6. Using the GPO Technique
Microsoft has created a new Windows Firewall for
Windows 7 that has features you can't access using the older techniques
shown in the previous sections. When you need to access these new
features, you need to use an entirely different access technique that
relies on GPO and a series of rules in place of the techniques used in
the past. The following sections provide an overview of how to use
these newer techniques.
6.1. Configuring the Rule Technique Example
The Rule Technique example performs three tasks.
First, it shows how to enumerate the rules used to configure the
Windows Firewall exceptions and services. You need to be able to
enumerate these rules to find entries that may be helpful to your
application. The same rule configuration applies to ports,
applications, and services, so you don't need to worry about any
special objects when working with the various Windows Firewall
elements. Second, the Rule Technique example shows how to add an
application exception. The same technique works for adding ports or
services as needed. Third, the Rule Technique example shows how to
remove the application exception.
The example begins with a Windows Forms application. You add three buttons: Get Rules (btnGetRules), Add (btnAdd), and Remove (btnRemove). The application also requires use of a list box control, lstRuleList. There isn't any need for special references or using statements. However, the application does require the following constants:
// Entries from ICFTypes.H
// Alternative Profile Type
const Int32 NET_FW_PROFILE2_DOMAIN = 1;
const Int32 NET_FW_PROFILE2_PRIVATE = 2;
const Int32 NET_FW_PROFILE2_PUBLIC = 4;
const Int32 NET_FW_PROFILE2_ALL = 2147483647;
// Protocol
const Int32 NET_FW_IP_PROTOCOL_TCP = 6;
const Int32 NET_FW_IP_PROTOCOL_UDP = 17;
const Int32 NET_FW_IP_PROTOCOL_ICMPv4 = 1;
const Int32 NET_FW_IP_PROTOCOL_ICMPv6 = 58;
// Direction
const Int32 NET_FW_RULE_DIR_IN = 1;
const Int32 NET_FW_RULE_DIR_OUT = 2;
// Action
const Int32 NET_FW_ACTION_BLOCK = 0;
const Int32 NET_FW_ACTION_ALLOW = 1;
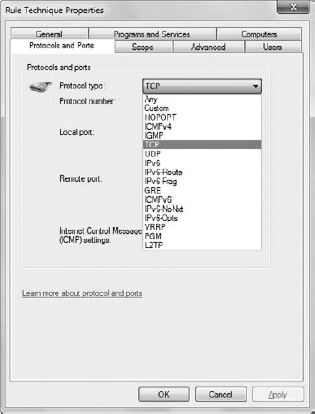
Notice that these constants come from the ICFTypes.H
file. Reviewing this file is helpful when you need other ideas for
working with rules in the Windows Firewall. In this case, you see the
constants for all three profiles and a special constant used when all
three profiles are required by the rule. The list of protocols is a
little short. A rule can employ any of the protocols shown in Figure 9. The problem is that the ICFTypes.H file only documents the TCP and UDP protocols — NET_FW_IP_PROTOCOL_ICMPv4 and NET_FW_IP_PROTOCOL_ICMPv6 are the result of experimentation. All the other constants do appear in the ICFTypes.H file.