Microsoft has enhanced many of the core
network features with the release of Windows Server 2008 and 2008 R2.
Windows Server 2008 R2 also comes with some newly added features that
deliver greater security, reliability, and a better end-user experience.
Network and Sharing Center
The Network and Sharing Center is the new central
console to configure and manage network settings in Windows Server 2008
R1, Windows Vista, Windows Server 2008 R2, and Windows 7. It includes
options that allow you to manage network adapters, enable or disable
file sharing, change network location settings, and troubleshoot
connection problems.
Redesigned TCP/IP Network Stack
Windows
Server 2008 R2 includes what Microsoft calls “The Next Generation
TCP/IP Stack.” During the development of Windows Server 2008, Microsoft
chose to completely redesign the TCP/IP stack to improve performance,
add new features for IP version 4 (IPv4), and to include support for IP
version 6 (IPv6). The redesign includes new features such as:
Fail back support for default gateways
—Windows Server 2003 and Windows XP provided the ability to add
multiple default gateways for redundancy. If one gateway became
unreachable, Windows could fail over to a backup default gateway.
Windows Server 2003 and Windows XP did not, however, provide an
automatic check of the unreachable gateway to determine when it came
back online. An administrator would have to manually fail back the
computer to the original gateway. Windows Server 2008 introduces the
ability to have the computer perform regular “checks” of a dead or
unreachable gateway. Once the gateway becomes reachable again, the
computer will fail back to the original gateway automatically.
TCP chimney off-load
—As networks have advanced over the years, so has the amount of
processing required to manage and maintain network connections.
Significant increases in CPU utilization have been seen when performing
large data transfers, such as those seen during backups and on iSCSI
Storage Area Network (SAN) connections. Typically, this increased
utilization is seen on 1-gigabit and 10-gigabit connection speeds. To
address this issue, Microsoft developed the ability to off-load all TCP
connection processing to a TCP Off-load Engine (TOE) card. TOE cards are
special network adapters built specifically to off-load TCP traffic
from the computer’s main CPU. This allows the TOE card to carry the
additional processing load, freeing up the computer’s primary CPU for
other processing requests.
Network Diagnostics Framework
—The Network Diagnostics Framework helps to locate and diagnose network
connectivity problems and in many cases it will take the end-user
through a series of steps to find the cause of connectivity loss and fix
it. It can help resolve several common issues, such as IP address
conflicts, dead default gateways, stopped DHCP client services, or
disconnected media.
DNS enhancements
Windows Server 2008 now includes new DNS features
including IPv6 support and the GlobalNames zone. The GlobalNames zone
provides single-label name resolution without the need for a dedicated
Windows Internet Naming System (WINS) deployment.
|
The Windows Internet Naming System (WINS)
For those who are unfamiliar with WINS; it was
originally developed to support name resolution over Windows networks
separated by wide area network (WAN) links. WINS provided name
resolution of NETBIOS names before DNS became the primary technology
used for computer name resolution. Though not as prevalent, WINS can be
seen on a lot of Windows networks today supporting legacy NETBIOS based
applications. The new GlobalNames zone is Microsoft’s solution to help
traditional WINS deployments to move to DNS technologies for name
resolution.
|
Policy-based QoS
Traditionally, Quality of Service (QoS) has been set
up to throttle or prioritize traffic between network switches and
routers; however, Policy-based QoS in the Windows Server 2008 R2 allows
administrators to deploy these features to servers and desktops. This
ability opens the door to more enhanced network bandwidth management.
SMB 2.0
Server Message Block (SMB) 1.0 was originally
developed for sharing files in Windows operating systems. SMB 2.0 was
released as part of the Windows Server 2008 R1 and Vista operating
systems, and remains in 2008 R2 and Windows 7 today. SMB 2.0 has greatly
been enhanced to increase the performance of SMB file traffic. Copying
files between two SMB 2.0 capable systems occurs at much greater speeds
as those seen using SMB 1.0. Several enhancements to SMB, such as the
ability to perform multiple operations at the same time, make it more
efficient. SMB 1.0 would perform only one operation and wait for a
response before moving to the next. SMB 2.0 can issue two to three
operations or more making it more efficient and faster in the eyes of
the end-user. An additional benefit to SMB 2.0 is that it also has the
ability to sustain a file transfer even if a brief network disconnect
occurs. Have you ever been in the middle of a very large file transfer,
and suddenly the network connection briefly drops? Do you remember the
frustration of having to start the file transfer all over again? SMB 2.0
can automatically maintain the file transfer during that brief
connectivity drop and continue copying files after the connectivity is
restored. SMB 2.0 is available in Windows Server 2008, Windows Server 2008 R2, Windows Vista, and Windows 7 operating systems.
You may be wondering, “What happens if I transfer a
file between a SMB 2.0 capable system and a SMB 1.0 capable system, such
as Windows XP?” In this situation, the file transfer process will use
the 1.0 version of SMB providing backward compatibility to the older
operating system.
Windows Firewall
Microsoft first included the Windows Firewall in
Windows Server 2003 and Windows XP. The Windows Firewall in Windows
Server 2003 provides the ability to “lock down” certain ports and
applications resulting in a greater level of security not only for
applications but also for the server system as a whole. Though the
Windows Firewall was a great addition from a security standpoint, it did
have a few shortcomings. The firewall was cumbersome to configure at
times, especially for less experienced Windows administrators. It also
filtered only traffic incoming to the server, so all outbound
connections were allowed by default.
Windows Server 2008 R1 and R2 include a new version
of the Windows Firewall with a much improved administrative experience.
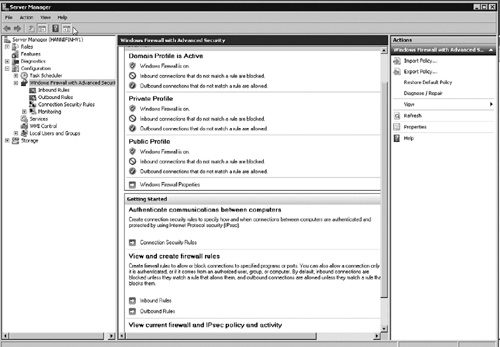
The Windows Firewall has been configured using a console built into the
Server Manager interface (see Figure 1).
The firewall now has the ability to filter both inbound and outbound
connections. Additionally, Windows Server 2008 R2 services and some
applications will automatically create necessary firewall rules to
ensure that they can communicate properly with the network.
Additionally, the firewall has APIs which allow application developers
to publish their own exception requirements to the firewall during
installation of their given application. The firewall can also be
changed on a per-network interface, opposed to a particular rule or
configuration applying to all interfaces.
IPv6 support
IPv6 is the next generation IP protocol designed to
eventually replace IPv4. Windows Server 2008 R2 natively supports both
IPv6 and IPv4 out-of-box. Both are installed and enabled by default in
Windows Server 2008 R2. As with most technologies, support for IPv4 will
continue to be required for several years but in the near future IPv6
may very well become the IP standard. To assist organizations in moving
to IPv6, Windows Server 2008 R2 includes several standards-based IPv4 to
IPv6 transition technologies such as Teredo, 6to4, and IP-HTTPS.
Network awareness
Windows Server 2008 R2 has the ability to sense
changes in network connectivity, whether this is connecting and
disconnecting on the same network or plugging into a different network
altogether. The Network Awareness APIs in Windows Server 2008 R2 allow
developers to write applications that can rely on this network state
change monitoring and react when changes occur. For example, an
application may require a connection to the corporate network for
certain features to function properly. Using Network Awareness APIs, the
developer could instruct the application to display only those features
when it detects that the computer is connected to the corporate LAN.
Network Access Protection
Network
Access Protection (NAP), originally released in Windows Server 2008 R1,
is a technology that ensures that computers on your network comply with
IT health policies. NAP makes sure that client computers have current
operating system updates installed, antivirus software running, and
custom configurations related to ensuring that the client is compliant
with corporate IT policies. NAP restricts the computer’s network access
until it verifies whether the client is in compliance. If the computer
is found not to be in compliance with set policies, the end-user can be
offered a way to remediate the problem and then granted full network
access.
DirectAccess
DirectAccess is a new feature introduced in Windows
Server 2008 R2 and Windows 7. DirectAccess provides end-users with
constant, secure connectivity to the corporate network anytime an
Internet connection is available and without the need for traditional
Virtual Private Network (VPN) client software installed. This connection
not only gives end-users easy access to the company network, but also
provides systems such as configuration management and software
distribution server’s access to the PC. This is a Win-Win feature for
end-users and IT departments alike. DirectAccess is accomplished by
creating a secure tunnel between the Windows 7 workstation and the
Windows Server 2008 R2 network.
Exploring Network and Sharing Center
The Network and Sharing Center is the new central
console for managing TCP/IP network connectivity and features, such as
Windows File sharing. The new Network and Sharing Center is the
“one-stop shop” to view, manage, and troubleshoot your network
connectivity in Windows Server 2008 R2.
The Network and Sharing Center can be accessed via a few methods. It can be accessed via the control panel under the Network and Internet section (see Figure 2),
by right clicking on a network connection in the system tray or by
right clicking on the Network option in the Start menu and choosing
properties.
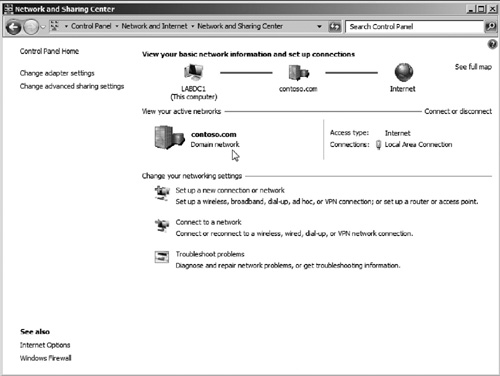
You will notice several options presented when you
first open the Network and Sharing Center. In the top middle section of
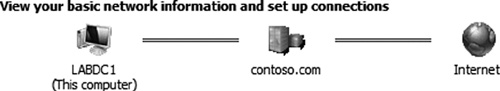
the window, you will see a basic connectivity map as seen in Figure 3. The simple map provides a visual representation of network connectivity from the operating system’s perspective.
This includes the ability to access a local network and the Internet.
If the server fails to connect to either of these, the map will display
the problem area with a red disconnected status. The connectivity map
may vary slightly depending on what type of network your computer is
connected to.
Below
the connectivity map, you will see a section that lists the name and
type of the network you are connected to along with the media (wired or
wireless) providing the connection (see Figure 4).
By clicking on any connected media type, you can view the status of the
connection as well as make configuration changes, such as disabling the
network adapter or setting the IP address.

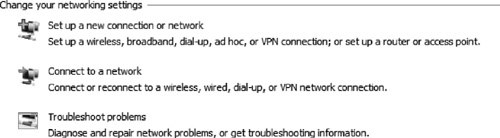
Moving down the window, you will see a section named “Change your network settings” (see Figure 5). Here you can change various aspects of your network connection, including setting up a new connection to a remote network via VPN or dial-up, connecting to an existing network, or diagnosing current network problems.
The left-hand section of the Network Sharing Center provides links to the following network and configuration settings:
Change adapter settings
—This link opens the network connections window. Here you can perform
tasks such as disabling/enabling network adapters, and assigning IP
addresses and protocols to those adapters.
Change advanced sharing settings —This link takes you to the window that allows you to turn network sharing, network discovery, and public folder sharing on and off. These settings can be turned on or off for each network profile individually.
|
See Also Links
Throughout the configuration windows in Windows
Server 2008 R2, Microsoft has embedded “See Also Links.” The links take
you to the configuration and management consoles similar to the current
console where the links appear.
|
Network profiles
Windows Server 2008 and Windows Vista introduced a
new way to manage network configuration based upon the network that the
computer is connected to. For example, you can configure the computer to
open Windows Firewall ports for Remote Desktop connectivity while
connected to the corporate network and to disable the ports when
connected to a public network. Windows Server 2008 R2 includes the
following network profile types:
Domain —The
domain network profile is used when the computer is connected to the
network that hosts the domain that it is a member of. For example, if a
computer is a member of the Contoso.com domain, the domain network profile will be used when that computer connects to the network that hosts the Contoso.com domain.
Private
—The private network profile is used when connecting the computer to a
trusted network that does not host the domain in which the computer is
joined. This profile is less restrictive than the public profile and
thus should only be used on trusted networks, such as a home network or
in situations where the computer is connected to the corporate network,
but not joined to a Windows domain.
Public
—The public network profile should be used when connecting the computer
to a non-trusted network, such as a public Wi-Fi hotspot. This profile
is much more restrictive toward other network computers and devices.
You will more than likely not be moving your
production servers between various networks on a regular basis.
However, it is important that you understand how Network Profiles impact
on the operating system’s configuration to ensure that proper settings
are applied for your given network scenario. For example, if you open a
Windows Firewall port for the private profile and the computer is using
the domain profile, then the firewall change that you made will have no
impact on the computer’s current configuration.