volume inside an existing file-system volume, for elevated
security. Since it can handle an entire mounted volume, it can be easily used
to encrypt data on a USB pen drive too. As for the crypto processing, the
utility does it so fast and seamlessly, that the user doesn't even know about
it. Usually, such on-the-fly utilities demand heavy memory and CPU usage, but
that’s not the case with TrueCrypt. It achieves this by making use of all CPUs
and cores available on the system. It also uses a technique called pipelining,
whereby a portion of the disk is read and decrypted in memory, acting as a
buffer, in anticipation that the application would want to fetch that data
piece.
TrueCrypt
is widely used to encrypt disk volumes, to keep data safe from physical theft
by prying attackers
TrueCrypt requires a user-entered password
to encrypt the volume, and also allows the selection of an algorithm for
encryption.
Besides the keys, on Windows machines
TrueCrypt allows the user to generate a random key by moving the mouse
randomly. This key is fed to the encryption algorithm to further enhance its
strength, thus introducing tighter data encryption security. It is important to
note that there is no bypass or backdoor for the utility if the pass-phrase is
forgotten. Due to the complex algorithms in use, it can practically take
millions of years to crack an encrypted volume in such situations. TrueCrypt
can also accept PKCS #11 protocol-based devices such as smart cards or
secure-tokens. This makes it a must-have utility for volumes carrying seriously
critical corporate data.
Installation
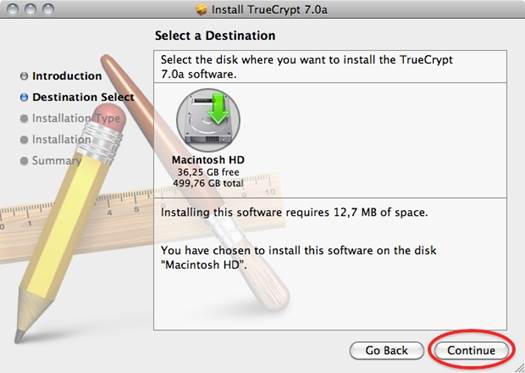
A
screenshot of TrueCrypt being installed
This utility can be downloaded from sourceforge.net/projects/truecrypt/,
or the latest available version from http://www.truecrypt.org.
While installing on GUI-based Ubuntu or a similar distro, just unpack and
double-click the binary archive to get it installed under Applications>Accessories>TrueCrypt.
Figure 1 shows a screen shot of TrueCrypt being installed on an Ubuntu distro.
Upon running the utility, it gives you a choice to either create an encrypted
container, or a protected volume within a partition or disk drive mount. The
next step is to select encryption and hash algorithms, and the pass-phrases.
Figure 2 shows a sample installation screen on Windows. Depending on the
system’s hardware configuration, it may take a while for TrueCrypt to process
the data. This can be significantly long for a high volume of data.
IT administrators are advised to try some
hands-on work and gain expertise on the utility in a lab set-up, prior to
deploying it on their production infrastructure. This is because there is no
mercy or trick to retrieve locked data if the pass-phrase is forgotten. The
drive or mounted volume under TrueCrypt will be totally inaccessible under such
situations. This also calls for tighter security mechanisms to store the key in
a safe location. Since it performs encryption-decryption on the fly, disk
fragmentation occurs quite often; hence, for better system performance,
administrators are also advised to defrag the volumes periodically. TrueCrypt
is installed on business-critical production systems including Web servers,
file servers, email servers, etc, which makes it a standard utility for IT
infrastructures where business data security is paramount.