How to control usage on company-owned
devices
Historically, where employee-owned devices
are concerned, company efforts to protect data and assets on mobile devices
have focused on controlling the actual devices. That is changing, however.
Today, there is a growing realization among businesses that implementing
comprehensive protection also means enacting some form of control over the apps
employees use on those devices.

How
to control usage on company-owned devices
Why be concerned
Why bother controlling app usage? In a
word: security. Primarily, companies fear that employees will download
malicious apps that introduce any number of exploits that could enable a hacker
to take control of the device. There's also the worry that employees could make
company data vulnerable by using apps that share and sync.
"It's becoming increasingly difficult
to separate corporate technology use from personal technology use, regardless
of who owns the device," says Mike Battista, research analyst with Info Tech
Research Group (www.infotech.com). "This is particularly true when you
bring the cloud into it. If an app be it an actual downloaded app or just a Web
service-stores data in the cloud, it doesn't matter that it's a company-owned
device. The data all goes to where the employee wants it to. That can be a
problem if there is information the business wanted to keep within company
walls."
Companies more apt to be concerned about
app control are those with proprietary/confidential data at risk and those
under scrutiny of regulations. "Honestly, almost all companies have data
they want or need secured, but those companies who are in heavily regulated
industries are the groups who are the most concerned," says Christian
Kane, analyst with Forrester Research (www.forrester.com). "Smaller
companies tend to have a more laissez-faire attitude towards device and app
security to a certain extent, but really it's dependent on the company."
Why companies don’t monitor
Considering what's at stake, why don't all
companies that deploy mobile devices also monitor and control employee app
usage? "First, most companies aren't using a large number of mobile
applications, and a majority of their workforce isn't using company apps that
are available," says Kane. "This means that they don't necessarily
have mobile apps as a high priority, and most firms today aren't monitoring
apps." Most companies, he says, still focus only on mobile device
management, and most MDM solutions don't enable tracking all app usage, only
identifying what apps are installed.
Additionally, monitoring app usage can
prove difficult. "Without actively seeking out an MDM or MAM [mobile
application management] solution, keeping track of app installation and usage
on employee devices (even if the devices are issued by the company) is not easy
to do," Battista says. Despite increasingly more companies using MDM and
MAM solutions, many companies still don't see an immediate advantage to doing
so, he says.

monitoring
app usage can prove difficult
Kathryn Weldon, principal analyst for
enterprise mobility with Current Analysis (www.currentanalvsis.com), says that
depending on the number of apps in use, implementing a MAM solution may not be
worth the effort. "It depends on how many apps you even allow your users
to use," she says. "[If] you have less than five apps that you're
worried about, [then] maybe it's not worth it." But if you have a fairly
large number of apps, she adds, and notice employees are bringing in their own
devices for interacting with both personal and corporate data, "there is
the paranoia that should probably kick in at that point to figure out some way
to lock down the personal and business data."
Measures of control
Though some companies have yet to adopt an
MDM or MAM solution, it is likely companies will seek out solutions with
application control functionality as app reliance among employees grows. IDC
has forecast that global revenue from MEM (mobile enterprise management)
software, which includes both MDM and MAM components, will grow from $444.6
million in 2011 to $1.8 billion by 2016.
Battista sees "application management
as an increasingly emphasized part of MDM." Regardless of terms and
acronyms used, he says, "I'm seeing vendors racing to offer functionality
that goes beyond basic MDM." Many MDM vendors, he says, promote their
corporate app stores and app management as a differentiating feature."
Weldon's recent research breaks down
vendors offering MAM abilities into functional categories, including:
§
Vendors that offer MAM solutions but also
operate an app store
§
Vendors that focus on mobile application
development but also offer MAM or app store integration
§
Vendors that lead with mobile security and use
app wrapping to address MAM
§
MDM vendors that incorporate MAM capabilities
For SMBs, she says, MDM vendors that
incorporate MAM abilities are probably the best fit currently. For companies
already investing in MDM solutions, Weldon adds, "you can probably go to
the next step with them."
Early days
As MAM is still in its early stages, Kane
says, most companies have yet to adopt a solution. As companies build more
mobile apps in their environments, though, there will be a greater need for
both app management and app distribution/delivery solutions such as corporate
app stores. Approaches now available include vendors that use an SDK to allow
developers to leverage their management tools. To date, this approach has
probably been offered most, Kane says, because the solution is often tied to
MDM or other mobile solutions, although it does "require different
versions of each application you want, and if multiple management firms are
offering an SDK, it gets tricky."
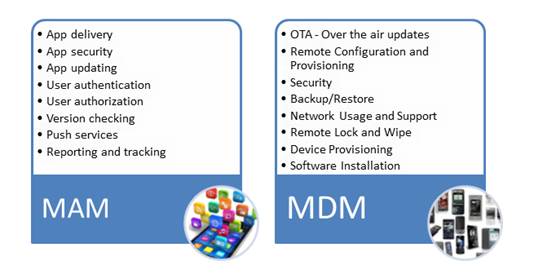
Most
companies will not deploy both MDM and MAM, but will choose the service that is
more in sync with their particular needs.
In addition to application wrapping,
"which is basically putting a policy/security wrapper around a given
application," Kane says, a third vendor type is offering "virtual
workspace containers" that essentially let companies install all corporate
apps in a separate container on the device so that work and personal apps
don't interact. Currently, app wrapping is drawing considerable interest and
will probably get significant traction moving forward "because it lets you
be a bit more agile in terms of the apps you put in there," Kane says.
Ultimately, Battista foresees vendors
offering device, app, and document management functions "under the same
umbrella, either as bundles or allowing businesses to pick and choose a la carte.
I'm not sure which acronym will win out for describing that set of features,
but many vendors will attempt to be a one-stop shop for all of them."