2.2. Developing for Security Roles
Role-Based Security asks the question of
whether some entity (a user, the system, a program) is in a particular
role. If it's in that role, the entity can likely access a system
resource or application feature safely. The concept of a role is
different from something more absolute like a group. When you're a
member of a group, you have the same access whether you access the
system from a local machine or the Internet. A role does include the
idea of group membership, but this is membership based on the
environment — the kind of access requested in a given situation from a
specific location. An entity's security role changes, rather than being
absolute. The following sections describe how to check a user's role
based on the evidence presented by the application's current domain.
2.2.1. Configuring the Security Role Example
This example begins with a Windows Forms application. You add a Test button (btnTest). In addition, you need to add the following using statements:
using System.Security.Principal;
using System.Threading;
2.2.2. Creating the Security Role Example Code
It may surprise you to learn how many roles a
particular user fulfills at any given time. The example in this section
obtains the identity of the current user — the one logged in to the
system. It then discovers the roles that the user fulfills. Listing 3 shows the code required for this example.
Example 3. Using the IsInRole() method
private void btnTest_Click(object sender, System.EventArgs e)
{
WindowsPrincipal MyPrincipal; // The role we want to check.
AppDomain MyDomain; // The current domain.
StringBuilder Output; // Example output data.
Array RoleTypes; // Standard role types.
// Set the principal policy for this application.
MyDomain = Thread.GetDomain();
MyDomain.SetPrincipalPolicy(PrincipalPolicy.WindowsPrincipal);
// Get the role and other security information for the current
// user.
MyPrincipal = (WindowsPrincipal)Thread.CurrentPrincipal;
// Get the user name.
Output = new StringBuilder();
Output.Append("Name: " + MyPrincipal.Identity.Name);
// Get the authentication type.
Output.Append("\r\nAuthentication: " +
MyPrincipal.Identity.AuthenticationType);
Output.Append("\r\n\r\nRoles:");
// Create an array of built-in role types.
RoleTypes = Enum.GetValues(typeof(WindowsBuiltInRole));
// Check the user's role.
foreach(WindowsBuiltInRole Role in RoleTypes)
{
// Store the role name.
if (Role.ToString().Length <= 5)
Output.Append("\r\n" + Role.ToString() + ":\t\t");
else
Output.Append("\r\n" + Role.ToString() + ":\t");
// Store the role value.
Output.Append(
MyPrincipal.IsInRole(WindowsBuiltInRole.User).ToString());
}
// Output the result.
MessageBox.Show(Output.ToString(),
"User Role Values",
MessageBoxButtons.OK,
MessageBoxIcon.Information);
}
|
The code begins by obtaining the domain for the current thread. . The program executes in an application domain, and we can
obtain information about that domain. In this case, the code sets the
security policy for this domain equal to the same policy used by
Windows. The application is now executing with the same policy that the
user has when working with Windows. You could theoretically change that
policy depending on conditions such as user location.
Now that the code has set the security policy for the thread, it uses that information to create a WindowsPrincipal object, MyPrincipal.
This object knows all kinds of security information about the user. The
code shows how you can obtain the user name and the method of
authentication used.
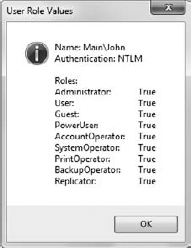
The most important use for MyPrincipal is
to determine which roles the user is in. You probably haven't defined
any roles as part of a CASPol configuration process, so the example
uses the WindowsBuiltInRole enumeration to check the standard types. If the user is in the requested role, the IsInRole() method returns true. This value is converted to a string and placed in Output. Figure 1
shows typical output from this example. Of course, the results will
change when you run the program on your system because the dialog box
will reflect your name and rights.
The important concept to take away from
this example is that Role-Based Security performs a task similar to
standard Windows security, but using a different and more flexible
technique. Because of the differences between Windows security and
Role-Based Security, you may need to rely on the groups provided by NT
security, especially when working in an environment that has a mix of
managed and unmanaged code.