Find and kill the threats you don’t
even know are there
Key points
·
Computers can be infected even if they have
antivirus software installed
·
Malware infections are not always easy to spot,
so run regular scans
·
Removing some types of infection can require
special measures
·
You may need to repair parts of Windows after
removing malware
It’s easy to assume that antivirus software
makes your computer invulnerable to infection but don’t kid yourself. The
catch-all term for viruses, spyware, Trojans and other malicious software is
malware and it is constantly evolving.
Find
and kill the threats you don’t even know are there
While good security software will adapt to
combat new risks and ever-changing threats, no product is 100 per cent
effective. In other words, your computer, smartphone or tablet could be
infected right now.
In this project, we will explain how to
check your device for invaders, and then how to remove them and repair any
damage they may have left behind.
Be alert to threats
In an ideal world, security software will
automatically block and flag up – all attempts to infect a computer. But
malicious software creators never stop working on ways to evade detection.
There is also an element of uncertainty over what constitutes infection, so
some suspect programs (sometimes called ‘potentially unwanted programs’ or
Pups) are flagged as dangerous by one security tool, but ignored by another.
The behavior of your computer or device can
alert you to the presence of malware. You may be unable to launch or update an
existing security program, for example, or you may find yourself blocked from
accessing certain tools, or discover that attempts to access security websites
result in a redirection to another web page. You may even see pop-up messages
claiming that you are infected – though clicking fake warnings may actually
lead to an infection.
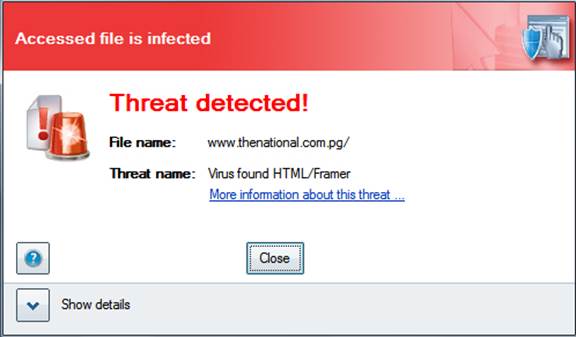
A
malfunctioning security tool is a tell-tale sign that your computer has been
infected with some kind of malware
While some malicious software exhibits
these signs, other infections stay hidden, providing no indication that
anything is wrong. Meanwhile, they may be silently stealing your personal
information. That is why it is important to perform regular checks on your
computer, even if everything appears to be OK.
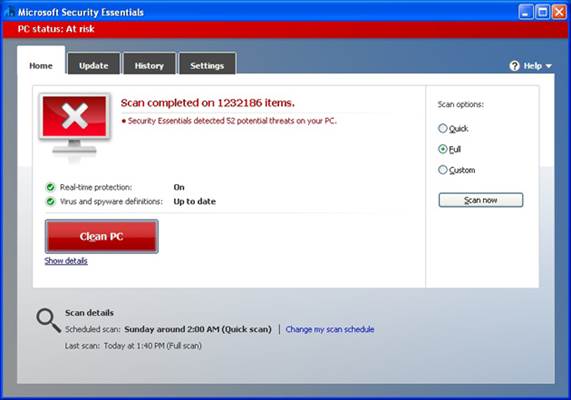
First, open your existing security tool.
Check that it is fully up to date and then perform a full scan – it may find an
infection that bypassed its ‘real-time’ (live) protection. Let it clean up the
infection, restart the computer and scan again to see if it has removed it.
Whether or not the security program finds
and hopefully removes – any evidence of infection, seek out a second opinion.
This can be done using a free scan and remove tool designed to work in
conjunction with antivirus software. One of the best is Malwarebytes
Anti-Malware, which often finds infections other tools can’ t. Download and
install it free, clear the ‘Enable free trial…’ box at the end of the setup
wizard (because the full version of the software isn’t required) and click
Finish. Allow the program to update itself then select ‘Perform full scan’ and
click the Scan button. Make sure all hard disks and USB drives are selected
before clicking Scan again. If an infection is found, read the Remove malware
from your computer section below.
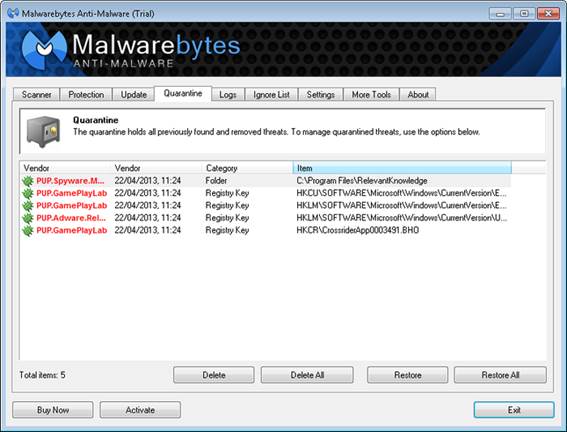
Malwarebytes
Anti-Malware can spot certain infections that other security tools miss
If nothing is found, but you are convinced
something is wrong, try scanning with Norton Power Eraser (www.snipca.com) free tool that does not
require installation. After completing a scan, a list of bad or unknown files
will be displayed. Click a file name to view a ‘ reputation’ rating from
Norton’ s community of users, or click the Cloud Scan button to have the file
analyzed over the internet.
Norton Power Eraser uses what it describes
as ‘aggressive methods’ to detect threats. This means it may root out harder-to-find
infections, but may also mistakenly identify legitimate programs as dangerous.
It will not remove important system files or files marked as ‘unknown’ , but
you may find certain programs no longer work correctly after it has cleaned
your computer – so use only when absolutely necessary.
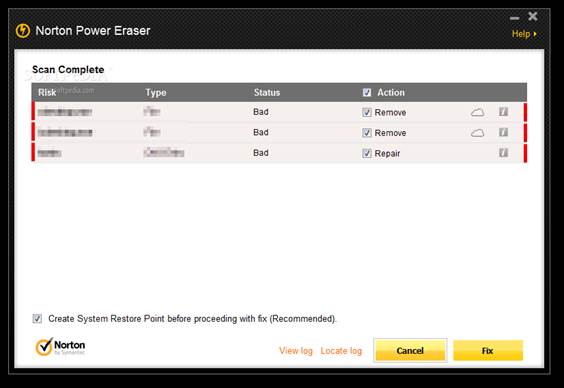
Norton
Power Eraser is a free tool that can remove troublesome malware from your PC
If no infections are found, but you are
still suspicious, go further. Perform a quick security audit of all running
programs and processes using a free tool called System Explorer. Download it by
visiting www.snipca.com and clicking the ‘Download System Explorer Portable’
link. Right-click the downloaded Zip file and choose Extract All to save it
into its own folder. Once done, open the program folder and double-click the
SystemExplorer.exe file to launch it.
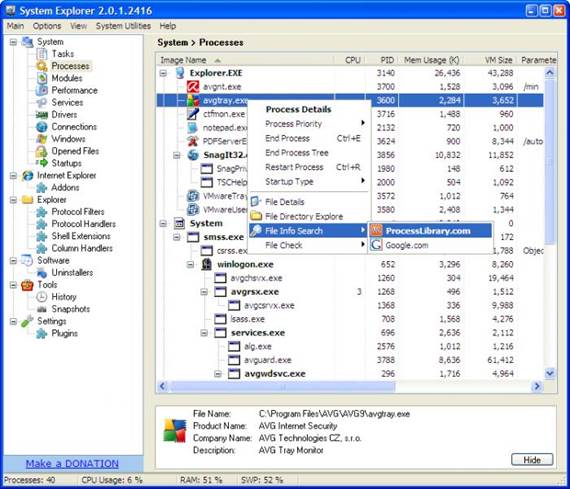
When the System Explorer window opens,
click the ‘Start As Admin’ button if it appears in a yellow bar at the top of
the program window. Next, switch to the Processes tab and click the Security
Scan button followed by ‘Start security check’. All running programs will be
checked against System Explorer’s security database for potential threats.
Unsafe entries will be clearly flagged, but also be wary of programs marked
with a blue shield containing a question mark, which means they are unknown.
System
Explorer lets you manually check for suspicious-looking programs and processes
taking place on your computer
Select an unknown entry to reveal more
about it at the bottom of the System Explorer window. Be wary of any entries
that appear as gibberish in the Product Name, Company Name and Description
fields – this is a tell-tale sign of malware.
Clicking the Details link next to a name
opens the System Explorer online database, which will attempt to identify the
target. You can also right-click the entry and choose File Info Search followed
by Google Search to see if a more general web search turns up any additional
information about the file in question.