Don't fall victim. With these tips
and tools; you can protect yourself against malware, phishing, and theft.
MOBILE MALWARE IS getting lots of attention
these days, but you can't forget about your PC's security after all, you
probably still use it to pay bills, shop online, and store sensitive documents.
You should fully protect yourself to lessen the chance of cybercriminals
infiltrating your computer and your online accounts, capturing your personal
information, invading your privacy, and stealing your money and identity.
You need to guard against viruses, of
course, but not all antivirus programs catch all threats, and some do better
than others. You have to watch for many other types of threats, too: Malware invasions,
hacking attacks, and cases of identity theft can originate from email, search
engine results, websites, and social networks such as Facebook. They can also
come in the form of links or advertisements for phishing and scam sites. But
with some education on the topic, and the right tools, you can identify such
scams and avoid falling victim.
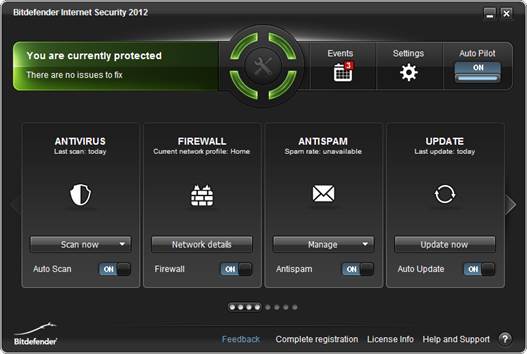
Bitdefender
Internet Security 2012 had the highest rating in our malware detection,
blocking, and removal tests.
If your children use your computer, you
must also protect against inappropriate content such as violent games and adult
sites, and you should monitor communication on social networks. Although the
best approach is to keep a close eye on your kids while they use the computer,
you can employ tools and services to filter content and monitor their Web usage
when you're not around.
Protecting your data from computer thieves
and from people who tap in to your Wi-Fi signal is also important. Encrypting
your computer is the only way to ensure that a thief cannot recover your files,
passwords, and other data. And unless you password protect and encrypt your
wireless network, anyone nearby can connect to it, monitor your Internet usage,
and possibly access your computers and files.
Here are the security threats you should
watch for, and the tools you can use to protect against them.
Viruses and Other Malware
Viruses, spyware, and other types of
malware are still prevalent, and cybercriminals are constantly finding new ways
to infect computers. Although adult sites and illegal file-sharing sites have a
reputation for harboring malware, you don't have to browse the shady parts of
the Web to become infected.
Installing a good antivirus or Internet
security program should be your first step. However, not all are created equal.
While no single antivirus product can protect against all of the millions of
malware variants, some packages detect (and successfully remove) more threats
than others do. For strong PC security, choose one of the top performers from
our 2012 antivirus product-line reviews. such as Bit defender Internet
Security, Norton Internet Security, or G Data Internet Security.
Although an antivirus package is your
primary weapon for fighting malware, you might wish to add other tools to your
arsenal for extra security.
OpenDNS (www.opendns.com) provides content
filtering that blocks many malware-infested sites and phishing scams. You can
enable this online sen/ice on select computers, or on your router to protect
all connected devices. The free OpenDNS FamilyShield automatically blocks
malware, phishing sites, adult content, and proxy sites that try to bypass the
filtering, and it requires only a simple setting change on your PCs or router.
The OpenDNS Home and Premium DNS offerings filter malware and phishing sites,
and let you make a free or paid account to customize the filtering and other
features.
The freeware utility Sandboxie lets you run
your Web browser or any other application in a safe mode of sorts to protect
against damage from downloaded viruses or suspicious programs that turn out to
be malware. It does so by running the browser or selected program in a virtual
environment (also known as a sandbox) that isolates the program from the rest
of your system. Some antivirus or Internet security packages come with a
sandbox feature, but if yours doesn't (or if it doesn't allow you to run
programs in the sandbox manually), consider using Sandboxie when you're
browsing risky sites or downloading suspicious files.
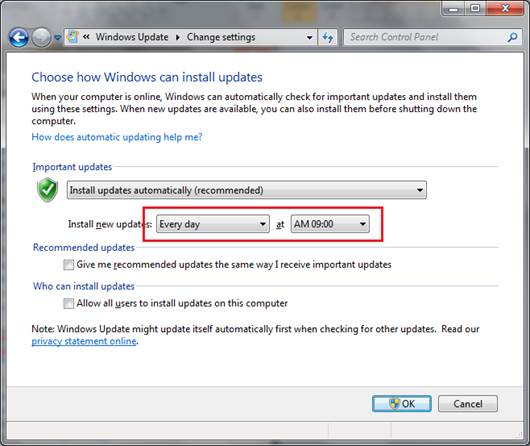
Through
the Control Panel, you can enable automatic updates for Windows and other
Microsoft products.
Intended to complement the defenses you
already have, MaIware bytes works alongside most regular antivirus programs. It
may catch malware that your regular antivirus utility misses, or remove threats
that your standard package can't. The free version does on demand scans (you
manually open the program and run a scan), whereas the paid version has real time
monitoring just as regular antivirus software does.
In addition to installing antimalware
utilities, you can take other steps to help prevent attacks.
Enable automatic Windows Updates: This
action ensures that Windows and other Microsoft products regularly receive the
latest security patches. You can adjust Windows Update settings via the Control
Panel. For best protection, choose to have Windows download and install updates
automatically.
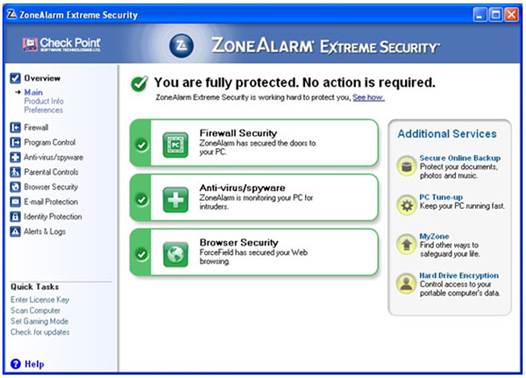
ZoneAlarm
Free Firewall provides protection for both incoming and outgoing traffic.
Keep non-Microsoft software up to date:
Don't forget to update your other software, too. Some popular programs and
components (such as Web browsers, PDF readers, Adobe Flash, Java, and
QuickTime) are bigger targets than others, and you should be especially mindful
to keep them up to date. You can open the programs or their settings to check
for updates, but most will automatically notify you when an update is available
and when you receive such notifications, don’t ignore or disable them.
Hacking and Intrusions
Malware-caused PC problems aren’t the only
thing you have to worry about. A determined cybercriminal can get inside your
PC by directly hacking into it, and some malware can steal your data and
passwords, sending the information back to home base.
This is where a firewall comes in handy: It
serves as a gatekeeper, permitting safe traffic (such as your Web browsing) and
blocking bad traffic (hacking attempts, malware data transfers, and the like).
Windows includes a firewall, named
(appropriately enough) Windows Firewall. It's set by default to block malicious
traffic from coming into your computer, but it isn't set to watch the data
that's going out, so it will likely not detect any malware attempts to transmit
your data to cyberattackers. Although you can enable the firewall's outgoing
protection (in Windows Vista and later versions), that isn't easy for the
average user to set up or configure.
For the ultimate in PC security, you should
use a firewall that protects your machine from both incoming and outgoing
malicious traffic by default. First, find out whether your antivirus utility or
Internet security package has a firewall component, and whether it offers ful I
protection. If it doesn't, consider a third-party firewall such as ZoneAlarm
Firewall or Comodo Firewall Free (personalfirewall.comodo.com).
Phishing and Scam Sites
One method that cybercriminals use to steal
your passwords, money, or identity is commonly called phishing (a play on the
word fishing). Attackers try to get you (the fish) to hand over your
information or money. They do so by hooking you with an email message, IM, or
some other form of communication (the bait) that looks as if it came from a
legitimate source such as a bank or an online shopping site.
Phishing isn’t a new tactic, but people
still fall for it. Here are some precautions that you can take to keep phishing
scams from reeling you in.
Don't click links in email: Scammers often
put links to fake login pages in email messages that look very convincing in an
attempt to steal your personal information. With that in mind, if an email ever
asks you to click a link to log in to a site and enter your username and
password, don’t do it. Instead, type in the real website URL of the company
directly into your browser, or search Google for the site.
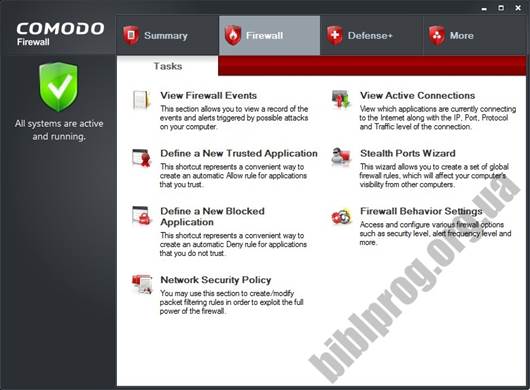
Comodo
Firewall Free offers a full firewall and extra protection against malware.
Check for SSL encryption: Before entering
sensitive information online, make sure that the website is using encryption to
secure the information while it's moving over the Internet. The site address
should begin with https instead of http, and your browser should show some kind
of indicator near the address bar. If a site isn't using encryption for a
screen in which it asks you to enter sensitive data, it's most likely a
phishing site or scam site. SSL encryption isn't a guarantee of safety, but you
ought to make a habit of looking for that lock icon.
Use a Web browser add-on: Many Web browser
add-ons out there can help you identify phishing scams and other dangerous
sites. Typically these plug-ins use badges or some other indicator to show
whether a site is safe, unsafe, or questionable. Most antivirus programs offer
these types of browser add-ons, but if yours doesn’t or you don't like it,
consider using Web of Trust (www.mywot.com), an independent site reputation
tracking service.