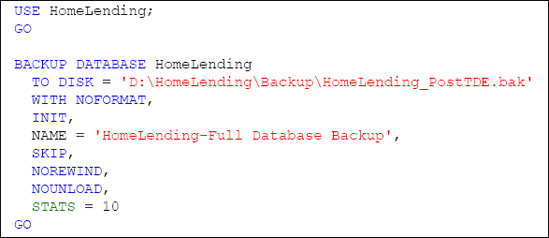
5.2 Verification through Backup and Recovery
Another method of verifying the success of a TDE
implementation is to perform a backup of the database, after TDE has
been enabled, as shown in Listing 9. When doing so, make sure not to overwrite the backup file that was created prior to implementing TDE.
The next step is to compare the contents of the
pre-TDE and post-TDE backup files, by opening both files up in a simple
text editor such as Notepad, Wordpad or Textpad. We can perform a
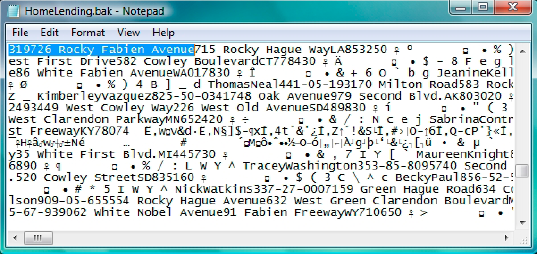
search within the pre-TDE backup file for the plain text of a known
sensitive data value. For example, we will search for the value of "319726 Rocky Fabien Avenue" which is contained in the Borrower_Address table in the HomeLending database.
This search reveals the searched value in plain text, as shown in Figure 2.
In addition, if you were to manually scan through the backup file, you
would find that the metadata of our database objects, such as tables,
views, stored procedures and user defined functions are revealed in
plain text.
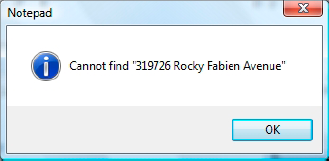
The same search on our post-TDE backup file will result in the message box shown in Figure 3,
stating that it cannot find the requested value. This is because the
entire backup file, including the metadata of our database objects, has
been encrypted and no longer contains any plain text values.
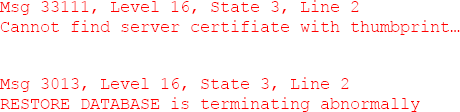
One final test in regard to the backup file is to
attempt to restore the post-TDE backup file onto a different instance
than the one in which the HomeLending database resides, using the RESTORE DATABASE command, as shown in Listing 10.
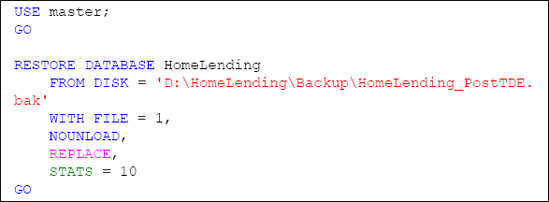
This attempt will return an error message that states that the certificate at the Master database level, in which the HomeLending database encryption key is protected, does not exist; therefore the attempt will fail.
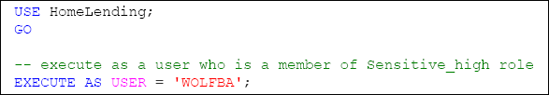
5.3 Using EXECUTE AS
Finally, we can perform a test to determine that the data that is contained within the encrypted HomeLending database files can be read by valid users of the database, as shown in Listing 11. We use EXECUTEASUSER to impersonate various users within the database and test their ability to access the encrypted data. The use of REVERT terminates the impersonation and returns us to our original user account.
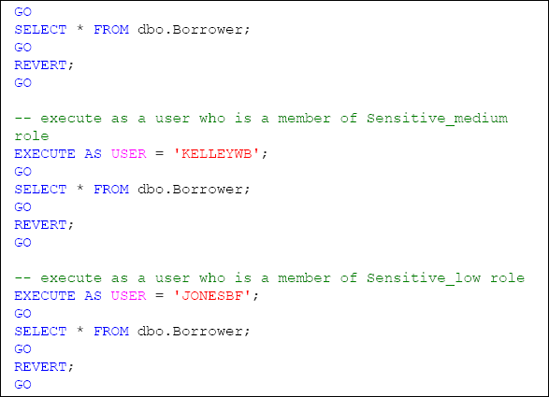
Each query in the above script successfully returns the contents of the Borrower table within the HomeLending
database. This demonstrates that the automatic decryption is
functioning as expected, and verifies that permissions to the
appropriate database objects are not affected.
Please note that if the exercises for implementing cell-level encryption, have been completed within the same database that is being used in the TDE exercises, the query in Listing 11 will fail since permissions to all tables were denied to the Sensitive_high, Sensitive_medium and Sensitive_low database roles. This can be overcome by granting SELECT permissions to these database roles to the Borrower table.