2.3.3 Restricted Groups (Computer Configuration Only)
This
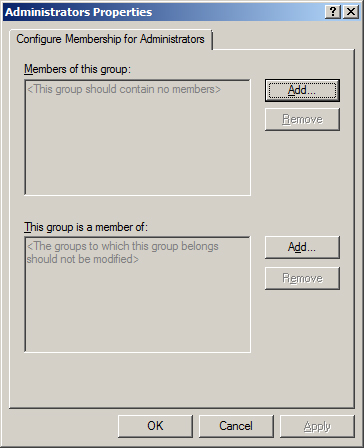
setting allows you to centralize the group membership of both groups
that reside in Active Directory and those that live locally in the
Security Accounts Manager (SAM) on each computer, referred to as local
groups. The setting allows you to control group membership, which
includes both user accounts and group accounts. You can also control
the groups in which a specified group has membership. Both options are
shown in Figure 4.
Warning
Restricted
Groups is a delete-and-replace policy. This means that if you define a
list of user and group accounts to have membership in a specified
group, the existing group members will first be deleted and replaced
with the user and group accounts that you define in the policy. |
Note
If
you want to control the membership of local groups without having the
delete-and-replace behavior of Restricted Groups, consider using Group
Policy Local Users and Groups. |
2.3.4 System Services (Computer Configuration Only)
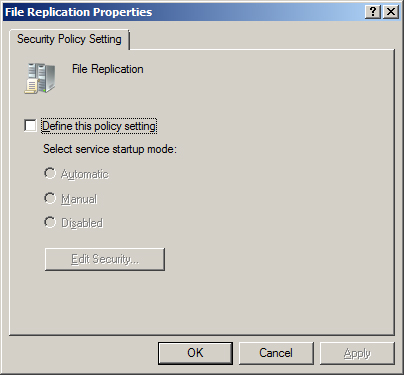
This
policy allows you to control certain aspects of services that reside on
the target computer. The settings available in this policy include the
ability to control the following aspects of services (also shown in Figure 5):
Note
To control more details of services that are running on target computers, you can use Group Policy Services. |
2.3.5 Registry (Computer Configuration Only)
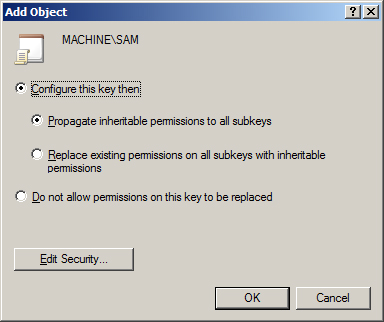
This
policy is designed to control permissions on registry keys. You can
control the full array of NTFS permissions, including advanced
permissions, auditing, and ownership of the objects configured in the
policy. After the policy is configured, you have the option of
controlling whether the permissions will propagate down through the
subkeys in the registry or only apply to the registry key defined, as
shown in Figure 6.
Warning
Application
of permissions to registry keys can be resource intensive and cause
delayed computer start-up. You should use this policy only when
absolutely necessary and only after testing to ensure that the
performance of the start-up is satisfactory for your production
environment. |