After studying in detail how to create and enforce identity-based rules for regular users who need to pass traffic through
firewalls, you can now turn your attention to potential admin users
attempting to execute commands on IOS devices. As discussed earlier,
TACACS+ is a natural choice for this type of demand because two of its
basic attributes (cmd and cmd-arg) lend themselves well to the challenge of individually authorizing any available command on IOS software.
Although the selection of the authentication
protocol is one essential facet of the problem you need to solve, there
are some important aspects to take into account:
Modern
networks are characterized by an increasing number of infrastructure
devices (routers, switches, firewalls, Wireless Access Points, and so
on) that need to be managed. Scalability is a key topic here.
It
is not typical for companies to have the level of expertise evenly
distributed across branches and headquarters. Logical configuration of
remote devices is frequently performed from the central site. Some sort
of configuration profile that could be built once and deployed multiple times for similar devices would be of great value.
There
are many examples of products that integrate several functional
domains. Cisco Integrated Service Routers (ISR), for instance, can
combine routing, switching, WLAN connectivity, WAN optimization,
telephony, and security features, just to name a few. The challenge
resides is that most of the time, there are distinct technical teams in
charge of each knowledge segment, with different sets of metrics, and
so on. How to ensure service integration while still separating teams?
Traditional solutions that provide only all-or-nothing types of access control do not meet the flexibility requirements of complex environments. Granularity is fundamental.
Cisco Secure ACS implementation of the TACACS+
server portion helps to deal with the issues just raised. By supporting
the creation of Shared Profile Components
that can be applied to any number of user groups, scalability and
manageability result. Two kinds of profiles deserve explicit reference:
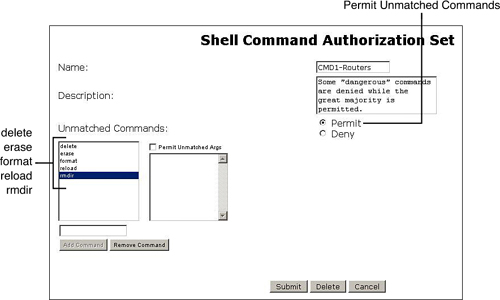
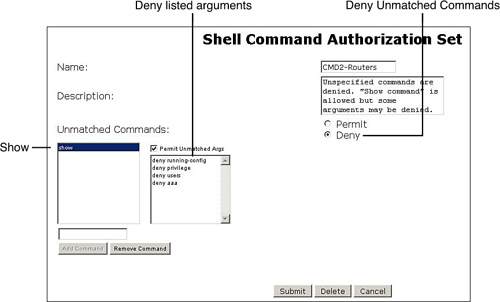
Shell Command Authorization Sets: Flexible collections of commands that can include any command or, even more specifically, any command argument. Figures 1 and 2
show two sample command sets that were constructed using different
logic. Although the first, named CMD1-Routers enables most commands and
denies only specific ones, the second, CMD2-Routers, does the opposite,
denying by default and enabling only what was explicitly permitted. It
is relevant to point out that in the second command set some arguments
of the show command were also denied. This provides an illustration of how powerful this resource is.
Network Device Groups (NDG): Sets of AAA Clients (NASes).
These types of CS-ACS profiles can be combined with command sets inside User groups to form a matrix of access privileges similar to that one illustrated in Table 1.
Notice that members of one User group may now be assigned a different
command set for each NDG. This section examines these concepts by
presenting practical usage scenarios.
Table 1. Combining NDGs and Command Sets Inside User Groups
| | NDG INTERNET | NDG INTRANET |
|---|
| User Group GROUP1 | Command Set CMD1 | Command Set CMD2 |
| User Group GROUP2 | Command Set CMD3 | Command Set CMD1 |
Example 1
reinforces the concept that individual command authorization is not
supported by RADIUS. This is not a bug. It is just the nature of the
protocol.
Example 1. Individual Command Authorization Is Not Supported by RADIUS
! Defining an AAA Server Group that uses the RADIUS protocol
aaa group server radius RADIUS1
server 172.21.21.250 auth-port 1812 acct-port 1813
server-private 172.21.21.250 auth-port 1812 acct-port 1813 key 7 13061E010803557878
!
! Attempting to configure command authorization using RADIUS
OUT(config)#aaa authorization commands 1 CMD1 group RADIUS1
%AAAA-4-SERVNOTACPLUS: The server-group "RADIUS1" is not a tacacs+ server group.
Please define "RADIUS1" as a tacacs+ server group.
|
Example 2
assembles the relevant commands to implement command authorization and
accounting on IOS. Notice that IOS enables the usage of named method
lists instead of just the default
method list. This is useful when there is a need to implement different
methods for the various types of access (Console, VTY, PPP, and so on).
Tip
It is good practice to always use named method lists
even if you might have perceived it as more complex in a first contact
with the resource. This approach guarantees much more flexibility if
you need to add another AAA type of control later. Examples 3 through 6 illustrate the process of calling method lists into action.
Example 2. Basic Configuration for IOS Command Authorization and Accounting
aaa new-model
!
! Defining an AAA server-group called "TACACS1"
aaa group server tacacs+ TACACS1
server 172.21.21.250
server-private 172.21.21.250 key 7 14141B180F0B7B7977
!
! Defining the source interface for TACACS+ packets
ip tacacs source-interface Vlan21
!
! Defining a LOGIN method for the serial console (local authentication for this line)
aaa authentication login CONSOLE local
! Defining a LOGIN method for the VTY lines (Telnet and SSH)
aaa authentication login TERMINAL group TACACS1
!
! Authorization for EXEC sessions and execution of individual commands
aaa authorization exec EXEC1 group TACACS1
aaa authorization config-commands
aaa authorization commands 1 CMD1 group TACACS1
aaa authorization commands 15 CMD15 group TACACS1
!
! Accounting for EXEC sessions and execution individual commands
aaa accounting exec EXECLOG1 start-stop group TACACS1
aaa accounting commands 1 ACCT1 start-stop group TACACS1
aaa accounting commands 15 ACCT15 start-stop group TACACS1
!
! Applying the LOGIN authentication and EXEC accounting methods for the console line
line con 0
login authentication CONSOLE
accounting exec EXECLOG1
!
! Applying the LOGIN, Authorization and Accounting named Method Lists to the VTY lines
line vty 0 4
login authentication TERMINAL
authorization exec EXEC1
authorization commands 1 CMD1
authorization commands 15 CMD15
accounting exec EXECLOG1
accounting commands 1 ACCT1
accounting commands 15 ACCT15
transport input telnet ssh
|
Example 3 depicts the operation of the named method lists defined in Example 2 to control console line access. EXEC Authorization is not defined for the console line.
Example 4
illustrates access control to a VTY line (via telnet, in this case). In
this example, a value of “15” to the privilege-level (priv-lvl=15) is
assigned after EXEC Authorization.
Example 3. Console Session (Local Authentication and TACACS+ Accounting)
! Locally defined user "admin" connects to the console line
AAA/BIND(00000017): Bind i/f
AAA/ACCT/EVENT/(00000017): CALL START
Getting session id for NET(00000017) : db=8466336C
AAA/ACCT(00000000): add node, session 43
AAA/ACCT/NET(00000017): add, count 1
Getting session id for NONE(00000017) : db=8466336C
AAA/AUTHEN/LOGIN (00000017): Pick method list 'CONSOLE'
Username: admin
Password:
DMZ>
! Accounting for the EXEC session
AAA/ACCT/EXEC(00000017): Pick method list 'EXECLOG1'
AAA/ACCT/SETMLIST(00000017): Handle ED000006, mlist 84664930, Name EXECLOG1
Getting session id for EXEC(00000017) : db=8466336C
AAA/ACCT(00000017): add common node to avl failed
AAA/ACCT/EXEC(00000017): add, count 2
AAA/ACCT/EVENT/(00000017): EXEC UP
AAA/ACCT/EXEC(00000017): Queueing record is START
AAA/ACCT(00000017): Accouting method=TACACS1 (TACACS+)
AAA/ACCT/EXEC(00000017): START protocol reply PASS
AAA/ACCT(00000017): Send START accounting notification to EM successfully
|
Example 4. Telnet Session - Highlighting EXEC Authorization
! Login Authentication, EXEC Authorization and EXEC Accounting succeed for VTY line
AAA/AUTHEN/LOGIN (00000018): Pick method list 'TERMINAL'
AAA/AUTHOR (0x18): Pick method list 'EXEC1'
AAA/AUTHOR/EXEC(00000018): processing AV cmd=
AAA/AUTHOR/EXEC(00000018): processing AV priv-lvl=15
AAA/AUTHOR/EXEC(00000018): Authorization successful
AAA/ACCT/EXEC(00000018): Pick method list 'EXECLOG1'
AAA/ACCT/SETMLIST(00000018): Handle ED000006, mlist 84664930, Name EXECLOG1
Getting session id for EXEC(00000018) : db=83CABEE4
AAA/ACCT(00000018): add common node to avl failed
AAA/ACCT/EXEC(00000018): add, count 2
AAA/ACCT/EVENT/(00000018): EXEC UP
AAA/ACCT/EXEC(00000018): Queueing record is START
AAA/ACCT(00000018): Accouting method=TACACS1 (TACACS+)
AAA/ACCT/EXEC(00000018): START protocol reply PASS
AAA/ACCT(00000018): Send START accounting notification to EM successfully
|
Example 5 illustrates a command authorization session for IOS that is in accordance with the configurations presented in Example 2 and with the command set defined in Figure 2. In this particular case, the command attempt is denied, therefore not producing an accounting record.
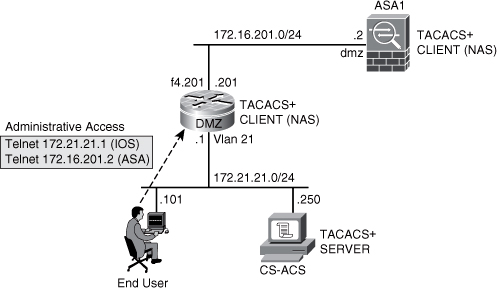
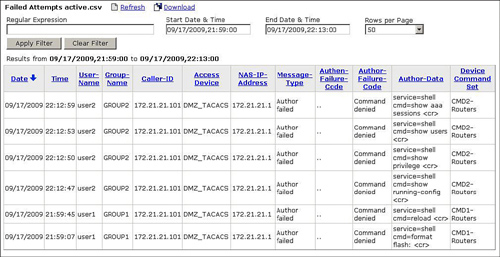
Figure 3 shows a sample Failed Attempts report in CS-ACS for denied commands. The last column of the table displays the Device Command Set that denied the execution of the command.
Example5. Command Authorization Session (Nonauthorized Command)
' Following up EXEC authorization, user2 attempts to execute the "show users" command
! AAA/AUTHOR: auth_need : user= 'user2' ruser= 'DMZ'rem_addr= '172.21.21.101' priv= 1 list= 'CMD1' AUTHOR-TYPE= 'command'
AAA: parse name=tty2 idb type=-1 tty=-1
AAA: name=tty2 flags=0x11 type=5 shelf=0 slot=0 adapter=0 port=2 channel=0
AAA/MEMORY: create_user (0x8465C574) user='user2' ruser='DMZ' ds0=0 port='tty2'
rem_addr='172.21.21.101' authen_type=ASCII service=NONE
priv=1 initial_task_id='0', vrf= (id=0)
tty2 AAA/AUTHOR/CMD(1549841260): Port='tty2' list='CMD1' service=CMD
AAA/AUTHOR/CMD: tty2(1549841260) user='user2'
tty2 AAA/AUTHOR/CMD(1549841260): send AV service=shell
tty2 AAA/AUTHOR/CMD(1549841260): send AV cmd=show
tty2 AAA/AUTHOR/CMD(1549841260): send AV cmd-arg=users
tty2 AAA/AUTHOR/CMD(1549841260): send AV cmd-arg=<cr>
tty2 AAA/AUTHOR/CMD(1549841260): found list "CMD1"
tty2 AAA/AUTHOR/CMD(1549841260): Method=TACACS1 (tacacs+)
AAA/AUTHOR/TAC+: (1549841260): user=user2
AAA/AUTHOR/TAC+: (1549841260): send AV service=shell
AAA/AUTHOR/TAC+: (1549841260): send AV cmd=show
AAA/AUTHOR/TAC+: (1549841260): send AV cmd-arg=users
AAA/AUTHOR/TAC+: (1549841260): send AV cmd-arg=<cr>
TAC+: (1549841260): received author response status = FAIL
AAA/AUTHOR (1549841260): Post authorization status = FAIL
AAA/MEMORY: free_user (0x8465C574) user='user2' ruser='DMZ' port='tty2'
rem_addr='172.21.21.101' authen_type=ASCII service=NONE priv=1 vrf= (id=0)
|
Example 6 illustrates a command authorization session for IOS that is in accordance with the configurations presented in Example 2 and with the command set defined in Figure 1.
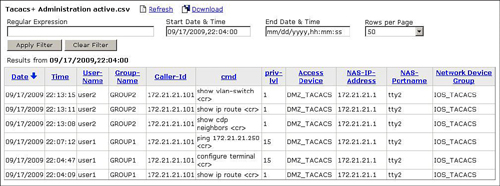
Figure 4 shows a sample TACACS+ Administration report in CS-ACS. An accounting record for the show ip route command of example 6 is shown in this figure.
Example 6. Command Authorization Session (Allowed Command)
! Authorized command is issued by user "user1". Command Accounting uses list "ACCT1"
AAA/AUTHOR: auth_need : user= 'user1' ruser= 'DMZ'rem_addr= '172.21.21.101' priv= 1 list= 'CMD1' AUTHOR-TYPE= 'command'
AAA: parse name=tty2 idb type=-1 tty=-1
AAA: name=tty2 flags=0x11 type=5 shelf=0 slot=0 adapter=0 port=2 channel=0
AAA/MEMORY: create_user (0x84D63A0C) user='user1' ruser='DMZ' ds0=0 port='tty2'
rem_addr='172.21.21.101' authen_type=ASCII service=NONE priv=1 initial_task_id='0', vrf= (id=0)
tty2 AAA/AUTHOR/CMD(3985697951): Port='tty2' list='CMD1' service=CMD
AAA/AUTHOR/CMD: tty2(3985697951) user='user1'
tty2 AAA/AUTHOR/CMD(3985697951): send AV service=shell
tty2 AAA/AUTHOR/CMD(3985697951): send AV cmd=show
tty2 AAA/AUTHOR/CMD(3985697951): send AV cmd-arg=ip
tty2 AAA/AUTHOR/CMD(3985697951): send AV cmd-arg=route
tty2 AAA/AUTHOR/CMD(3985697951): send AV cmd-arg=<cr>
tty2 AAA/AUTHOR/CMD(3985697951): found list "CMD1"
tty2 AAA/AUTHOR/CMD(3985697951): Method=TACACS1 (tacacs+)
AAA/AUTHOR/TAC+: (3985697951): user=user1
AAA/AUTHOR/TAC+: (3985697951): send AV service=shell
AAA/AUTHOR/TAC+: (3985697951): send AV cmd=show
AAA/AUTHOR/TAC+: (3985697951): send AV cmd-arg=ip
AAA/AUTHOR/TAC+: (3985697951): send AV cmd-arg=route
AAA/AUTHOR/TAC+: (3985697951): send AV cmd-arg=<cr>
TAC+: (-309269345): received author response status = PASS_ADD
AAA/AUTHOR (3985697951): Post authorization status = PASS_ADD
AAA/MEMORY: free_user (0x84D63A0C) user='user1' ruser='DMZ' port='tty2'
rem_addr='172.21.21.101' authen_type=ASCII service=NONE priv=1 vrf= (id=0)
AAA/ACCT/259(00000018): Pick method list 'ACCT1'
AAA/ACCT/SETMLIST(00000018): Handle 34000007, mlist 846E3288, Name ACCT1
[ output suppressed]
|
Figure 5
is intended to consolidate the processes of individual command
authorization and accounting that can follow a successful EXEC
authorization. In the start point of the flowchart, assume that the
user has already been authenticated.