Integration, management tools &
usage policies
Cloud computing can be a great solution for
companies looking to ease the burdens on their internal infrastructure or to
add a little extra capacity when necessary. But the cloud can also come with
control issues that may make you question whether or not it was worth it to
invest in the technology. Dave Bartoletti, senior analyst with Forrester
Research (www.forrester.com), says the
private cloud isn’t as big of an offender because the “ownership still stays
within your four walls.” But the public cloud, in particular, he says, is
susceptible to loss of control because “if you’re doing something in a public
cloud sphere and starting out there, it’s a fundamental shift in how you’ve
done business.”

The
cloud can also come with control issues that may make you question whether or
not it was worth it to invest in the technology
Bartoletti says enterprises will experiment
with the cloud using SaaS (software as a service) solutions, but the simple
fact that SaaS involves off-site computing can cause companies to feel a loss
of control almost immediately. Cloud computing also brings security issues to
the forefront, because businesses may feel like they are “losing control of
ownership of the data,” says Bartoletti, while the IT team may feel as though
they are “losing control over how technology decisions are made in general.”
No company wants to feel like they have
little or no control over a solution or service, which is why it’s important to
do research up front. But if you have already implemented a cloud environment
and want to tighten the reins, it isn’t too late. You can still pin-point where
any issues originate and institute new solutions or policies that will help you
regain control.
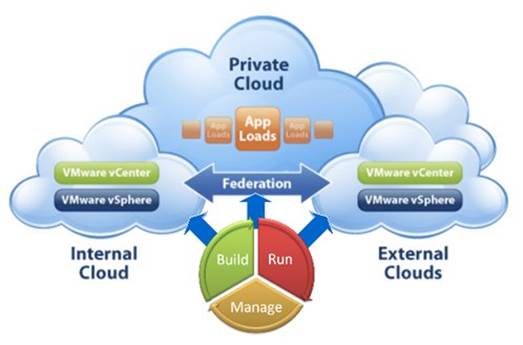
Improve your overall cloud integration
John Sloan, lead research analyst with
Info-Tech Research Group (www.infotech.com),
would add company-wide integration to the list of factors that lead to loss of
control. It may seem like a great idea at first to take advantage of the cloud
through data and application migration. But if you don’t plan ahead, you may
end up “juggling a bunch of islands” and experiencing “poor integration between
your internal resources and the cloud,” Sloan says.

When
it comes to data integration, “you may have data in a cloud service”
With application integration, you may move
some apps to the cloud and leave others within the organization, possibly as
part of a hybrid cloud environment. Then, you may realize down the road that
you need these two apps to communicate with one another in order for them to
work properly. You’ve already paid for the capacity you need to house that
application in the cloud, so you have to decide whether to pull it back, move
your other app to the cloud, or figure out a way to patch them together after
the fact. When it comes to data integration, “you may have data in a cloud
service” as well as “related data internally, so now you have two silos of
data,” says Sloan. Your data then becomes fragmented and it’s difficult to know
which one is your “single version of the truth,” he says.
The last piece of integration that can
cause problems revolves around identity and access management. Sloan uses the
example of an employee having separate sign-on credentials for an internal
application and another housed in the cloud. If that employee leaves and you
remove his access to the internal app, he may still have access to the
cloud-based solution. This type of situation can open the gates to troubling
security issues and leave your company vulnerable to data loss or theft.
The
cloud-based solution
The best way to prevent these issues is to
look at your internal systems and determine how they will integrate with the
cloud services of a third-party provider. For data and application integration,
you have to make sure they can communicate across environments and fully
interact with one another. And for identity and access management, you should
set up an integrated access management solution that creates one username and
password for every application. But you also need to speak to the service
provider to make sure that your access system will integrate well with the
vendor’s existing management tools.